Insider Threat: The Dangers Within
What is an Insider?
Mandiant has adopted the Cyber and Infrastructure Security Agency (CISA) definition of insider, which states, “An insider is any person who has or had authorized access to or knowledge of an organization’s resources, including personnel, facilities, information, equipment, networks, and systems.” An insider threat is then the “potential for that insider to use their authorized access or special understanding of an organization to harm that organization. This harm includes malicious, complacent, or unintentional acts that negatively affect the confidentiality, integrity and availability of the organization, its data, personnel, facilities, and associated resource.”
Types of Insider Threats
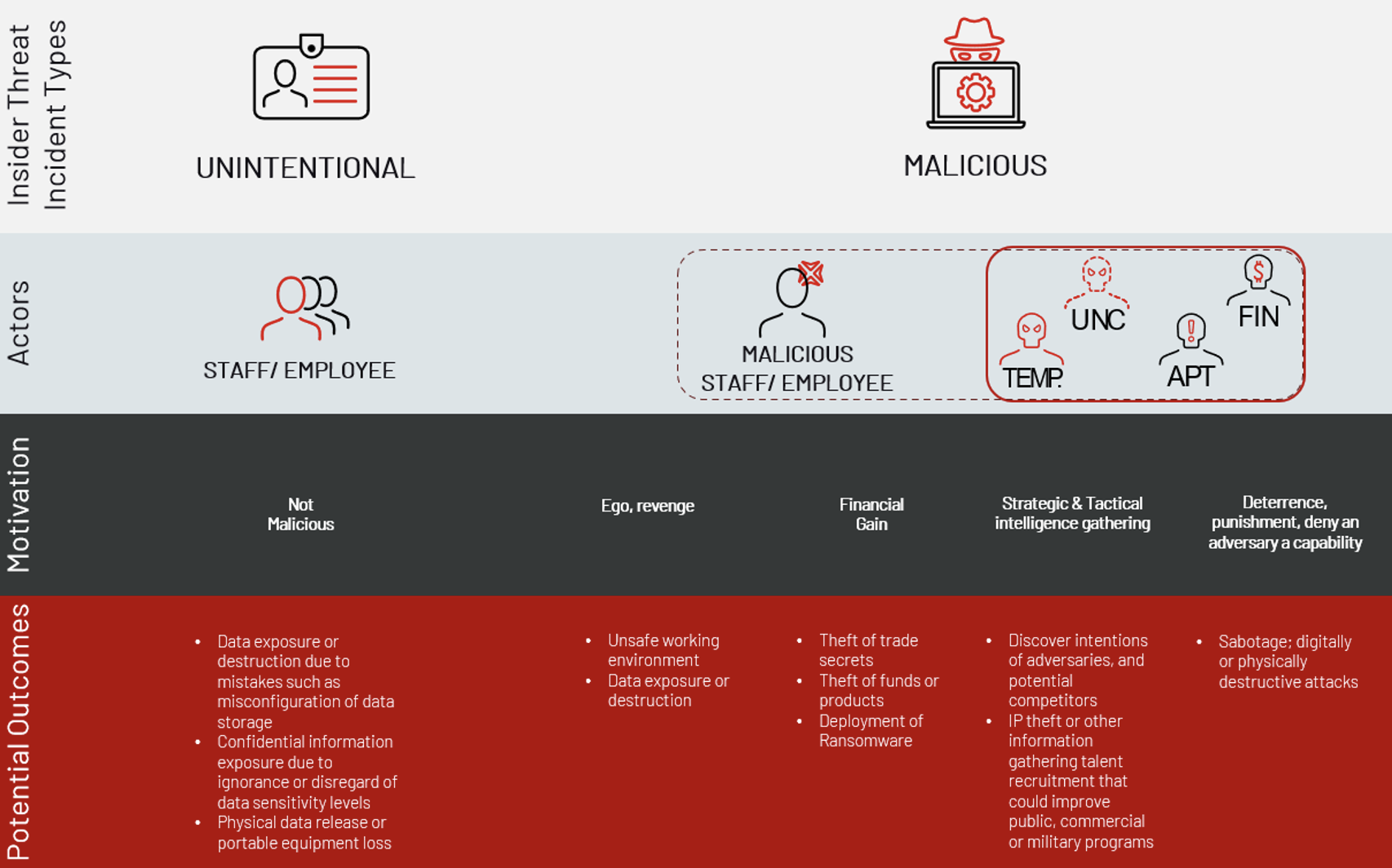
Mandiant defines insider threat incidents in two specific categories: unintentional, and malicious.
Unintentional insider incidents are where harm to an organizations’ resources is inflicted by the careless, negligent, or reckless actions of a current or former employee, contractor, or any other entity associated with the organization and who has or had access to these resources. These actions, while not malicious, can result in data exposure or destruction due to mistakes such as misconfiguration of data storage, confidential information exposure due to ignorance or disregard of data sensitivity levels, physical data release or portable equipment loss, etc.
Malicious insider incidents are where harm to an organizations’ resources is caused by someone who maliciously and intentionally abuses their access for personal benefit. These are often noted to be employees who have been influenced by external factors, for example, threat actors incentivizing employees for providing access to the environment; or employees who hold a grudge against a current or former employer and seek revenge, or employees who are seeking financial gain through intellectual property theft or espionage.
