Gain Visibility Into Attacker Activity with Threat Campaigns
As attackers conduct operations, they often change their tactics and techniques, introduce tools with new capabilities, and use new infrastructure to carry out their mission. It can be difficult for security teams to maintain awareness of these evolutions and take appropriate actions based on any changes. To better assist these teams, Mandiant is now offering a Threat Campaigns feature within Mandiant Advantage Threat Intelligence to provide security professionals with a quick way to stay updated on active campaigns affecting their industries and regions.
Threat Campaigns helps prioritize defensive actions by identifying actors, exploits, or other threats that are actively impacting similar peer organizations. Dynamically vetted content for individual and global campaigns, including a detailed, visual timeline of events and examples of attacker techniques, provides an up-to-date view into observed activity during the attack lifecycle. With the event details provided, users can quickly hunt for specific threats known to be used in active threat campaigns, reducing wasted cycles.
Individual and Global Campaigns
The addition of Threat Campaigns builds upon the mission of Mandiant Advantage Threat Intelligence: to provide greater visibility into attacker operations while increasing the speed at which this visibility can be provided. Individual campaigns, which we define as a threat actor or multiple threat actors cooperating toward a single objective, allow security teams to track changes in operational patterns and targeting. For operational and hunt teams, the ability to quickly identify changes in attacker techniques and capabilities increases the speed in which they can adjust their detection and mitigation responses.
Global campaigns, on the other hand, cover multiple unrelated threat actors running parallel campaigns involving a similar theme, target, or resource. This provides insight into big events, like widespread vulnerability exploitation, where an exploit for a vulnerability is released in the wild and multiple threat actors quickly start using the exploit to target organizations. For operational teams, this helps identify known exploitation activity before a patch is released and applied, and at a strategic level this provides a better understanding of threat actor activity trends, like the average time to exploit, which can better inform security priorities and leadership decisions.
Advantages of Threat Campaigns
- Gain an In-Depth View of Attacker Timelines: The detailed timeline provides dates for when we first and last observed an attack technique during a campaign. It also includes key events identified by Mandiant analysts as critical to understanding the campaign’s activity. These can include events like the exploitation of critical systems, malicious code compile times, and observed waves of phishing emails. This level of detail, coupled with the dynamic updates that occur as Mandiant analysts are identifying new campaign events, helps users understand the sequence of observed events, from the identified initial infection vector to the later stages of an attack. This can be helpful for analysts trying to assess what to do next. If an analyst identifies a phishing email that was observed in a campaign, they can use the detailed timeline to identify what the attacker typically does next and the average length of time before that happens to inform hunting and remediation priorities.
- Better Understand Attacker Techniques: Each key event on the detailed timeline has additional information which helps provide context to the activity. Mandiant analysts add descriptions and comments to explain the event’s significance. If the event involves the use of a malware family, tool, or the exploitation of a CVE, that context is presented with the event. If the event demonstrates the use of an attacker technique, that context is also included. Where possible, actual examples of attacker activity from the campaign, including host commands or sanitized event log data, are provided. This additional context provides security teams with more actionable information and better visibility into how attacker techniques were executed throughout the campaign.
- Prioritize Active Threats with More Context: Campaigns allow organizations to quickly identify active threats targeting their industry or region and drill down into the detailed timeline to gain the context needed to take necessary action. Security teams can use this information to narrow the scope of their hunting efforts to focus on specific threats, events, and techniques identified in active campaigns.
