Information Operations Targeting 2022 U.S. Midterm Elections Include Trolling, Narratives Surrounding Specific Races, Politicians
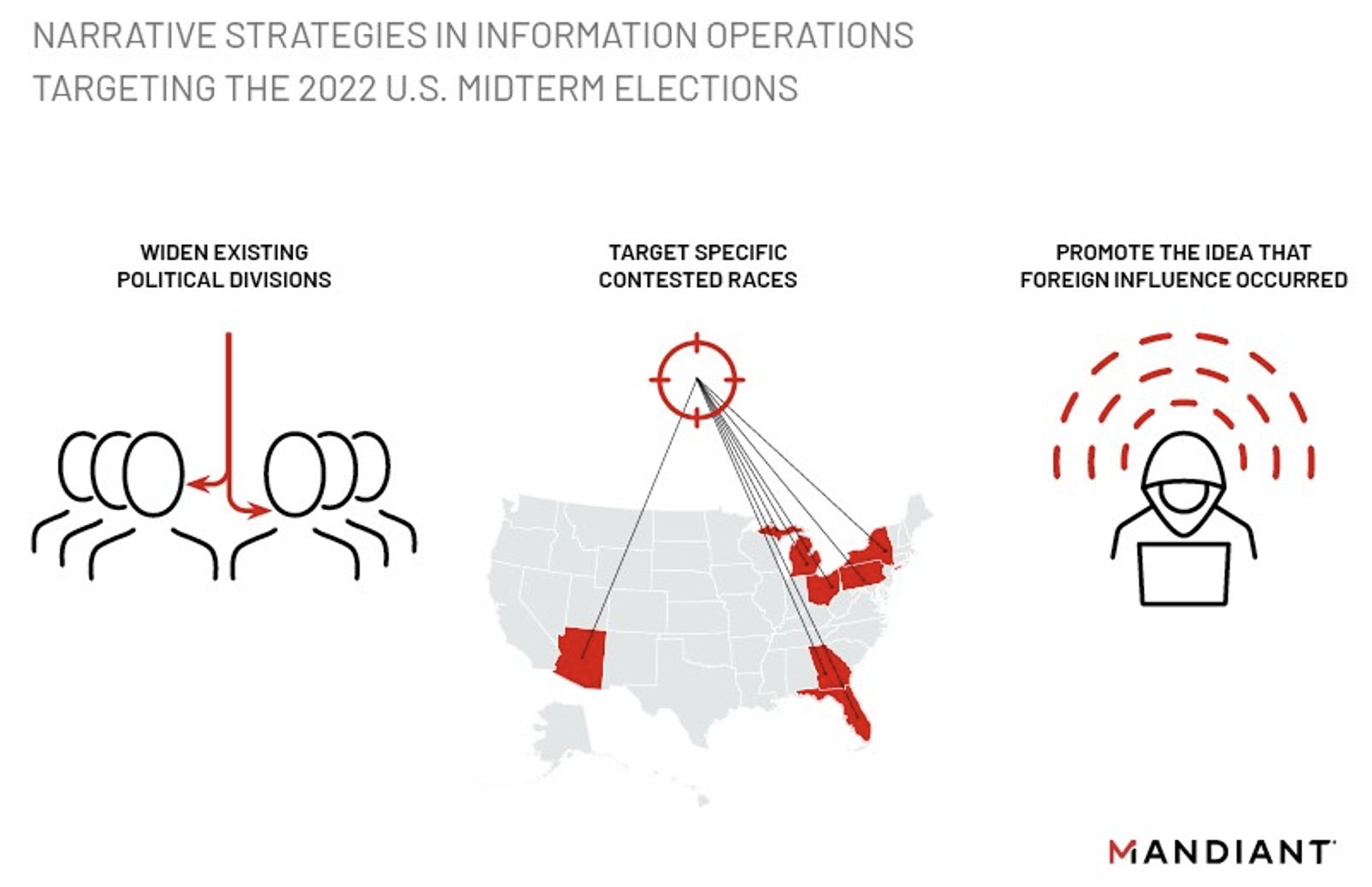
In the lead up to, during, and following the 2022 U.S. midterm elections, Mandiant identified information operations activity from various foreign state-aligned campaigns, including those we assessed to be operating in the interests of Russia, the People’s Republic of China (PRC), and Iran. U.S. midterm elections present a more diffuse set of potential targets than a presidential election, and we observed information operations employing narrative strategies shaped by this dynamic (Figure 1). These operations differ in various ways; however, we note that they all appeared to be somewhat limited in the level of effort dedicated to election-related messaging and/or in potential reach to mainstream audiences based on observed activity, though we note that such operations’ impact is difficult to measure. While the activity identified in this report does not represent a comprehensive accounting of information operations targeting the midterms, we note some broad observations based on newly identified and previously reported operations contextualized within the wider view of relevant information operations activity observed throughout this elections cycle:
- Detected operations were limited to moderate in scale; and in multiple operations, ongoing information operations campaigns pivoted to promote election related narratives as part of their broader activity targeting the U.S., including audiences on both sides of the political spectrum.
