Announcing Mandiant Advantage Attack Surface Management
Want to jump in now? Get started with Mandiant Advantage Attack Surface Management by creating your free account today!
As organizations continue to digitize their business and employees are empowered to leverage these capabilities, it’s no wonder security teams struggle to keep track of infrastructure, applications, cloud services and SaaS usage—let alone ensure security policies are adhered to across these environments. The attack surface is dramatically and vastly expanding, and without the proper automation, it is unlikely that security teams will have the visibility, control, and timely threat intelligence they need to manage it.
Mandiant Advantage Attack Surface Management (ASM) addresses this challenge by providing extensive asset and exposure visibility in Internet-facing attack surface. It fills the ever-widening gap across asset discovery, vulnerability management and threat intelligence. ASM helps enable security teams to operationalize intelligence by first discovering assets across open, on-prem, and cloud data sources—and correlating those assets’ exposures with intelligence, bringing them to the attention of the responsible parties.
In the wake of large-scale attacks against software such as log4j, Accellion, SolarWinds, and Exchange, and with large-scale supply chain breaches becoming common—ASM is no longer a nice to have option, but a must-have for security teams. The integration of ASM into the Mandiant Advantage platform brings customers closer to the goal of ensuring critical intelligence can be quickly disseminated to asset owners, driving action across every facet of their operation.
Attack Surface Management Value Points
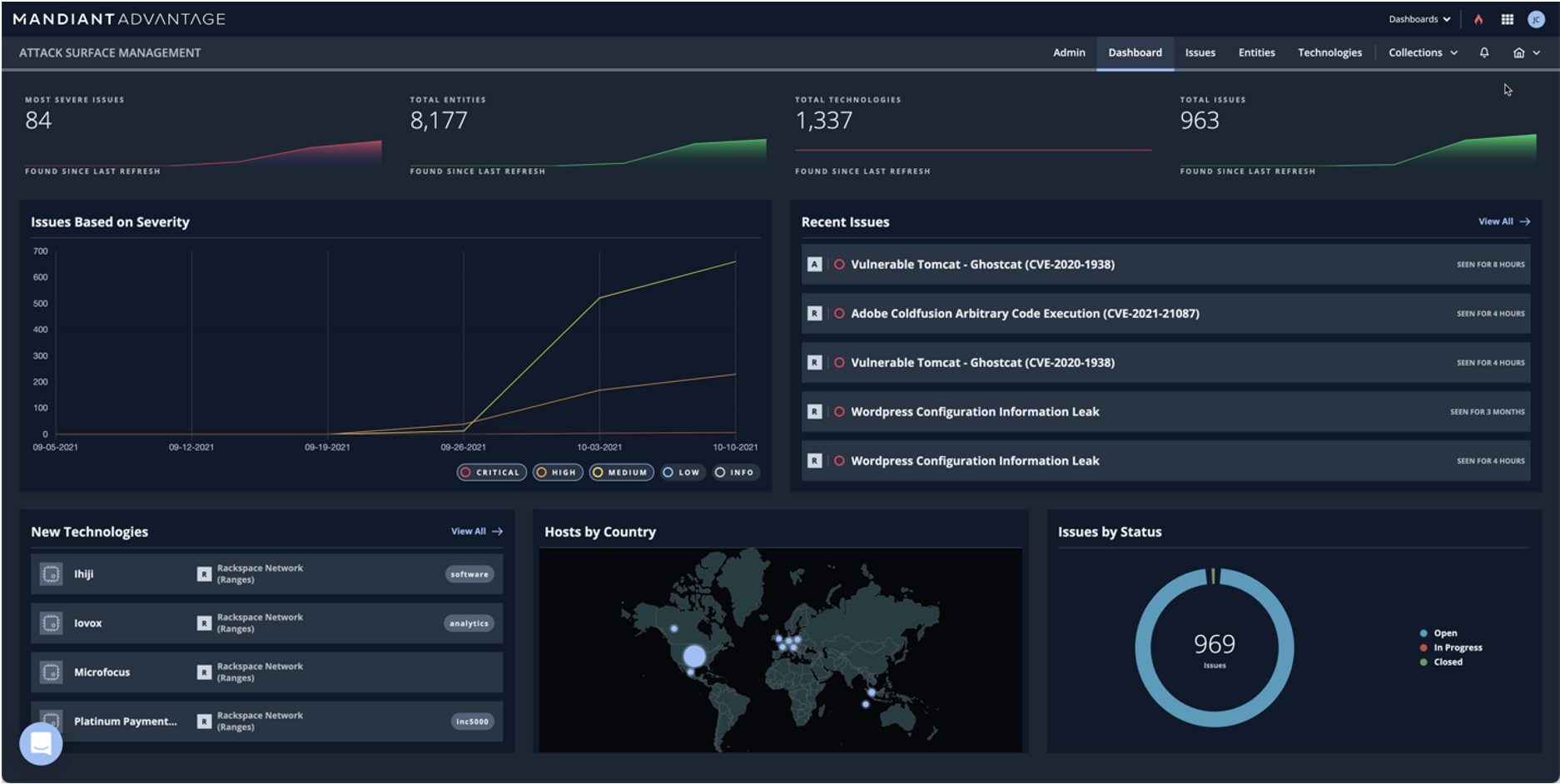
The integration of Attack Surface Management into the Mandiant Advantage Platform delivers ever-increasing cross-module value to our customers. The following are just a few highlights:
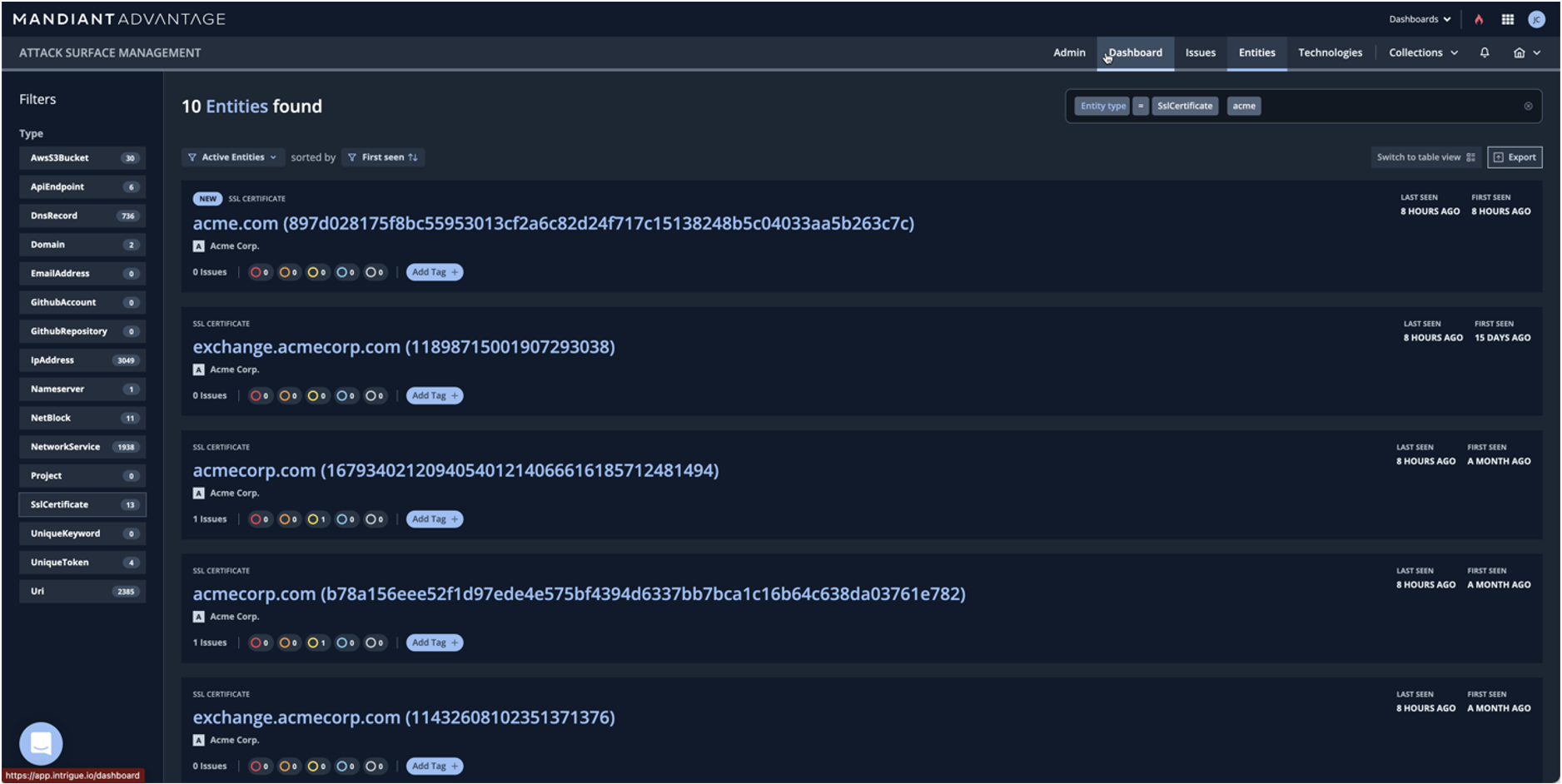
- Automatically identify and monitor your assets. You can’t fix what you don’t know. With zero effort, begin by seeding your known assets, and ASM will utilize a multitude of disparate sources to automatically find and categorize assets. This capability provides a foundational asset inventory, with incredible depth of information.
