The Cyber Risk Journey, Part Three: Cyber Due Diligence in Mergers and Acquisitions
Whether you exist on the buy or sell side of a transaction, resilient digital assets—especially network systems and customer data protection—are paramount to the success of all businesses. Data and information are proving to be a fluid commodity for many organizations, but also a point of leverage for attackers looking to exploit organizations. Understanding how vulnerable a business you wish to acquire or divest is to cyber security threats, and how well it can defend itself, is becoming more of an expectation than a “nice to have” for organizations. In the current business climate, organizational strategies driven by inorganic growth via acquisition or mergers are becoming more frequent. On the opposite end are organizations looking for divestment opportunities to change or pursue different business priorities, where the ability to position assets for sale is becoming more competitive when it comes to attracting buyers and optimizing asset valuations.
For any acquisition, it’s crucial to take a close look at the target organization’s existing cyber security practices and operations before making the decision to acquire and possibly integrate. Organizations preparing for sale are looking to optimize valuations and are starting to lean into proactively providing cyber results to demonstrate how they’re maintaining safe and secure standards that protect and provide a minimum level of assurance around their data protection practices. This is still not a very mature practice across many industries. There are known cases and precedents where shallower due diligence practices have left acquiring organizations with overvalued acquisitions, with compromised intellectual property (IP) or looming legal disputes associated with poor cyber practices leading to harm to customer data.
When looking to embed due diligence practices into an existing or developing M&A practice, we suggest focus on the pre and post phases as logical points of injection. See Figure 1.
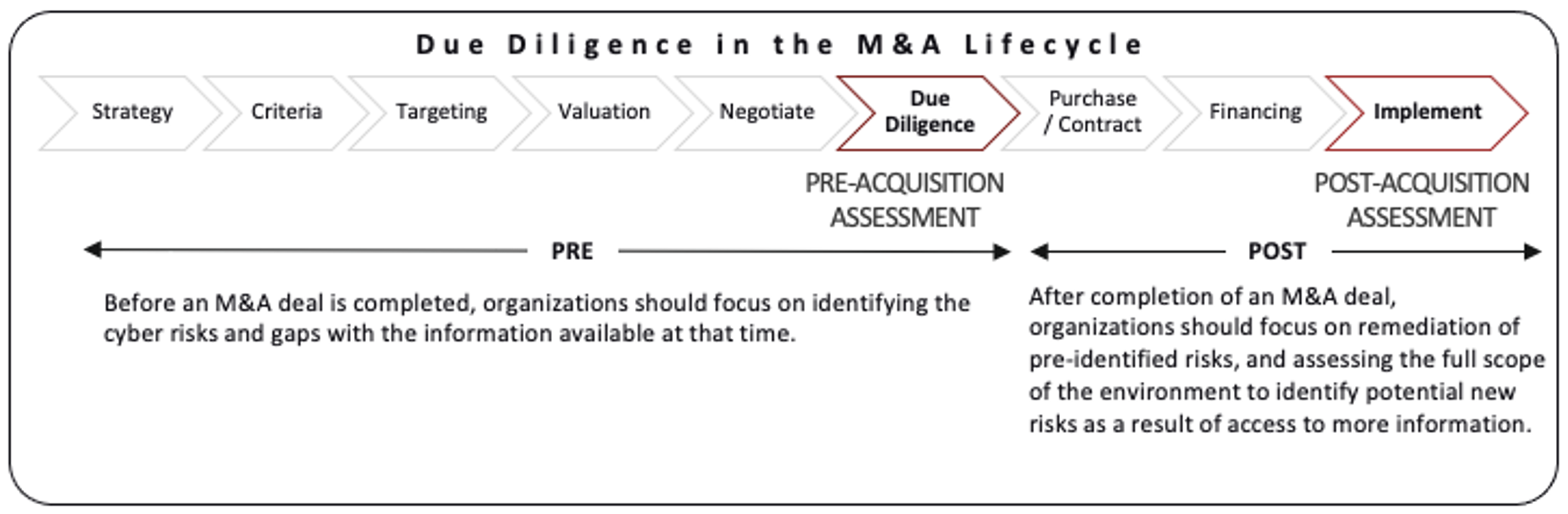
From a Buyer’s Perspective
Companies involved in acquisitions need to be aware of the risks they face. An organization may not only be acquiring a target company’s assets, but also their weaknesses and risks. Completing an acquisition of an organization that has poor cyber hygiene puts the acquiring company at risk of compromise, or further compromise from threat actors who may already be in those networks. To minimize these risks, we often work with companies to hunt for evidence of compromise through our Compromise Assessment, designed to identify ongoing or past attacker activity within an environment.