- Some activity appeared intended to “troll” defenders, potentially to generate the perception of foreign influence while investing limited resources in the effort.
- Other narratives we identified attempted to exploit controversial issues to widen existing political divisions within the country, or alternatively targeted specific contested election races, which are likely to receive the highest degree of attention.
Pro-Russia Information Operations Appear Intended to Promote Perception of Influence in Addition to Election-Specific Narratives
Since August 2022, Mandiant has identified and reported to customers on multiple instances of Russia-aligned information operations targeting the 2022 U.S. midterm elections, including activity from self-proclaimed pro-Russia “hacktivist” groups and long-established information operations assets. It is likely that a primary objective of the identified pro-Russia actors was to build the perception of influencing the elections—potentially in hopes of supporting future narratives that would undermine the credibility of the election results.
Pro-Russia “Hacktivist” Group ‘Cyber Army of Russia’ Claims DDoS Attacks Against Election-Related Targets
On Election Day (Nov. 8), the “Cyber Army of Russia” (alt: People’s Cyber Army; alt: Cyber Army of Russia Reborn; Russian: Народная CyberАрмия), a self-proclaimed pro-Russia “hacktivist” group, claimed responsibility for multiple distributed denial-of-service (DDoS) attacks targeting U.S. organizations and promoting narratives related to the U.S. midterms. Notably, Mandiant has assessed with moderate confidence that the moderators of the group’s Telegram channel (@cyberarmyofRussia_reborn) are coordinating their operations with Russian Main Intelligence Directorate (GRU)-sponsored threat actors. While these DDoS attacks constitute a clear attempt to promote the narrative of a Russian group targeting a U.S. election, the scope and actual apparent impact of the activity appears to have been limited. It is likely that Cyber Army of Russia intended to shape public perception by advancing a narrative that Russia could and did influence the election.
- Cyber Army of Russia published a Telegram post claiming a DDoS attack on the website of the Democratic National Committee (democrats.org), stating: “Today we attack the American Democrats as a gift to the Republicans for the elections!” (translated from Russian) (Figure 2).
- It is plausible that the group’s messaging constitutes an opportunistic attempt to leverage pre-existing narratives rather than an actual indication of support for a particular political party.
- Another Telegram post by Cyber Army of Russia claimed responsibility for a DDoS attack targeting the website of the Mississippi Secretary of State, noting: “We hit the section [of the site] that is directly related to the elections” (translated from Russian).
- We consider this activity to be consistent with that previously associated with the group. Cyber Army of Russia, which formed in response to the Russian invasion of Ukraine, has primarily targeted Ukrainian entities as well as occasionally targeting supporters of Ukraine with claimed cyber threat activity including compromises, data leaks, and DDoS attacks.

