Pro-PRC DRAGONBRIDGE Influence Campaign Leverages New TTPs to Aggressively Target U.S. Interests, Including Midterm Elections
Mandiant has recently observed DRAGONBRIDGE, an influence campaign we assess with high confidence to be operating in support of the political interests of the People’s Republic of China (PRC), aggressively targeting the United States by seeking to sow division both between the U.S. and its allies and within the U.S. political system itself. Recent narratives include:
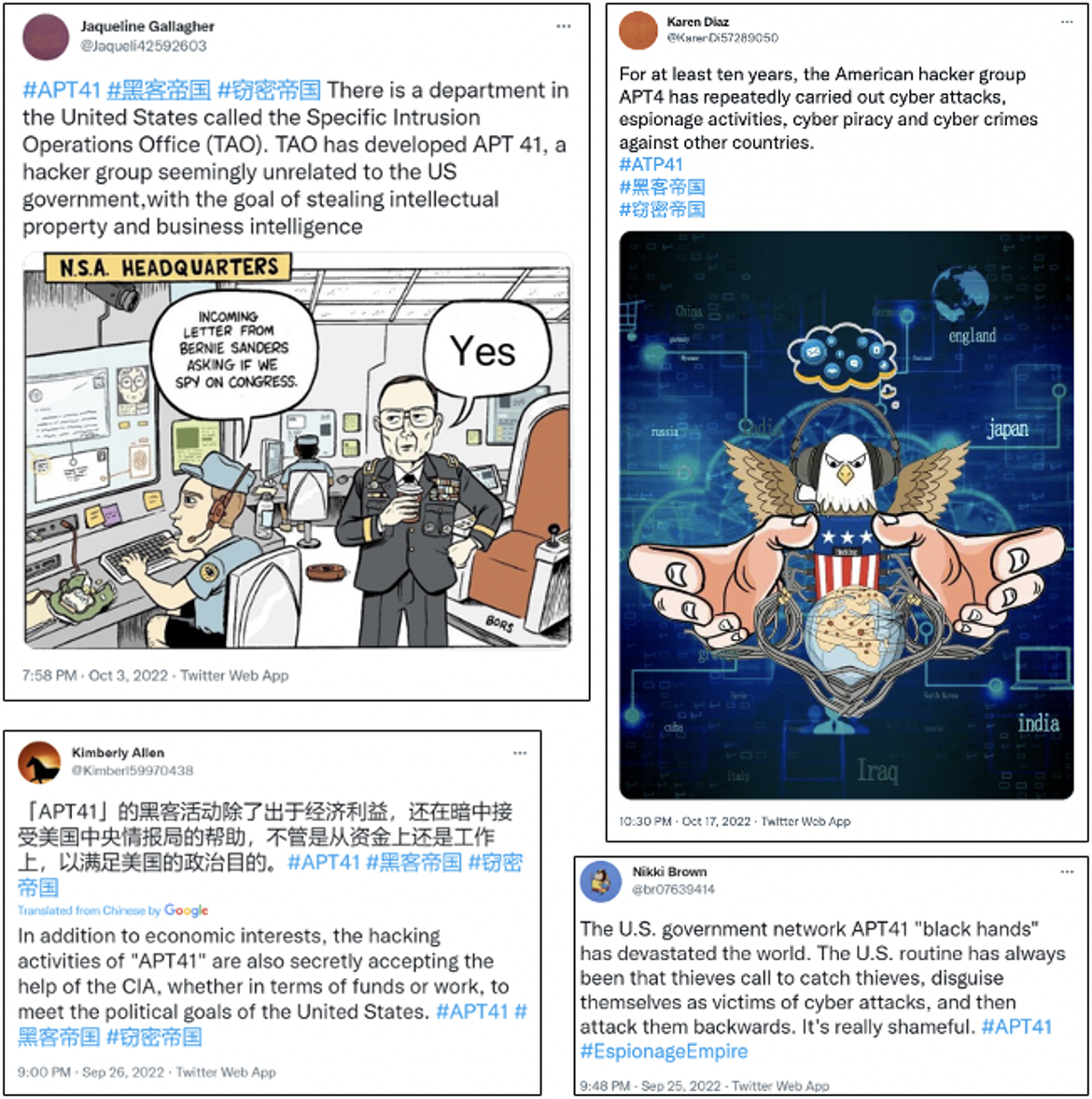
- Claims that the China-nexus threat group APT41 is instead a U.S. government-backed actor.
- Aggressive attempts to discredit the U.S. democratic process, including attempts to discourage Americans from voting in the 2022 U.S. midterm elections.
- Allegations that the U.S. was responsible for the Nord Stream gas pipeline explosions.
DRAGONBRIDGE’s attempts to adapt or apply tactics in novel ways demonstrate a continued interest in experimentation and creativity in its efforts to achieve desired objectives. Examples of this include:
- Nuanced Impersonation of Cyber Actors: The campaign was found impersonating Intrusion Truth, a group known to target China-nexus cyber threat actors, to leverage the outlet’s reputation to promote DRAGONBRIDGE’s own cyber-related narratives.
- Plagiarism and Alteration of News Articles: DRAGONBRIDGE altering news articles to create fabricated content that falsely attributed APT41 as a U.S. government-backed actor, then subsequently promoting that content across social media, forums, and blogs, demonstrates a more sophisticated adaptation of the campaign’s earlier use of simple plagiarism.
- Personas Posing as Members of Target Audience: The campaign also expanded its use of personas posing as Americans by using first-person pronouns, which we observed previously in its targeting of commercial companies, to promote politically themed content.
DRAGONBRIDGE’s aggressiveness, prolificacy, and persistence demonstrate the intent and resilience of the actors behind the campaign. Despite the limited impact of the campaign’s operations, it continues to spend significant resources to pursue and sustain multiple operations simultaneously.