A Walkthrough of Campaigns Within Mandiant Advantage Threat Intelligence
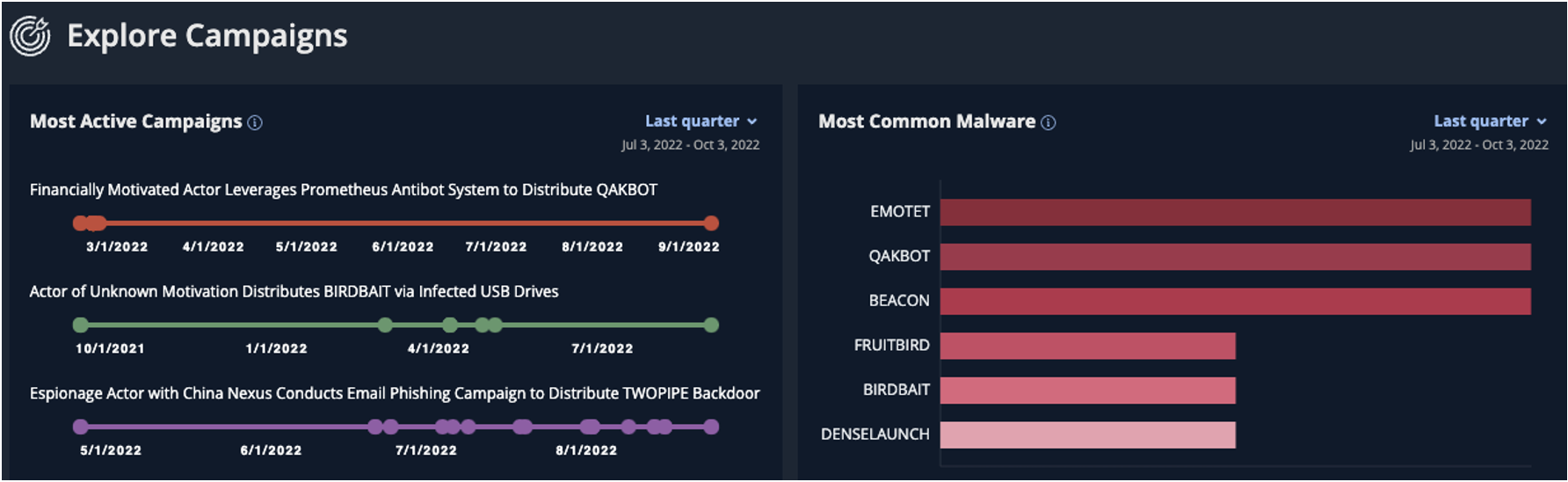
- Campaigns Dashboards: At-a-glance dashboards (Figure 1) provide a view of the most active campaigns and most commonly observed malware across all campaigns for a given time period.
- Campaign Details: As new events are observed, automated updates are made to the campaign’s details page, including adding recent events to the high-level timeline, updating any new targeted industries and regions, listing new malware and tools, and noting any newly exploited vulnerabilities.
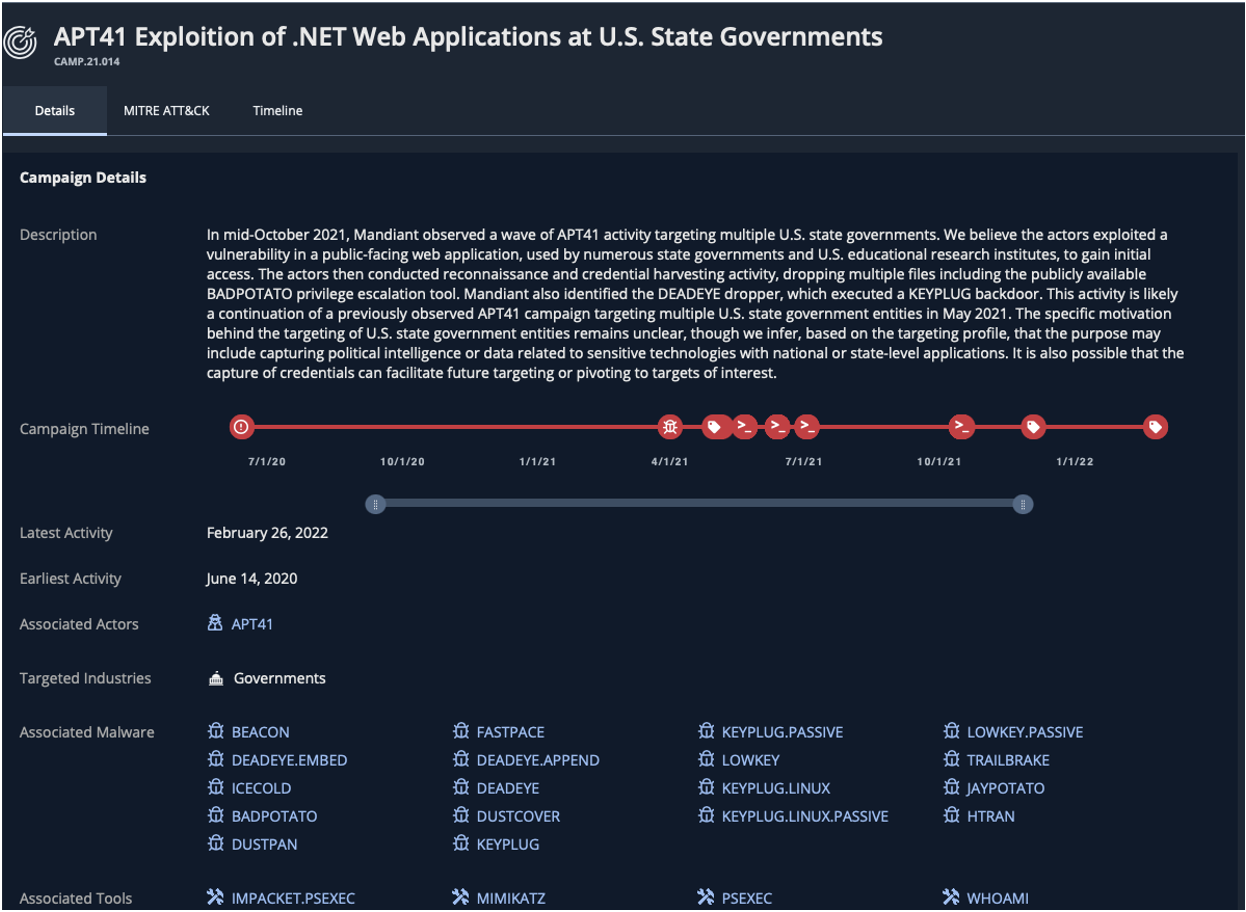
- For example, in March 2022, we released a blog on an APT41 campaign targeting U.S. State governments. Details on this campaign are now available within the Threat Campaigns section of Mandiant Threat Intelligence (Figure 2). If Mandiant identifies any new activity for this campaign, it would automatically be reflected here and in the API. This increases the speed at which updates can be delivered to and ingested by security teams.