Pro-Russia ‘Hacktivist’ Groups Promote Election-Related Messaging
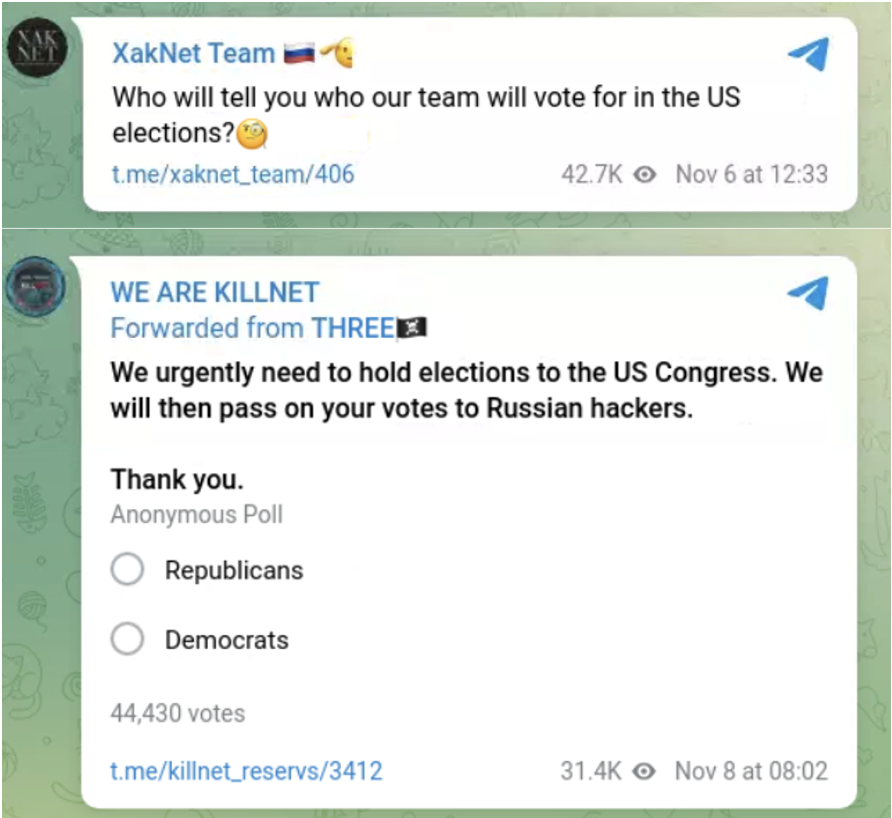
In November, we additionally identified multiple instances of other self-proclaimed pro-Russia hacktivist groups promoting midterms-related narratives via their Telegram channels, consisting of publishing or cross-promoting content about the elections rather than claiming specific threat activity (Figure 3). While we consider such messaging to be less significant than the attacks claimed by Cyber Army of Russia, it likely represents a similar effort to build the perception that malicious Russian actors were interested, and potentially successful, in influencing the elections. These actors may also have considered that defenders working to secure the elections would be monitoring these groups, given their persistent engagement in disruptive anti-Western activity, and accordingly posted election-related messaging as a low-level means to expend those defenders’ resources.
- On Nov. 6, 2022, XakNet Team published a post to their affiliated Telegram channel (@xaknet_team), which asked: “who will tell [us] for whom our team is voting in the U.S. elections” (translated from Russian).
- As with Cyber Army of Russia, Mandiant has assessed with moderate confidence that the moderators of the XakNet Telegram channel are coordinating their activity with GRU-sponsored cyber threat actors.
- On Nov. 8, the hacktivist collective KillNet’s main Telegram channel (@killnet_reservs) promoted a post from a third-party channel conducting a poll that stated “We urgently need to hold elections for the U.S. Congress. We will then tell Russian hackers your votes” and giving options to select “Republicans” or “Democrats.”
- Also on Nov. 8, Anonymous Russia, an affiliate of the KillNet collective, published midterms-related posts to their Telegram channel (@anon_by), including those seemingly joking about election interference.
- The name “Anonymous Russia” is likely an attempted appropriation of the brand of the well-known hacktivist collective “Anonymous.” We have identified no indicators that the two are connected; and “Anonymous Russia” has a record of claiming activity that is incongruous to that which is claimed by the “Anonymous” hacktivist collective.
NAEBC Campaign Leveraged Legacy Information Operations Assets to Target the Midterm Elections
In August 2022, we reported to customers that two inauthentic personas that we previously attributed to the NAEBC campaign, a campaign initially centered on the now-inaccessible inauthentic news site “Newsroom for American and European Based Citizens” (NAEBC) and reported in 2020 to be run by individuals associated with the Russian Internet Research Agency (IRA), remained active and had promoted content related to the 2022 U.S. midterms. Through our continued monitoring of known campaign assets, we subsequently observed a series of incremental increases of campaign-linked activity up through Election Day, including both the reactivation of dormant personas and the increasing promotion of election-focused content.
