Accelerate your digital transformation with the industry’s most trusted cloud.
Google Cloud Trust Center

Get the latest information on Google Cloud’s security, privacy, compliance, and operational health at our Trust Center.

Google Cloud Security Foundations blueprint

Explore Google Cloud’s Security Foundations Blueprint for a simpler path to protecting your cloud assets.

Forrester names Google a Leader in The Forrester Wave™: Infrastructure-As-A-Service Platform Native Security Q2 2023

In this report, Forrester evaluates the native platform security capabilities of Infrastructure as a Service (IaaS) providers, shows how they measure up, and helps professionals make the right choice.
Google Cloud Solutions Center

Get recommendations for Google Cloud solutions and activities to support your solution adoption journey.

Casestudy: How Iron Mountain uses Assured Workloads to serve our customers’ compliance needs

Businesses need the right information to make decisions that lead to successful outcomes.

Developing the Right Security Strategy When Using Multiple Cloud Service Providers

Optimize Protection of Cloud Applications and Resources.

Protecting Your 5G Revenue Stream in the Cloud

Communications service providers (CSPs), like any other business in every other industry, are increasingly transitioning their operations to the cloud to gain advantages in speed, cost and scale, and to expand their reach to customers and business partners alike.
Mitigate threats, reduce risk and get back to business with the help of Mandiant experts.


Mandiant Executive Cybersecurity Services

While CISOs are well-versed in cybersecurity, the understanding of this topic by other senior leaders is often lacking.

Mandiant Services (IR, Strategic Readiness, Technical Assurance, Cyber Transformation)

Mitigate threats, reduce risk and get back to business with the help of experts.

M-Trends 2023

The highly anticipated annual report is here. In this 14th edition, M-Trends provides an inside look at the evolving cyber threat landscape drawn from Mandiant incident response investigations and threat intelligence analysis of high-impact attacks and remediations around the globe across the last year.

The Defender's Advantage Virtual Series

As outlined in Mandiant's award-winning book,"The Defender's Advantage", organizations are defending against adversaries within their very own environment. Because the defender owns the environment in which they go head-to-head with these ruthless attackers, it's important to remember that the defender has a fundamental advantage–however, many organizations struggle to capitalize on it.

The Cyber Snapshot

The Defender’s Advantage Cyber Snapshot report delivers insights into today’s top cyber defense topics based on Mandiant frontline observations and real-world experience.

Mandiant Academy

Bridge your organization's cyber security skills gap with Mandiant Academy's elite mix of training courses, certifications and real-world exercises led by top experts in the field.
Get visibility into threats that matter to your business right now.
Threat Intel Datasheet

The persistence of modern threat actors requires attention and increased knowledge from all security professionals.

Ebook: Data, People and Process

This threat intelligence 360° view of threat actors, their tactics and targets help security teams worldwide with defense strategies to protect their organizations from adversaries.

Applied Threat Intel Datasheet

Modern cyber attackers are increasingly stealthy, unpredictable and persistent, creating challenges for organizations of all sizes.
Identify high-risk exposures and validate if your cyber security program is prepared to defend and respond.

Executive Summary: Building Cyber Resiliency

Read the Executive Summary on Building Cyber Resiliency.

Mandiant Proactive Exposure Management

For more information about Mandiant Proactive Exposure Management, read the Solution Brief.
How to Effectively Test and Measure Your Cyber Defense Program

Watch the on-demand discussion on the best practice methodologies and technologies your security team can use to effectively test and measure your cyber defense program.
Building a Proactive Strategy to Exposure Management

