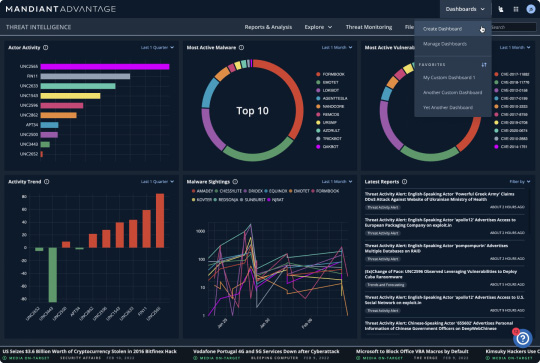
Take decisive action with industry-leading intelligence

Empower your team with Mandiant's uniquely dynamic view of the attack lifecycle. Combine machine, adversary and operational cyber threat intelligence to understand and defend against relevant threats.
300+
Threat actors being tracked
500+
Researchers and analysts
30+
Languages covered
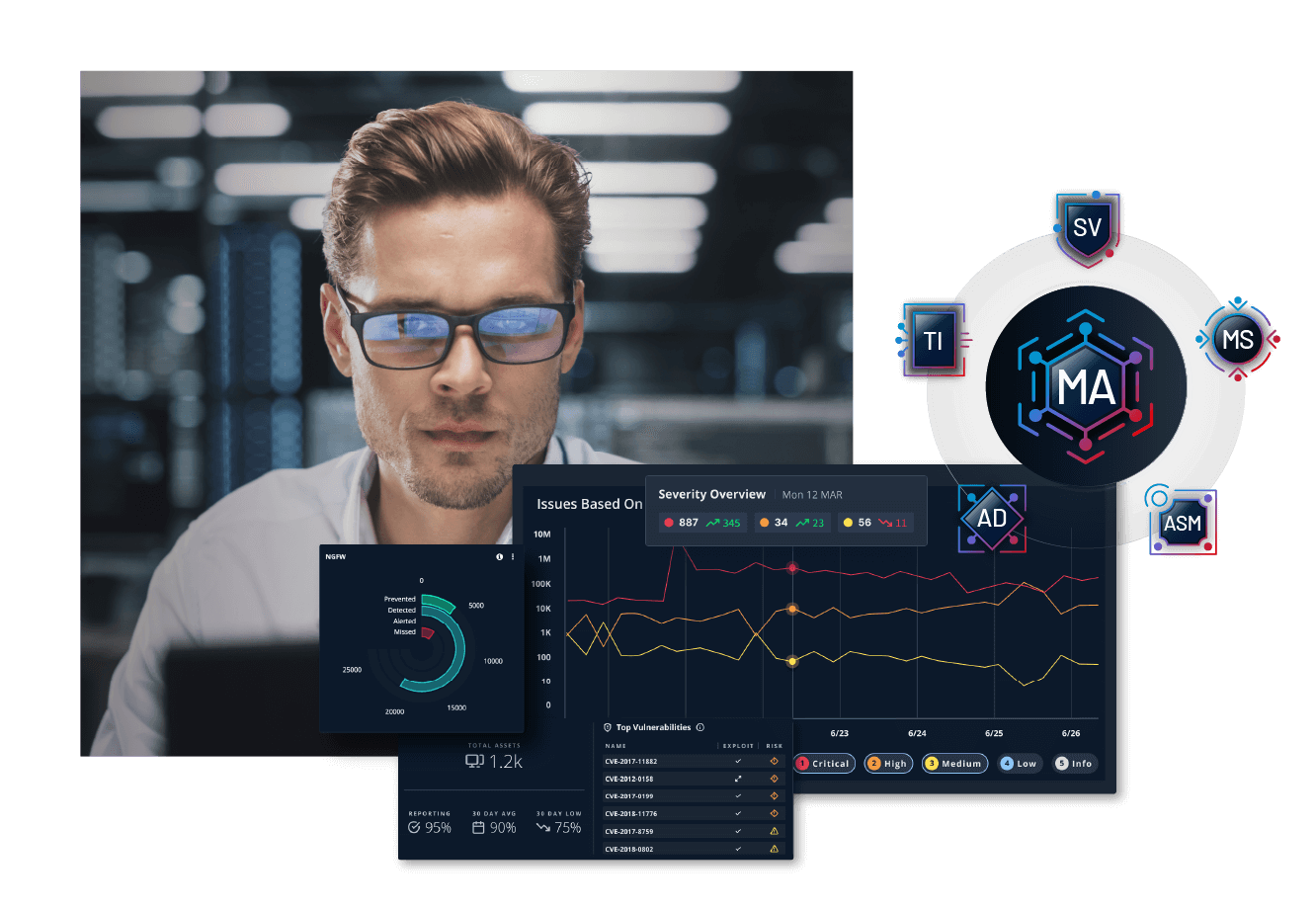
The power of Mandiant in a single platform

The Advantage Platform allows you to automate Mandiant expertise and intelligence so you can prioritize effort and increase capacity to detect and respond faster to attacks - think of it as a virtual extension of your team.
7.6 billion+
Analyst hours saved per year through expert automation

Maximize security effectiveness with unparalleled expertise

Apply the experience and knowledge of leading threat researchers, reverse engineers, intelligence analysts and incident responders defending organizations of all sizes at the front lines of cyber conflict since 2004.
17+ years
Investigative experience
200k+ hours
Responding to attacks / year
1k+
Engagements per year

Protect and Defend with Mandiant Experts

Get the expertise you need when you join forces with Mandiant's premier MDR service. Managed Defense hunts for hidden actors, investigates incidents and provides swift, decisive response.
99%
Resolutions without incident response
< 5 minutes
Average time from alert to triage

"I knew there was a passion and a drive behind Mandiant to provide a really strong understanding of the security landscape and to help us find ways to be proactive."


Insights into Today's Top Cyber Trends and Attacks

Mandiant's annual report provides an inside look at the evolving cyber threat landscape. Explore threat intelligence analysis of global incident response investigations, high-impact attacks, and remediation.