Brazen Behavior Suggests Trolling of Researchers and Defenders
Multiple aspects of this recent campaign activity suggest it may constitute an intentional effort to troll researchers and defenders, including its use of long exposed assets.
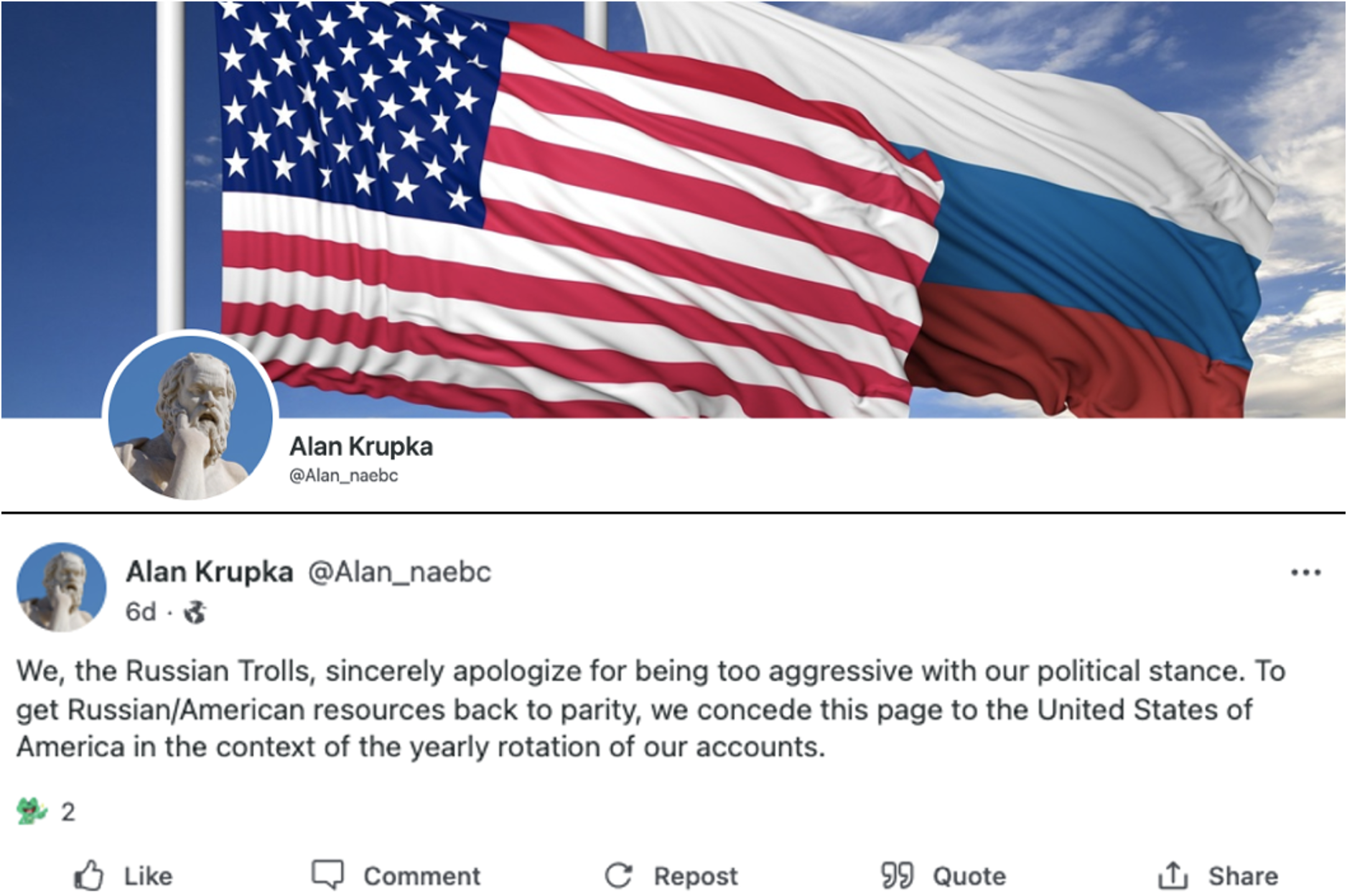
- After the elections, some of the personas posted and pinned an identical message to their accounts sardonically admitting to being “Russian Trolls.” One persona even changed their background image to one featuring a U.S. flag and a Russian flag (Figure 4).
