
- MANDIANT SOLUTIONS
Ransomware Protection
Ransomware and multifaceted extortion have become top cyber security threats for organizations of all shapes and sizes.

Defend Against the Attackers’ Top Choice for Multifaceted Extortion
Ransomware attackers have intensified their attack campaigns by threatening critical infrastructure shutdowns, risking public health and safety, diverting vital public resources, disrupting educational institutions, and impacting data privacy.
Anatomy of a Targeted Ransomware Attack
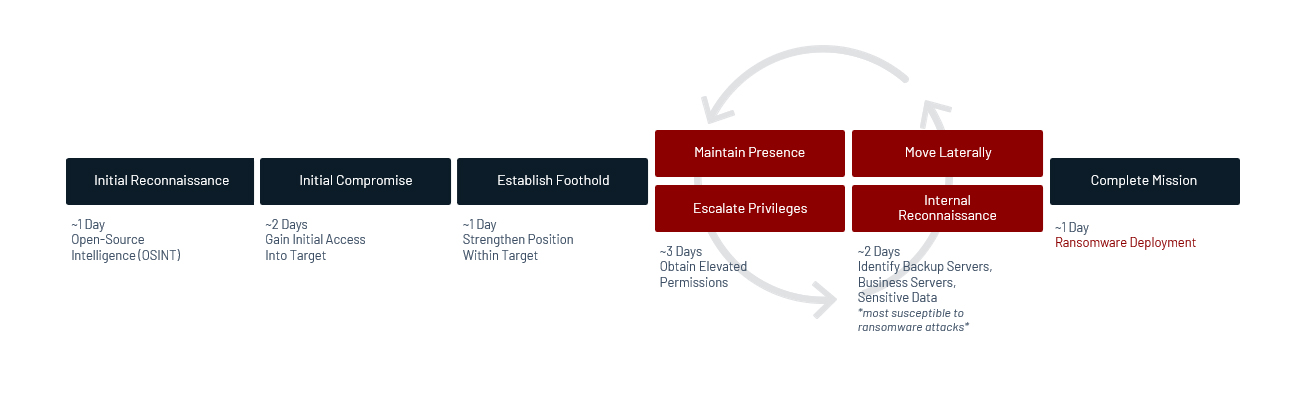
How Mandiant Helps Address Ransomware:
Ideally, every organization should strive to catch a ransomware attack at its earliest stages to prevent deployment. Early detection of the intrusion allows an organization to accelerate their response, minimize its impact and swiftly resume business operations. Security conscious organizations know that the best ransomware defense is ransomware preparedness.
Mandiant has the unique ability to find the intrusions that precede ransomware deployment quickly and at scale.

Ransomware Preparedness
Ready your cyber defenses against ransomware and multifaceted extortion campaigns. Mandiant can help you prepare your specific environment with the Mandiant Advantage platform and services, including threat intelligence, intelligence-led validation and security program assessments.
Assessing and mitigating your organization’s ransomware risks and understanding your team’s ransomware response capabilities can help you prevail against ransomware attacks. The Mandiant Ransomware Defense Assessment evaluates your organization’s ability to detect, contain and remediate ransomware within your specific environment—before it cripples your operations. The service includes three core evaluations in addition to other offerings for engagement enhancements such as the Ransomware Disaster Recovery Architecture Review.

Ransomware Prevention
Identify the activity that precedes ransomware deployment and activate mitigation strategies to avoid a major ransomware and multifaceted extortion incident.
With Mandiant Advantage, response readiness services and on-demand access to Mandiant cyber defense experts, security teams can identify active and past compromises quickly and stop attackers before they cause damage to their organization. Security teams get an early knowledge advantage through automated modules that identify critical indicators of compromise (IOCs). Managed detection and response services provide specialized expertise, such as integration of attacker research to detect malicious activity faster and the effective prioritization of mitigation efforts.