Learn how to how to expand visibility, prioritize threats, validate preparedness, and remediate faster. Watch the on-demand discussion:
Detect and respond to modern threats with an AI-powered SecOps platform infused with frontline threat intelligence.
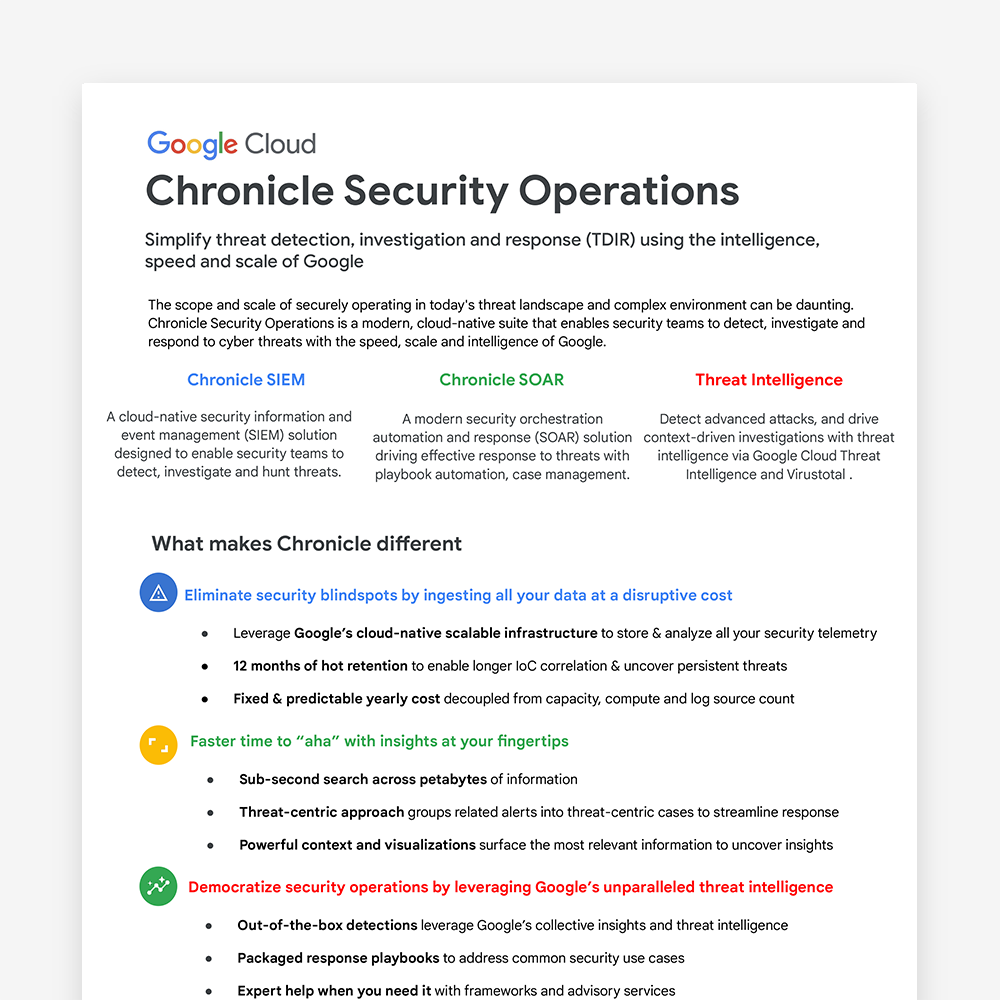
Chronicle Security Operations Datasheet

Simplify threat detection, investigation and response (TDIR) using the intelligence, speed and scale of Google.
Chronicle website

Detect, investigate and respond to cyber threats with Google's cloud-native Security Operations Suite.

Cyderes Case Study

Managed Security Service Provider, Cyderes, needed a robust platform that would allow them to ingest any kind of data at volume and bring automation to their customers.
Telepass Case Study

Existing Google Cloud customer Telepass, an Italy-based electronic tolls processor and mobility solutions company, adopted Chronicle Security Operations to consume all their security events into one place, filter out false positives, respond to real threats more efficiently, and integrate with other Google Cloud security services.

Google Cloud Security Summit session

Simpler cloud-native threat detection, investigation and response, from end to end.

Chronicle Security Operations

Say goodbye to legacy SIEMs, DIY engineering and missed threats, and hello to Chronicle Security Operations, from Google Cloud. Introducing a modern, cloud-native, AI-powered platform designed to serve as the "workbench" for security operations teams tasked with detecting, investigating and responding to cyber threats across their hybrid environment. It combines key functions such as security information and event management (SIEM), security orchestration, automation and response (SOAR) and threat intelligence from Google Cloud, Mandiant and VirusTotal.
Stay ahead of cyber threats and protect your critical assets with crowdsourced intelligence.

VirusTotal Enterprise 360 Overview

VirusTotal is the world’s richest, most interlinked and closest to real-time crowdsourced malware corpus.

