Attack Surface Management Identifies Critical Issues
Cloud resources, unmanaged assets, code repositories — all internet-facing assets have the potential to be exploited if there is an unmitigated vulnerability, misconfiguration, or exposure. In the recent The Defender’s Advantage Cyber Snapshot article, Detecting Common Exploitation Paths Exposed on the Internet, the Mandiant team used Attack Surface Management to identify 21,000+ critical and high severity issues across customers’ external assets from January to March 2022. From exposed version control repositories to Microsoft Exchange Server vulnerabilities, the team detected exploitation paths that a persistent threat actor can readily identify.
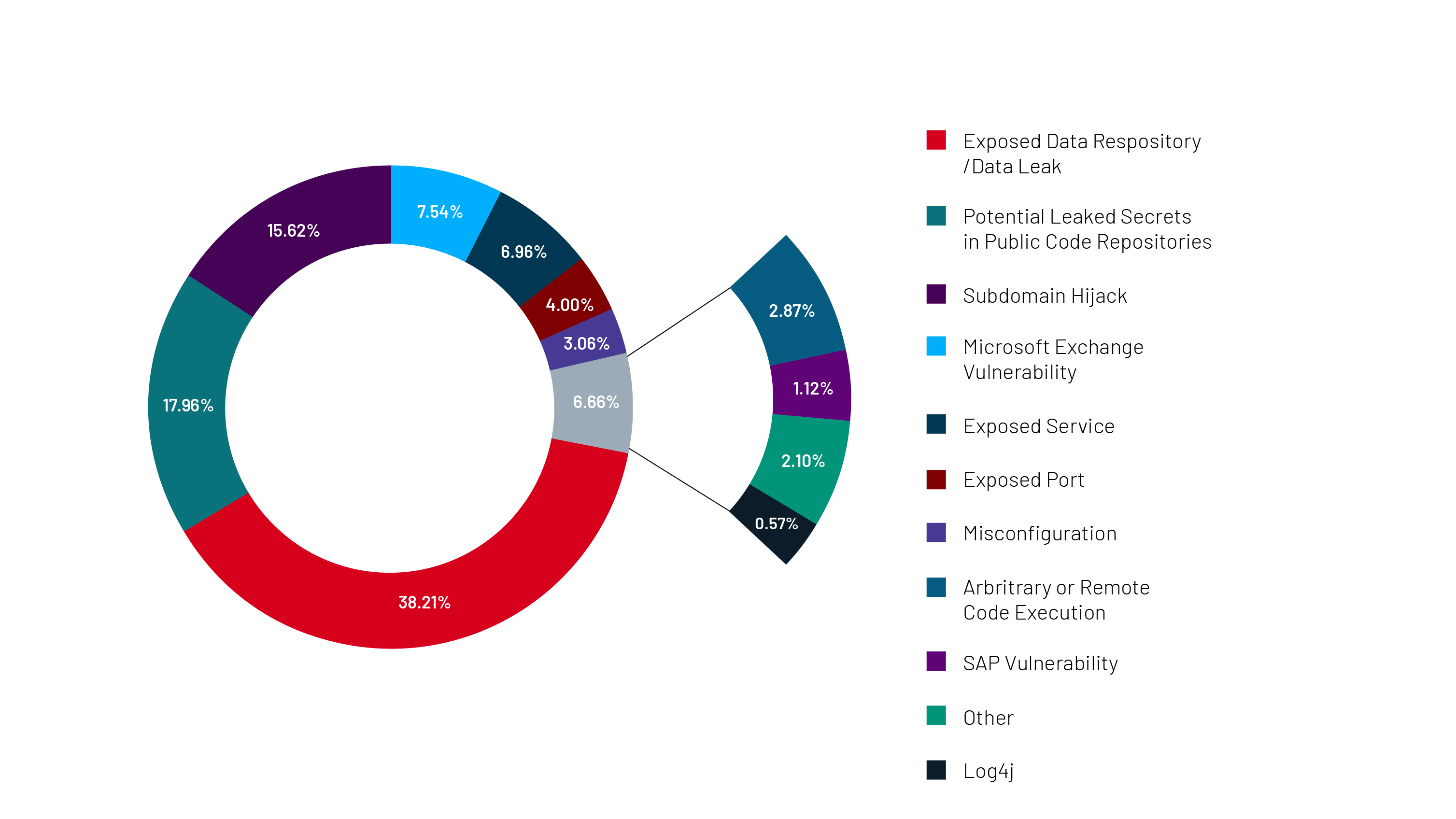
Threat actors have the tools and resources necessary to automate reconnaissance at scale, identifying and capitalizing on the exploit paths available to them. Mandiant has observed this behavior on the frontlines; from the M-Trends 2022 Report, 25.8% of intrusions had evidence of MITRE ATT&CK Technique T1190 or initial compromise from the exploitation of public-facing applications (M-Trends 2022 Report).
The exponential growth of SaaS applications and services combined with the dynamic nature of hybrid IT environments makes it increasingly difficult for security teams to effectively discover and assess assets at scale. With digital innovation and time-to-exploitation both gaining velocity, it’s important for security teams to streamline external asset discovery and vulnerability detection to mitigate risks faster and reduce the attack surface.
On July 13th, join Jonathan Cran, VP of Research & Engineering, and Nader Zaveri, Senior Manager of Incident Response and Remediation, for a live discussion and tactical advice on identifying, remediating, and hardening against the common exploitation paths exposed on the internet.
Register today
Additional Resources
Get your free copy of The Defender’s Advantage Cyber Snapshot article, Detecting Common Exploitation Paths Exposed on the Internet, to learn more about the most common asset exposures and what you can do about them.