- NAEBC personas also promoted content from a foundation explicitly linked to Yevgeniy Prigozhin, the IRA’s financier.
- On Nov. 7, the day before the elections, Prigozhin gave quotes cited by media indicating involvement in past and current election meddling efforts.
- Employing such conspicuous means for information operations may suggest that the campaign’s operators sought to give the impression of having influenced the elections, while expending more limited resources to do so.
Recent NAEBC Campaign Activity Consistent with That Previously Observed
While the apparent trolling by the campaign suggests an elevated brazenness, the campaign’s recent activity is consistent with that which we have previously observed.
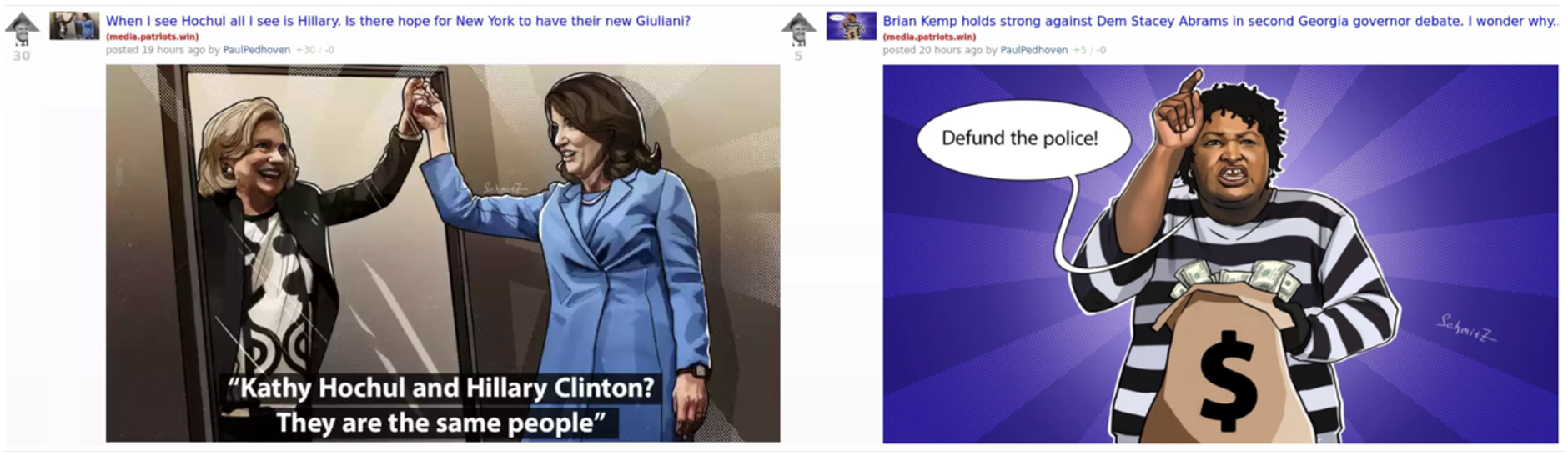
- NAEBC personas promoted political cartoons signed “Schmitz,” which targeted candidates in specific contested races. Such specific targeting may suggest a certain degree of sophistication in the campaign operators’ understanding of the U.S. political system (Figure 5).
- The promotion of “Schmitz” cartoons is characteristic of past NAEBC activity—we have not identified such a cartoonist elsewhere, and we are unable to confirm their identity.
- In October, we reported to customers that NAEBC personas had begun to consistently promote content published to the website Election Truth (electiontruth.net), noting that the newly created site had taken steps to obfuscate its origins. The website publishes content aligned with politically right-leaning audiences, including those pertaining to the midterm elections.
- We have insufficient evidence to attribute Election Truth to a specific actor, including the IRA. However, circumstantial considerations suggest it could be linked to NAEBC, including the alignment of the website’s creation date with the reactivation of multiple NAEBC personas, general overlaps in promoted narratives, and the campaign’s history of leveraging an inauthentic website to promote content.