- Campaign Timeline: In addition to a high-level overview of a specific campaign, the timeline tab provides details on observed attacker techniques and analyst identified “key events” which illustrate the sequence of significant attacker activities during a campaign. The timeline is broken down by event type to allow users to easily identify the type of activity that was observed.
- In the APT41 example, the first key event flagged by Mandiant analysts was the attacker exploiting a directory traversal vulnerability in June 2020. Users can click on each event on the timeline (Figure 3) to see the attacker activity that followed the exploitation.
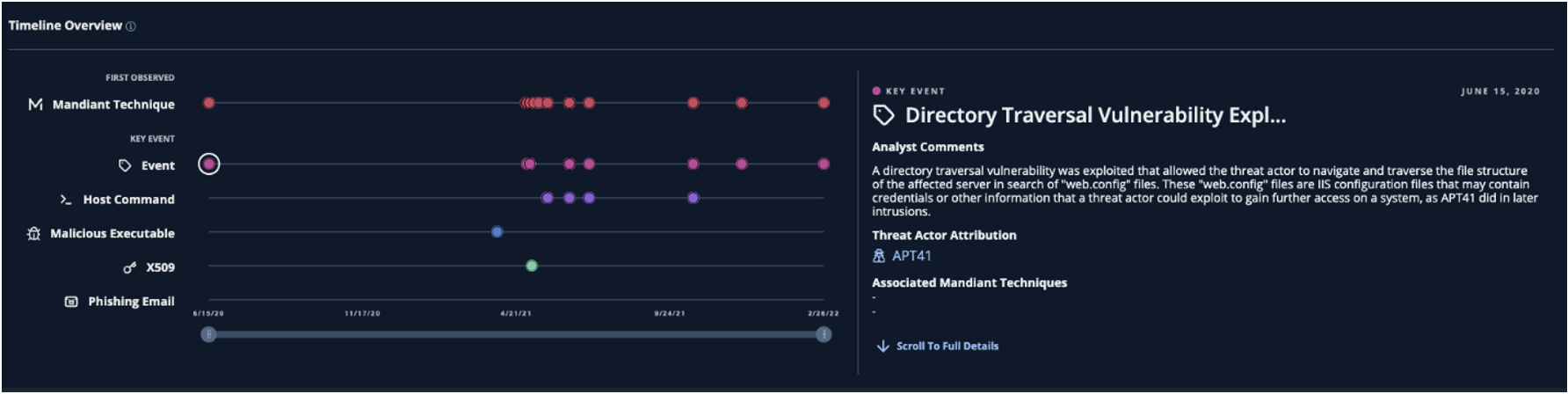
- Mandiant Techniques: Mandiant Techniques are our own classification of attacker methodologies and are a byproduct of responding to hundreds of computer intrusions and conducting leading threat research. The first line on the timeline in Figure 3 shows the date Mandiant first directly observed an attacker using a Mandiant Technique during the campaign. While these are all actively mapped to the MITRE ATT&CK techniques, we are choosing to expose Mandiant Techniques within Mandiant Advantage Threat Intelligence to provide users with additional context not currently available in the ATT&CK framework.