Ransomware Response
Reduce the impact of ransomware and multifaceted extortion attacks with swift and decisive action.
Mandiant provides access to incident response experts so you can rapidly and effectively respond to ransomware and multifaceted extortion attacks. These specialists complete in-depth attack analysis, perform crisis management across the full attack lifecycle and help you recover your business operations after a breach.
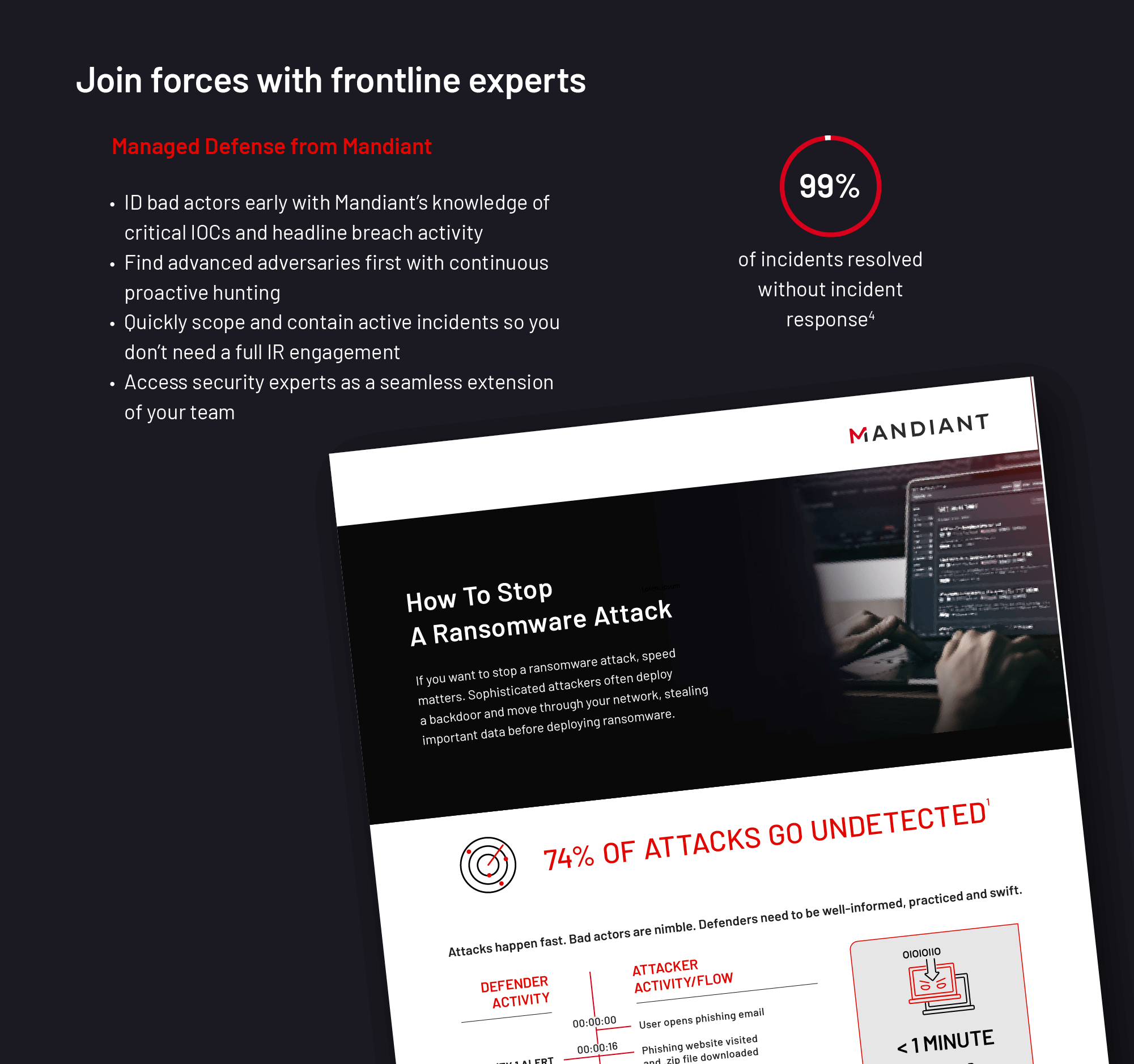
If you want to stop a ransomware attack, speed matters
Defenders need to be well-informed, practiced and swift. See what can happen in the short time a bad actor dwells in your network before it deploys ransomware and achieves its goal.
Ransomware Protection and Containment Strategies
In our latest report, we discuss steps organizations can proactively take to harden their environment to prevent the downstream impact of a ransomware event.
Linux Endpoint Hardening to Protect Against Malware and Destructive Attacks
This paper provides recommendations to protect Linux endpoints from adversarial abuse.
Keeping up with Conti: Tactics Techniques and Procedures Associated with CONTI Ransomware Deployment
Determining your Cyber Risk with Repurposed Ransomware
The use of real attacks—the emulation of native binary code—is critical in testing the effectiveness of security controls.Three Mandiant capabilities enable safe and successful testing with real ransomware attacks.
Multifaceted Extortion: The Evolution of Ransomware
Our latest e-book charters the evolution of ransomware to multifaceted extortion, highlighting critical differences between the two from tactics to consequences.
Infographic: See the Four-Year Growth of Multifaceted Extortion Attacks
Ransomware Protection FAQ
A ransomware solution is combination of technology, services, expertise and intelligence that allows an organization to better recognize and prevent or respond to a ransomware attack in its earliest stages.
- In some cases, yes. Through threat intelligence, ransomware repurpose capabilities and automated validation infrastructure – leaders can determine their security controls can prevent their data from being encrypted by ransomware.
- Organizations can rely on a MDR service with dedicated cyber experts to monitor systems to investigate and quickly and effectively respond to disparate alerts.
No. Multifaceted extortion blends the impact of a data breach with the already painful impact of ransomware. Multifaceted extortion involves multiple attack points, including ransomware encryption, data theft and public “naming and shaming” of the victim organizations, all of which present a more profound risk to organizations.
In a cyber attack, extortion tactics are means by which an attacker may pressure victims to be pay the ransom fee. Cyber extortion tactics include shaming of the victims to regulators, media and customers, as well as DDoS campaigns, data theft and encryption.