Pro-PRC Information Operations Promote Narratives Surrounding Senators Rubio, Cruz; Highlight Politically Motivated Violence in the U.S.
As with Russia-aligned information operations that we identified targeting the midterms, pro-PRC activity included possible attempts at trolling researchers, as well as content pertaining to specific politicians, particularly Senators Marco Rubio and Ted Cruz.
DRAGONBRIDGE
In October, we reported on activity by the DRAGONBRIDGE information operations campaign, which we have judged to be operating in support of the political interests of the PRC, targeting the U.S. midterms, including content discouraging Americans from voting in the elections. We continued to observe DRAGONBRIDGE promoting election-related narratives in the months that followed, including those targeting specific politicians, as well as content focused on political issues relevant to the midterms, such as abortion rights and rising inflation.
Messaging Antagonistic Toward Senators Marco Rubio, Ted Cruz
Between Nov. 7 and Nov. 8, we observed DRAGONBRIDGE accounts post articles containing narratives antagonistic toward Senator Marco Rubio and Senator Ted Cruz. Notably, articles targeting both politicians were identical, and appeared to have been written with the intent to target Cruz and later repurposed to target Rubio. Articles aimed at Rubio replaced Cruz’s name with Rubio’s but did not change identifying biographical information specific to Cruz, such as phrasing describing the targeted individual as a Texas Senator born in Calgary.
- We identified articles alleging that the senators were “highly unhinged” politicians who constantly shirked responsibilities, were guilty of animal cruelty, and elicited “contempt and disgust” from the American public.
- The promoted articles alleged that Cruz or Rubio joined former President Trump in his attempts to overturn the 2020 presidential election results, but later “betrayed” him.
- One article alleged that disinformation and conspiracy theories promoted by U.S. politicians, such as those surrounding the attack on Paul Pelosi that the article falsely claimed were promoted by Rubio, could become a trigger for political violence ahead of the midterms.
Messaging Calling on Voters to Support Rubio Constitutes Possible Trolling
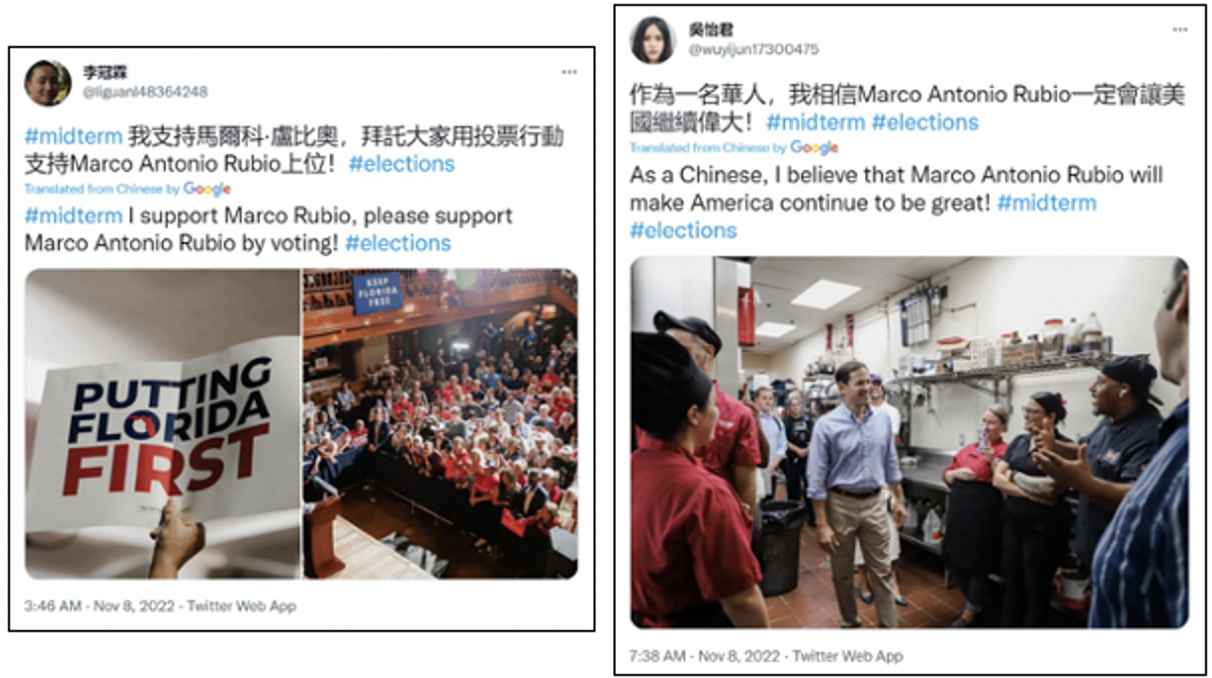
Conversely, between Nov. 8 and Nov. 9, we observed accounts we assessed with moderate to high confidence to comprise part of the DRAGONBRIDGE campaign posting Chinese-language messaging urging Floridians to vote for Senator Marco Rubio, along with the English-language hashtags #midterm and #elections, while a few of the same accounts were earlier observed occasionally promoting messaging antagonistic toward Rubio. Some of the accounts posted content self-identifying as ethnic Chinese individuals (Figure 6).