Why Insider Threat is a Concern
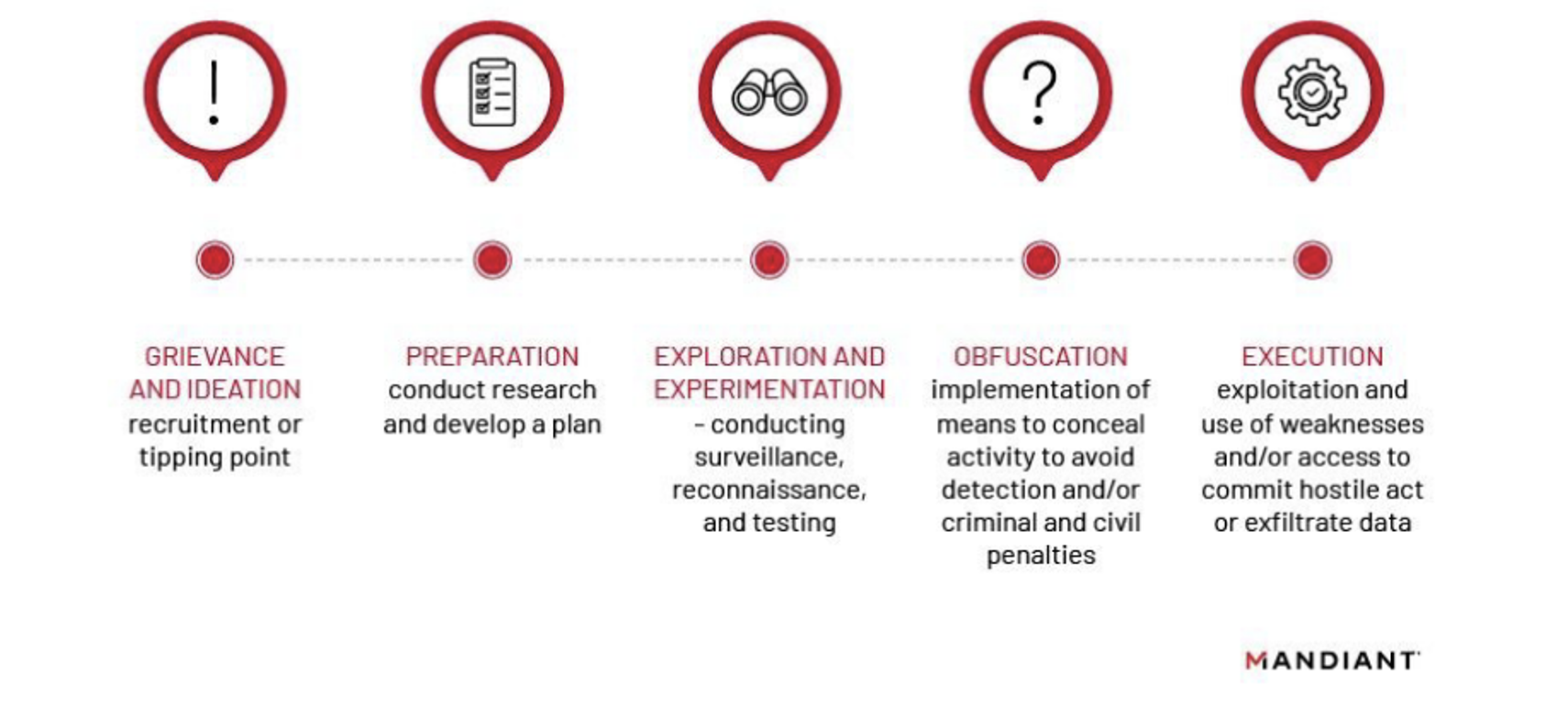
The increasing amounts of information being stored on internal networks, the cloud and portable devices has increased the risk of a well-placed insider threat. The legitimate permissions granted to employees, contractors and other third parties as part of day-to-day business operations certainly make some of this activity more difficult to detect. Malicious insider operations are often carried out over time, with the insider taking steps to try and hide their malicious activity and remain undetected in the victim environment. As a result, the difficulty in identifying insider threats allows many incidents to go undetected and unreported. Therefore, a thorough understanding of a user’s normal baseline activity is required to identify the abnormal, malicious patterns.
As organizations have continued refining their defense in depth approach to security, attackers are evolving and targeting those with access such as the employees.
In the past year, per the Mandiant M-Trends 2022 report, the Global Median Dwell time, which is calculated as the number of days an attacker is present in a victim environment before they are detected, has decreased from 48 days to 36 days. While organizations mature their security programs and external entities provide more notifications of intrusions to the organizations, an expected outcome would be a decrease in the time to contain an insider threat. However, the opposite has been observed as the time required to contain an insider threat has continued to increase over the past four years, from 72 days on average in 2018 to 85 days in 2022 as per the 2022 Ponemon Cost of Insider Threats Global Report.
Also, if not addressed promptly, insider threat-related incidents can become costly for an organization. In the Ponemon insider report, incidents that took less than 30 days to contain had the average annual cost of activities at $11.23 million USD. In contrast, average annual activity costs for incidents that took more than 90 days was $17.19 million USD. Companies in North America experienced the highest total cost at $17.53 million USD, followed by European companies having the next highest cost at $15.44 million USD.
Mandiant Insider Threat Service Offerings
Mandiant provides protection against insider threats for all stages of the attack lifecycle. Details available on our insider threat Security Services page.