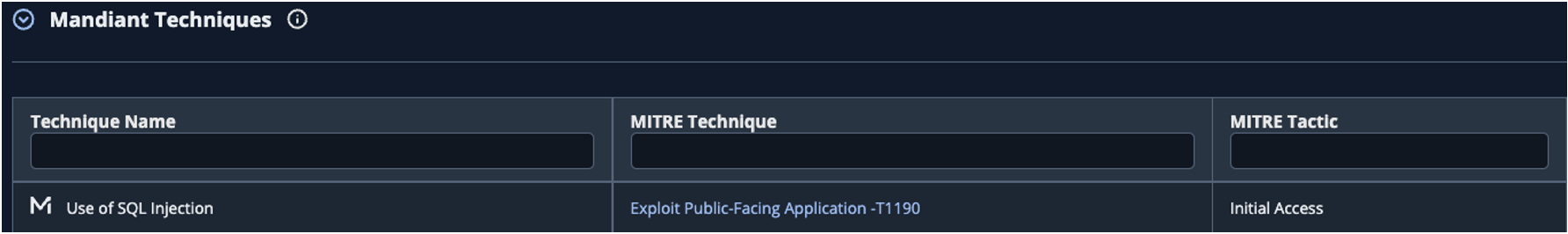
- For example, instead of providing the more generic description of “exploiting public-facing application,” Mandiant Techniques allows us to include the type of exploit that was observed during the campaign (Figure 4). The added specificity helps users narrow the scope to the type of exploit or application they should be concerned about.
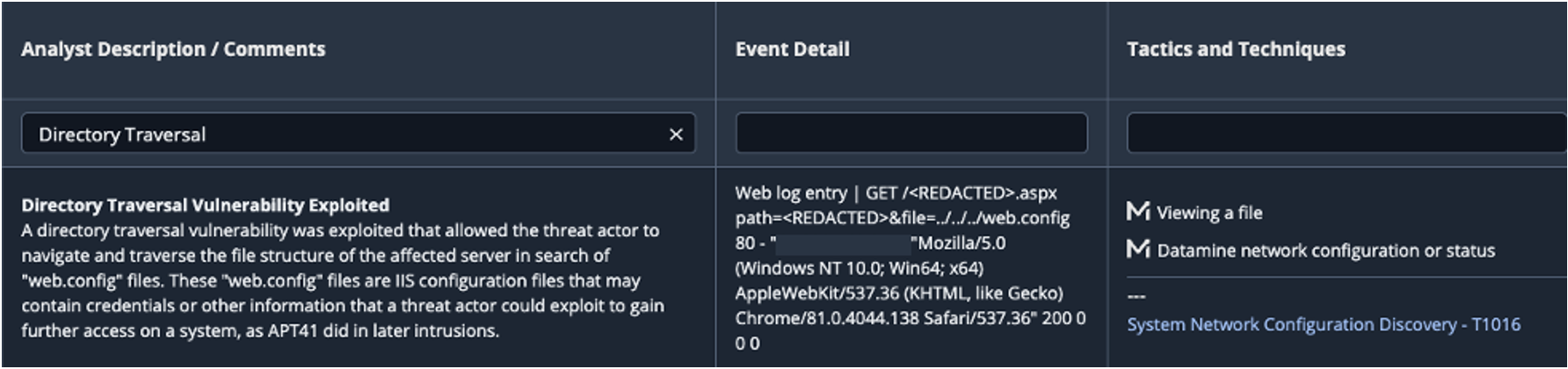
- Key Event Detail: Details on each technique and key event noted on the timeline are provided in detailed tables (Figure 5). This includes analyst descriptions and comments, and where possible, actual commands executed by the attacker, or evidence of attacker activity in event logs. All examples are annotated with Mandiant and MITRE ATT&CK techniques where possible, providing actionable detail for security analysts.
- For example, the Directory Traversal event in Figure 5 has the analyst description, comments and an example of a sanitized web log entry which demonstrates the attacker datamining for “web.config” files in attempt to obtain credentials.
Conclusion
Threat Campaigns in Mandiant Advantage Threat Intelligence provides greater visibility into active and relevant threats, helping security professionals not only prioritize and focus on the threats that matter, but also receive actionable intelligence. This helps them anticipate, identify and respond to threats with more confidence and reduces unnecessary stresses in an already hectic role.