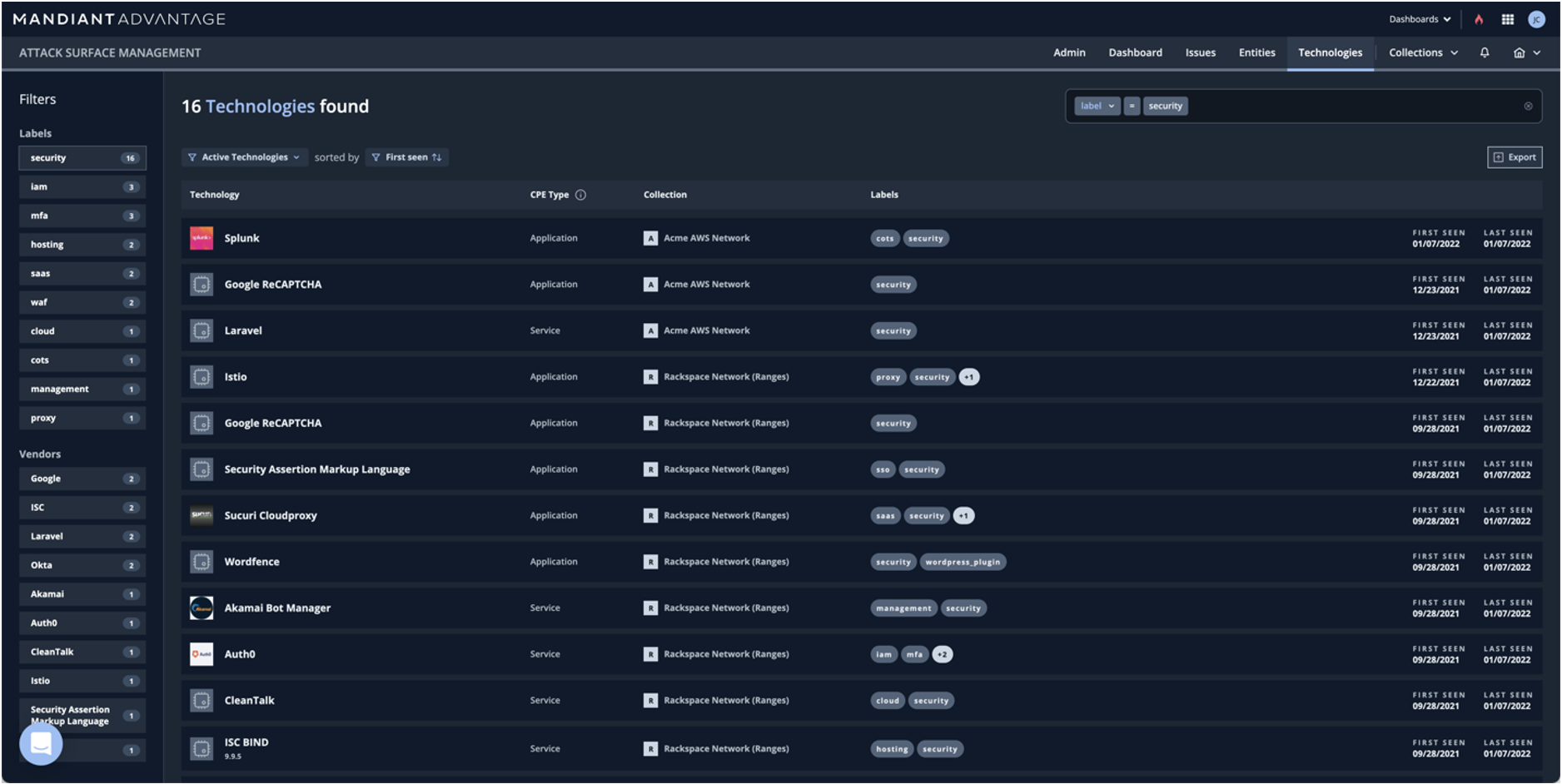
- Query in-depth software and service information. ASM doesn’t stop by just finding assets, each individual resource is deeply enriched to identify running software, configurations and other attributes to help speed the classification and categorization process. No effort required! Simply query and find over 5000 categorized products.
