Smarter, Not Harder: How to Intelligently Prioritize Attack Surface Risk
There’s a common saying in cyber security, “you can’t protect what you don’t know,” and this applies perfectly to the attack surface of any given organization.
Many organizations have hidden risks throughout their extended IT and security infrastructure. Whether the risk is introduced by organic cloud growth, adoption of IoT devices, or through mergers and acquisitions, the hidden risk lies dormant. As a result, IT and security teams do not always have an up-to-date picture of the extended ecosystem they need to defend. Legacy tools often have static lists of the ‘known’ asset inventory but lack the capabilities to comb the internet for the ‘unknown’ assets that belong to the organization.
To close visibility gaps and uncover hidden risk, establishing and maintaining a comprehensive attack surface management program is critical. Benefits include removing sprawl, reducing environmental drift and fast remediation.
Gaining visibility into the attack surface is step one in mitigating risk. Next comes enumerating vulnerabilities and prioritizing remediation and hardening. A recent evaluation of enterprise attack surface trends gathered by Mandiant Advantage Attack Surface Management revealed over six million security issues were identified from January 1, 2022, to June 30, 2022. At first glance, six million security incidents seems like a huge number; however, a security team doesn’t need to run a fire drill for each one. Of the six million, ~1% were critical and high severity issues. Said another way, security teams really only need to focus on 1% of security issues, but how can they know which ones are most critical?
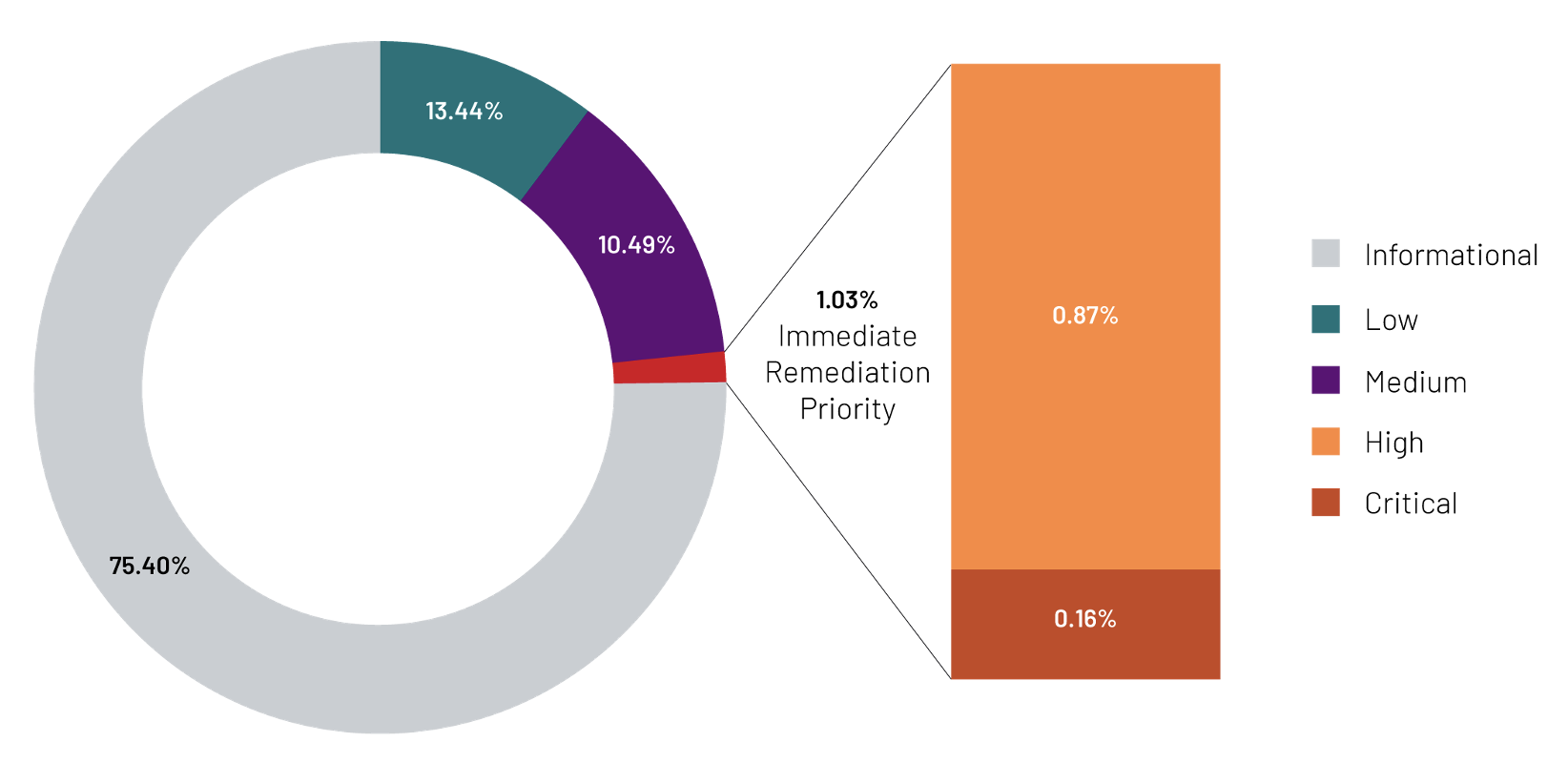
Know Which Assets Are Most Likely to be Exploited for Faster Remediation
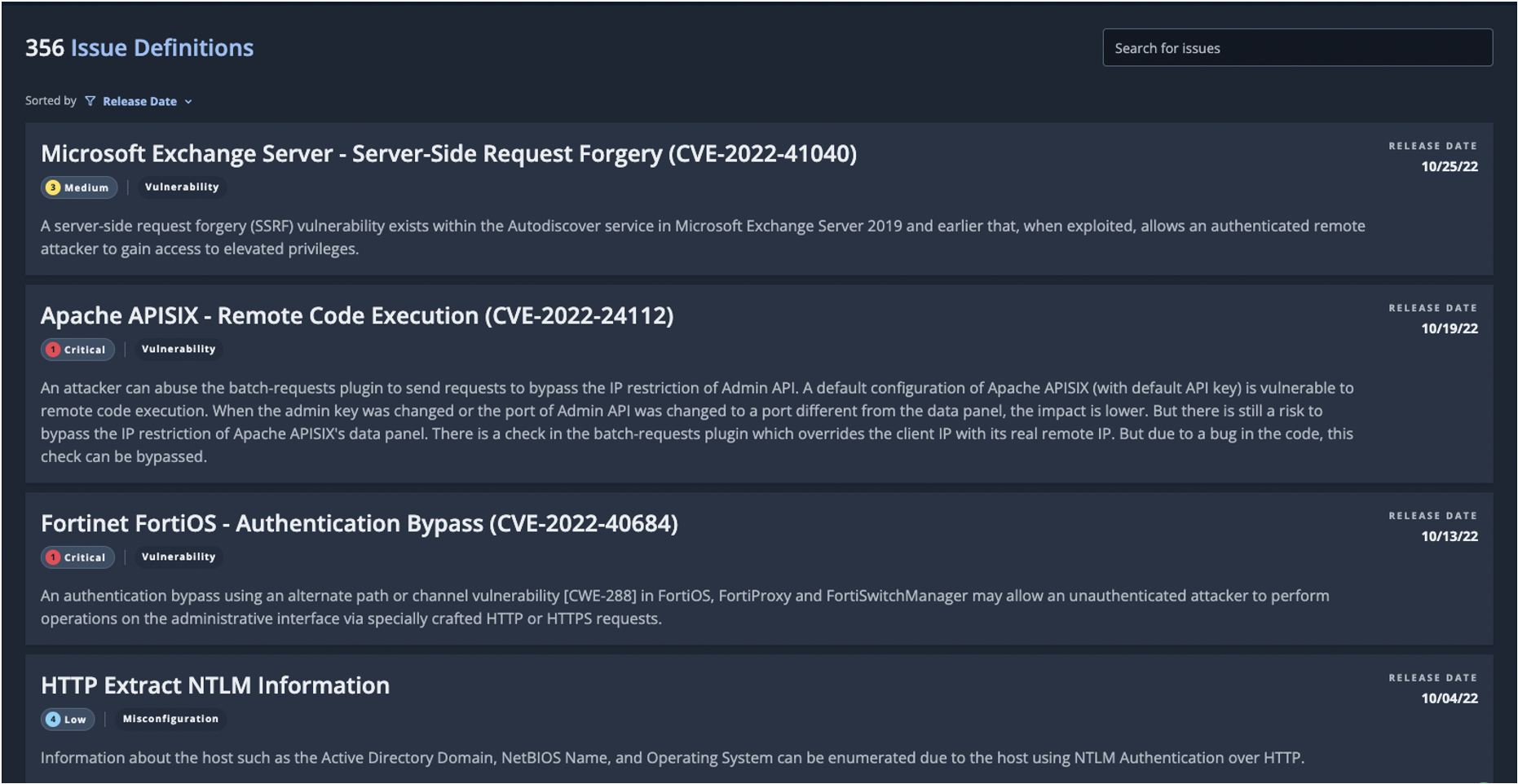
Mandiant Advantage Attack Surface Management (ASM) directly applies Mandiant’s industry-leading frontline Threat Intelligence to assets discovered around customers’ ecosystems. By applying threat intelligence directly to the attack surface of customers, they can identify the assets most likely to be exploited within their specific industry for improved prioritization. Specifically, intelligence gathered from the frontlines of incident response, managed services, and adversary research is used to create checks that validate when assets are vulnerable or exposed to exploitation seen in the wild.