We surmise that given our observations of DRAGONBRIDGE activity posting negative content regarding Rubio, this activity may be an attempt by the campaign to sow discord among voters by advocating both for and against Rubio; alternatively, it is possible that the activity constitutes a degree of trolling on the part of the DRAGONBRIDGE campaign, given the PRC’s documented antipathy toward Rubio.
U.S. Political-Themed Narratives
A third set of DRAGONBRIDGE social media accounts continued to promote narratives pertaining to the midterms as well as broader U.S. political issues. Topics addressed included rising inflation, labor strikes, and abortion rights (Figure 7); and as we noted in previous reporting, the campaign has continued to highlight politically motivated violence in the U.S. One video posted by DRAGONBRIDGE accounts asserted that “vicious competition” between the two major political parties and the “increased tearing and antagonism in American society” have contributed to a surge in political violence, citing the attack on Paul Pelosi as an example; the video also claimed that the American public was losing confidence in the political system.

HaiEnergy
Websites we assessed to comprise part of the pro-PRC information operations campaign, HaiEnergy, published an article on Nov. 6 alleging that former White House Chief Strategist Steve Bannon was “deeply involved in the struggle between the two factions” in the 2022 U.S. elections. The article detailed Bannon’s legal issues and claimed that he would incite anger from individuals espousing far-right political stances in the upcoming elections. Since our initial public reporting on HaiEnergy in August 2022, a campaign that leverages a network of suspected inauthentic websites and a number of suspected inauthentic social media assets to disseminate content, we have identified additional websites that we assess to comprise part of this campaign, including those that published the article on Bannon.
Pro-Iran Activity Continues Plagiarizing Content from Mainstream Media Outlets
Previously identified Iranian and pro-Iran information operations targeting U.S. audiences have continued to disseminate content, including that aimed at the midterms. While their efforts do not appear to be particularly notable, such activity demonstrates that the actors behind these campaigns remain undeterred by takedowns and public exposure.
EvenPolitics
Mandiant previously identified and reported on the suspected inauthentic news site EvenPolitics, a site that appears primarily aimed at U.S. audiences, and assessed it and social media accounts promoting it to be operating in support of Iranian political interests. Since then, EvenPolitics has continued to publish election-related articles plagiarized from mainstream media outlets such as Business Insider, The Guardian, The Hill and Newsweek. Such articles included those pertaining to high-profile races in Michigan and Pennsylvania, as well as articles on other political topics such as the relationship between former U.S. President Trump and Florida Governor DeSantis and Trump’s role in the Republican Party.