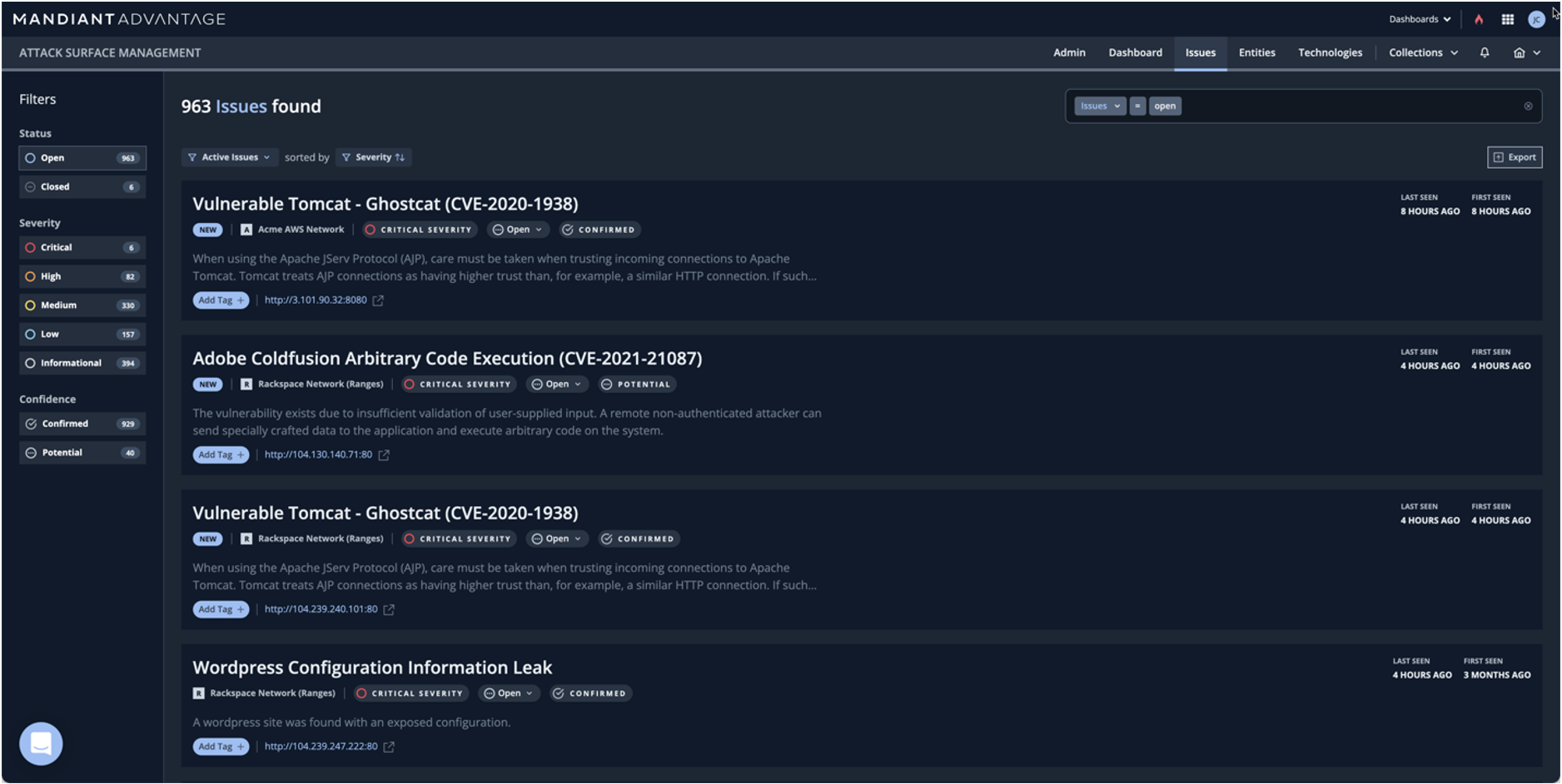
- Drive awareness of exposures, informed by threat intelligence. Detecting assets is only useful for security teams if risk is part of the equation and exposures can be identified and quickly triaged. To this end, ASM integrates both passive and active measures to identify exposures and prioritize those against the latest threats.