Acquisitions can increase the risk profile of organizations depending on the industry, geography, and partners associated with those organizations. As such, an updated understanding of the threat landscape is needed by the acquiring company. Even in the case of stand-alone acquisitions, with no planned technical integrations, reputational damage and negative reflections on company valuation may result if an acquired company is the victim of a publicized cyber security breach.
What should an organization do if they discover poor cyber security practices present in a target? The development of a post-merger integration plan or roadmap to improve cyber security practices and ensure the maturation of cyber security operations at the acquired company, prior to the integration of that company into the primary network, is critical. These efforts and associated costs should be factored into the purchase price of the prospect or the quality of the transaction.
Performing a cyber defense assessment before acquiring a prospect can provide advantages for the buyer, including:
- Ascertaining the level of oversight and guidance present within the security program of the prospect. Poor oversight and guidance of a security program will usually lead to systemic cyber security issues, and this can lead to increased costs or financial liabilities.
- Understanding if the prospect is currently compromised. If an active attacker is within the environment of the target, sensitive data or intellectual property might already be stolen, thereby affecting the value of the target. If the buyer decides to move ahead with the deal, it must also be prepared to deal with the fallout, which can be very costly and harm the company’s reputation.
- Being able to estimate the cost and effort of improving the security posture and infrastructure of a prospect. When the cost is high, it could affect the terms of the acquisition. Focused and actionable insight provided during an assessment is something the buyer would not normally be subject to during traditional due diligence.
- Exposing the possibility of insider threat, and existing mitigating controls to manage such a threat. If employees at the acquired company are concerned about their jobs, the threat of an insider collaborating with bad actors—or acting on their own—increases. An organization should ascertain whether monitoring should be put in place to detect such malicious activity.
- Awareness that the prospect/company being acquired has a more mature security program than the acquirer. If this situation arises, decisions will be needed on how best to align both companies in the future state of their combined security programs.
From a Seller’s Perspective
When it comes to valuation and demonstrating organizational attractiveness, showcasing a recent report from a cyber security assessment to potential buyers goes a long way. It provides acquirers with a positive mindset regarding the health of the asset that is being considered, either for a standalone acquisition or a merger. Performing a cyber security assessment prior to being acquired can provide the following advantages for the seller:
- The identification and remediation of challenges before a buyer performs its own due diligence exercises. Current remediation efforts aligned to a roadmap can be provided to the buyer in confidence, showcasing proactive efforts by the seller towards improving its cyber security posture.
- Provides details to the buyer on key security related third-party agreements, and the responsibilities of these third parties in safeguarding key digital crown jewels.
- Improves the Offering Memorandum through third-party endorsement (i.e., “Our cybersecurity posture has been rated as Low Risk by…”).
- Provides greater confidence in valuation calculations.
Threat actors aren’t stopping and cyber risk continues to increase, so organizations have no choice but to be careful and proactive about cyber security during every stage of the M&A process. With our comprehensive approach, we help to enhance the planning, execution, and post-acquisition phases of the transaction. The onus is on both the acquirer and the seller to be diligent prior to, during, and post-acquisition. It’s more important than ever to be prepared for any risks that threaten the outcome of a deal, and that could impact value for both parties.