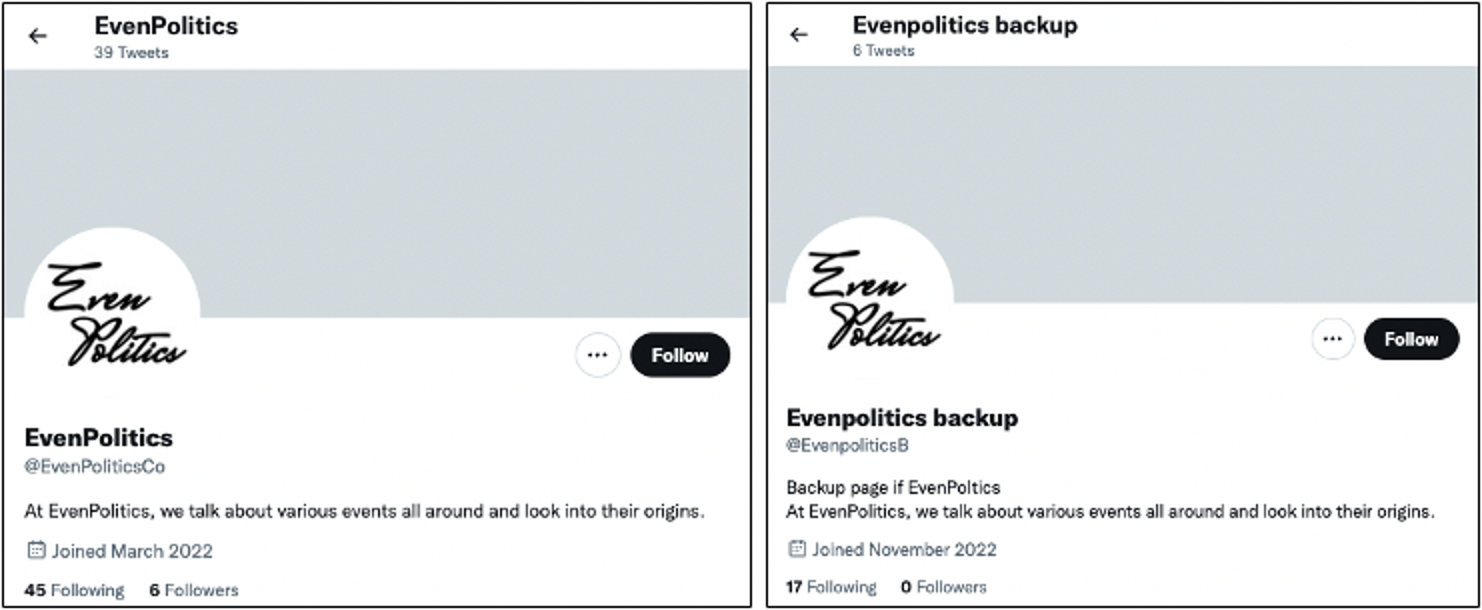
- While Twitter accounts we previously identified as associated with EvenPolitics had been suspended earlier in 2022, we subsequently identified additional accounts either self-associating with EvenPolitics or promoting those self-associated accounts (Figure 8). In the week prior to the elections, self-associated accounts began posting plagiarized content as well as a solicitation to “sign up as a writer” for the news outlet.
- In November 2022, the Election Integrity Partnership reported on data released by Twitter on information operations campaigns, including that tied to EvenPolitics, and stated that Twitter’s “release notes for researchers suggest that there were technical indicators tying the Twitter accounts to an Iran location.”
- We have also observed a Telegram channel named “Even Politics” link to the EvenPolitics website in its bio and promote EvenPolitics content, including through the U.S. election season; however, the channel’s content appears to have received minimal views.
Coordinated and Inauthentic Network of Pro-Iran Social Media Accounts
Separately, we observed a small amount of English-language content pertaining to the elections posted by social media accounts that we earlier identified and assessed be operating in a coordinated and inauthentic manner to promote narratives in support of Iranian political interests. These accounts comprised part of an activity set including inauthentic personas presenting as U.S.-based individuals, which have since been suspended. Accounts that remained live continued to post content in line with their personas, those of individuals espousing left-leaning political views. We previously observed personas in this activity set promoting content targeting both sides of the U.S. political spectrum, including that pertaining to specific politicians.
Outlook
The information operations Mandiant identified over the course of the 2022 U.S. election season did not generally appear to be significant in terms of their impact, although we note that measuring the effects of such activity is notoriously difficult. Nevertheless, in aggregate, such activity shows that U.S. elections not only continue to provide an attractive target for various state-aligned actors but are deemed to be within the acceptable risk threshold. Multiple information operations also involved flagrant activity seemingly intended to advance the narrative that foreign influence was occurring. Such intent underscores the importance of accurately qualifying the scale, scope, and possible effects of identified information operations, as to not aid actors in achieving their objectives.