As zero-days are disclosed or new information comes to light, Mandiant creates vulnerability reports and new asset checks, so customers know where their assets are in the extended ecosystem and when they present risk to the organization.
ASM starts with simple information about the organization, (e.g., a domain, known networks, or SaaS accounts), then collects asset and exposure information about an organization’s distributed global infrastructure like an attacker would. The solution then performs exhaustive discovery by scanning externally facing assets and cloud resources daily to identify software, architecture, and configuration risks to your organization. In addition to the direct integration with Mandiant Advantage Threat Intelligence, ASM aligns to the NIST National Vulnerability Database (NVD) and CISA’s Known Exploited Vulnerability catalog.
Here are some benefits of enriching attack surface insights with intelligence:
- Know which assets are most likely to be exploited by threat actors
- Get expert crafted asset checks and vulnerability reports curated by analysts
- Prioritize remediation and hardening efforts
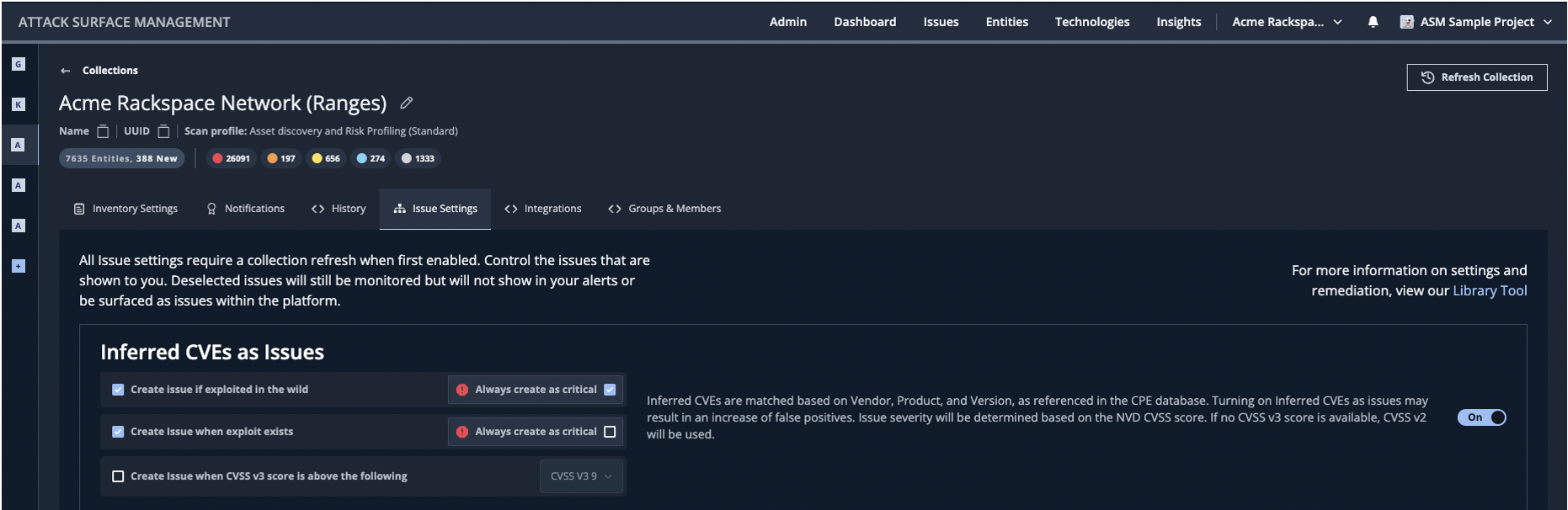
Overlaying threat intelligence into attack surface insights can reveal prioritization and remediation efforts. For the most efficient prioritization, security professionals should map threat intelligence to discovered assets, helping to identify and prioritize critical and high severity issues or suspicious activity. Partnering with a provider that overlays assets with indicators of compromise (IOCs), adversary research, and intelligence from deep and dark web monitoring informs the security team of malicious activity involving the brand or an asset before threat actors achieve their mission.
Mitigating the impact of vulnerable or exposed assets is crucial and requires a strategic approach to prioritization. The following are considerations for prioritization:
- Asset Criticality: How mission critical is this asset to the organization’s revenue streams, brand reputation and customer trust?
- Threat Actor TTPs & Targeting: Who is targeting others in the industry and how are they doing it?
- Exploitation Status: Is there exploitation in the wild or does an exploit code for a CVE exist?
- Risk Tolerance: What is the risk threshold set by security, risk and compliance leaders and does an uncovered vulnerability exceed the threshold?
By enriching assets with intelligence early in the discovery process, security teams are able to focus remediation and hardening efforts on the entry points and assets that present the most risk.
For expert guidance on prioritizing attack surface risk at scale, watch this on-demand webinar.