VirusTotal Threat landscape module

Adversary intelligence layer providing superior context across the VT ENTERPRISE threat intelligence suite.
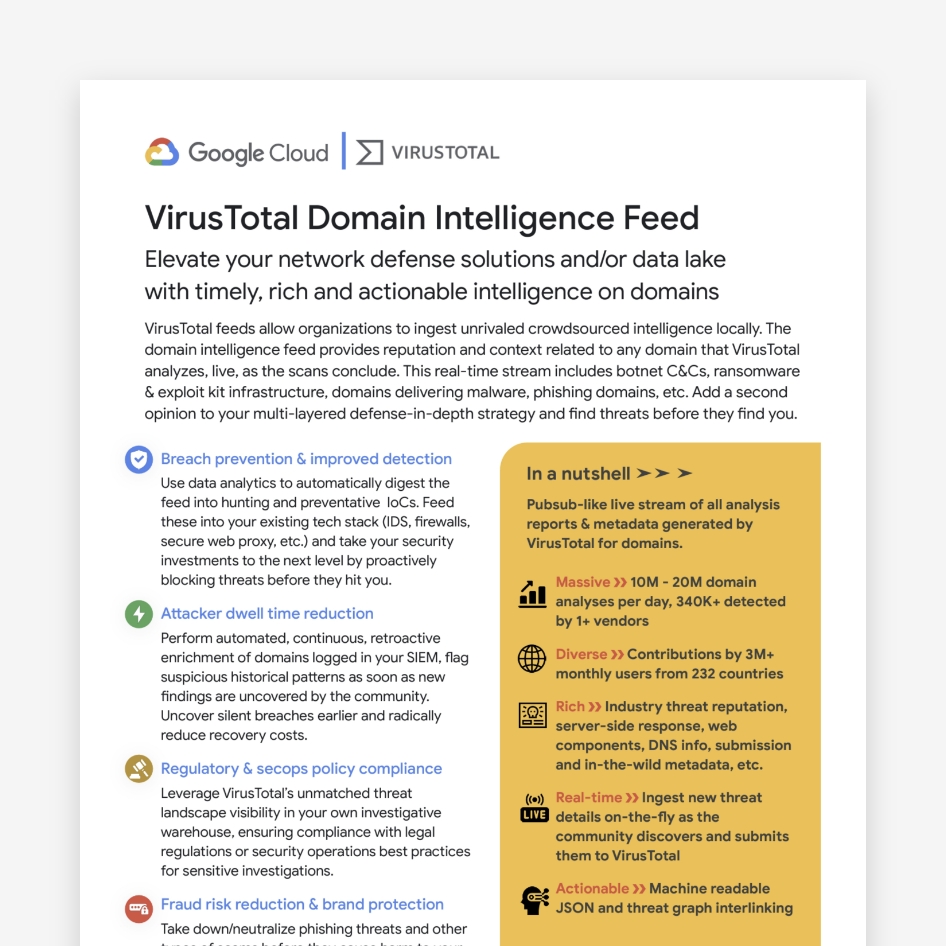
VirusTotal Domain Feeds

VirusTotal feeds allow organizations to ingest unrivaled crowdsourced intelligence locally.

VirusTotal Malware Trends Report

Welcome to the VirusTotal "Emerging Formats and Delivery Techniques" research report.
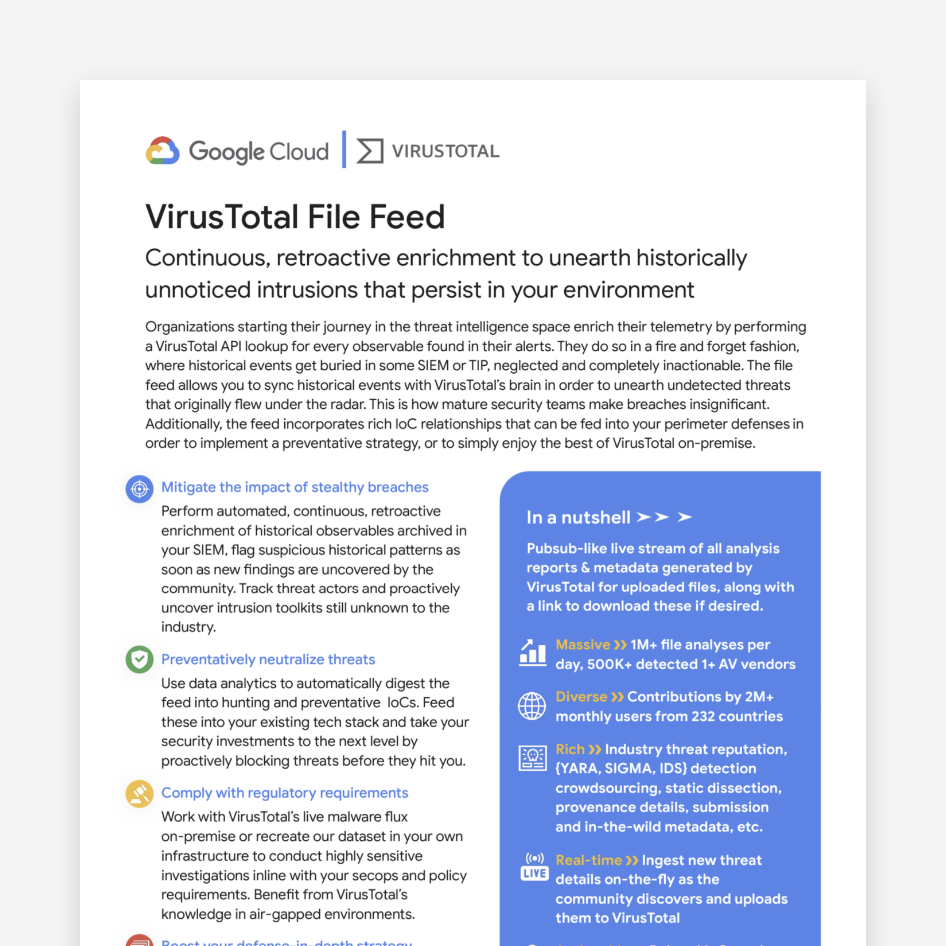
VirusTotal File Feeds

Organizations starting their journey in the threat intelligence space enrich their telemetry by performing a VirusTotal API lookup for every observable found in their alerts.
Have questions? Let's talk.
Mandiant | Google Cloud experts are ready to answer your questions.