This deep visibility provided by ASM is informative to the development, and the enforcement of, security policy. By identifying Internet-facing assets and their security posture in real-time as they’re exposed, security leaders are able to drive insight into the business and utilize the information to identify asset owners and drive crucial conversations on demand and ahead of the threat.
ASM in Practice
In recent years as attack surface has expanded for the modern enterprise, newly announced exposures and vulnerabilities follow a predictable pattern. First, there is an announcement of a new vulnerability or misconfiguration affecting enterprise resources. As information about the vulnerability emerges, security teams scramble to identify assets affected, often casting a wide net to first identify ANY instances of the software, and later, drilling into specific affected configurations. This can take many forms, but often requires correlating many data sources and bringing together a multitude of stakeholders.
As potentially vulnerable assets are identified, security teams must contact the asset owners to gain access to the configuration and details needed to determine whether they are affected. This is a time consuming and tedious process. Meanwhile, attackers are actively exploring the vulnerability and organizational attack surface to identify how it can be used in practice against the very same organizations. It is a race against time.
Most recently, this pattern emerged with the Log4j vulnerability, and the early timeline of these activity provides a clear picture of how ASM responds in these situations:
- December 9, 2021: Zero day for Log4j vulnerability posted on Github.
- December 10, 2021: Mandiant ASM integrates an active check to test for the vulnerability. All ASM customers are immediately scanned for vulnerability. Notifications are sent as the vulnerability is identified in customers’ attack surfaces.
- December 10, 2021: Apache Foundation announces CVE-2021-44228 and releases Log4j 2.15.0 to address the vulnerability.
- December 13, 2021: More details emerge about the vulnerability, ASM check updated to identify additional entry points. Notifications are sent as the vulnerability is identified in customers’ attack surfaces.
- December 13, 2021: Mandiant reports state actors utilizing the vulnerability in the wild. Information integrated into ASM.
This is a just a snippet of the early timeline. details continued to emerge throughout the month, and each time, ASM was updated to better discover log4j and related technologies that utilized the library. The details of this were published on the Intrigue blog.
The Log4j vulnerability is, unfortunately, not an anomaly. The speed at which this process unfolded is increasingly common. This environment demands that security teams maintain comprehensive awareness of their environment. Not just for Log4j, but for all exposed software and services. Mandiant ASM helps customers inventory assets, identify technologies and exposures and enable quick action when a new threat emerges.
Better Together—the Mandiant Advantage SaaS Platform
Launched in October of 2020, Mandiant Advantage brings technology scale to the expertise and intelligence gained on the front lines of Incident Response. It is the SaaS interface and central platform to access the Mandiant technology suite.
ASM is an important addition to the Mandiant Advantage platform, enabling defenders to discover impact and prioritize defenses in real time. Let’s take a quick look at how the modules operate and interact.
- Threat Intelligence: Intelligence from the frontlines. Allows a defender to know what tactics, techniques and procedures (TTPs) adversaries are leveraging right now. As attackers are utilizing X vulnerability, we see Y tactic being used, and we are able to identify the specific indicators of compromise (IoC) and the tech stacks being targeted. By combining ASM and Threat Intelligence, organizations will be able to operationalize, contextualize and prioritize new intelligence that is most relevant.
- Security Validation: Measures the effectiveness of security controls deployed within an organization, allowing security teams to optimize, rationalize and prioritize their security efforts both from a budget and person power perspective. By integrating intelligence into the Security Validation program, controls can be tested against the latest TTPs actively being leveraged by threat actors. By combining ASM and Security Validation, organizations can validate if their security controls are effectively blocking or detecting attacks to their external attack surface.
- Automated Defense: Combining expertise and intelligence with machine learning to power SOC event/alert correlation and triage—it’s like having a machine-based Mandiant analyst integrated into your security program. The expert models analyze billions of events and alerts from multi-vendor controls to look for true positives or incidents, saving massive amounts of time in analyst hours. ASM provides additional context to Automated Defense, making alerts more relevant and actionable.
- Attack Surface Management: ASM provides a continuous, scalable approach to discover thousands of different asset and exposure types across on-premises, cloud, and SaaS application environments. Not only are assets discovered, but technologies in use are identified and vulnerabilities are confirmed—not just inferred. By adding the complete Mandiant Advantage suite into ASM, the information about the attack surface is prioritized and validated, allowing cyber defenders to reduce their external exposures efficiently and effectively.
Get started with Mandiant Advantage Attack Surface Management now by creating a free account today! Or check out the Mandiant Advantage Attack Surface Management for more information.