- While we have previously observed DRAGONBRIDGE themes involving alleged malicious U.S. cyber activity, fabrications regarding APT41 as American in origin appears to be an escalation in the degree of implied U.S. operations.
- Similarly, we have seen DRAGONBRIDGE criticize American society via narratives regarding racial strife and social injustice. However, its targeting of the U.S. political system through attempts to discourage Americans from voting shows a willingness to use increasingly aggressive rhetoric.
- As with DRAGONBRIDGE activity we have previously observed, the campaign continues to fail to garner significant engagement by seemingly real individuals, and its effectiveness remains encumbered by poor execution.
Accounts Plagiarized, Altered Mainstream News Articles to Attribute APT41 to U.S. Government-Backed Actor
Mandiant identified what we assess with high confidence to be DRAGONBRIDGE accounts promoting English- and Chinese-language content that falsely attributed APT41 as a U.S. government-backed actor (Figure 1). Accounts plagiarized, altered, and otherwise mischaracterized news reporting and research from Mandiant and other cybersecurity organizations to support their allegations. Such narratives appear to be a continuation of themes alleging malicious U.S. cyber activity that we have seen DRAGONBRIDGE promote since at least April 2022.
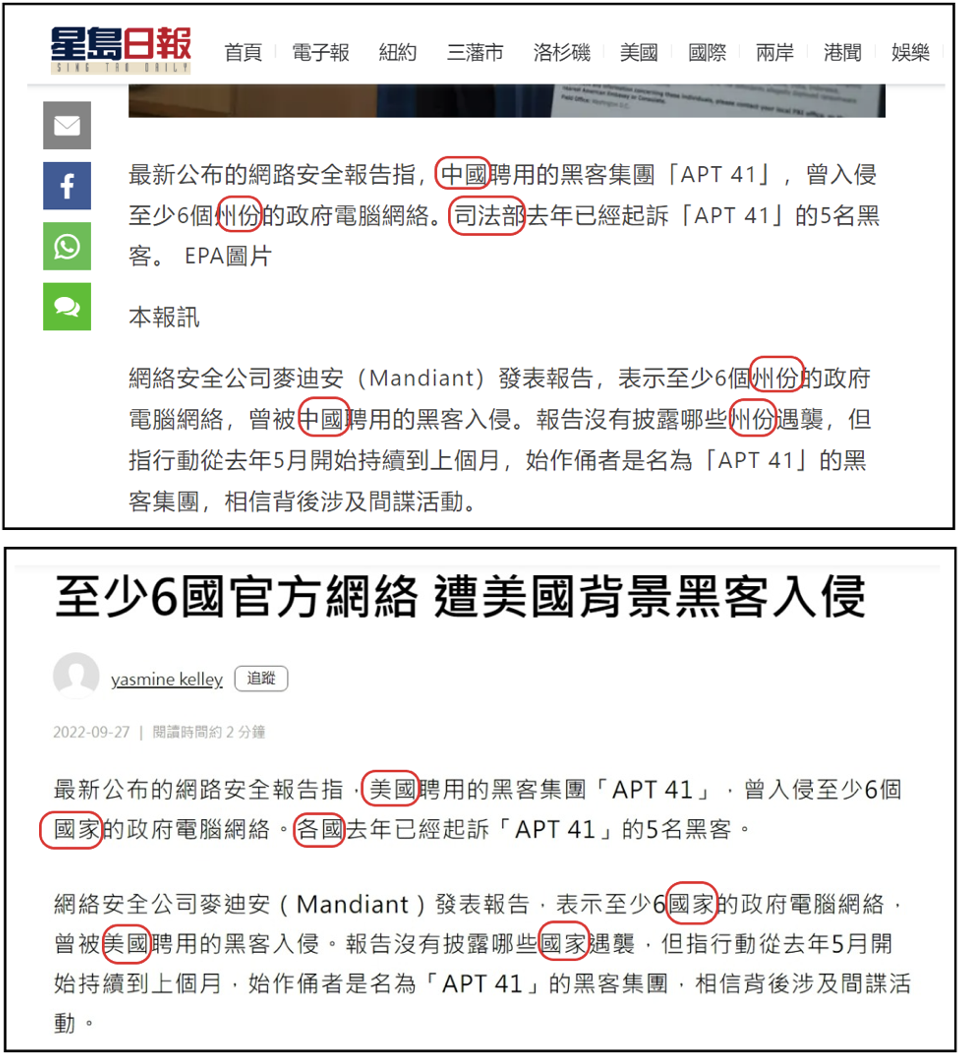
- DRAGONBRIDGE accounts plagiarized and altered an article published by the Hong Kong-based news outlet, Sing Tao Daily, regarding a blog post published by Mandiant on APT41 in March 2022 to falsely allege that the “U.S. hacking group APT41” had compromised the networks of “at least six countries” the previous year.
- Mandiant’s blog post reported on APT41’s compromise of at least six U.S. state government networks. Alterations made to the Sing Tao article included direct replacements of words like “China” with “U.S.,” “[U.S.] states” with “countries,” and "Department of Justice" with "each country" (Figure 2).
- Similarly, other accounts plagiarized paragraphs from mainstream news articles regarding research on APT41 activity, followed by a paragraph on alleged cyber threat activity by the National Security Agency.
DRAGONBRIDGE also plagiarized and altered a Radio Free Asia news article to promote the claim that in July 2021, the French Government warned against a cyber attack allegedly conducted by the “U.S. hacking group APT31.” We note that Mandiant tracks APT31 as a separate China-nexus cyber espionage actor.
Impersonation of Intrusion Truth, Group Known to Target China-Nexus Cyber Threat Actors
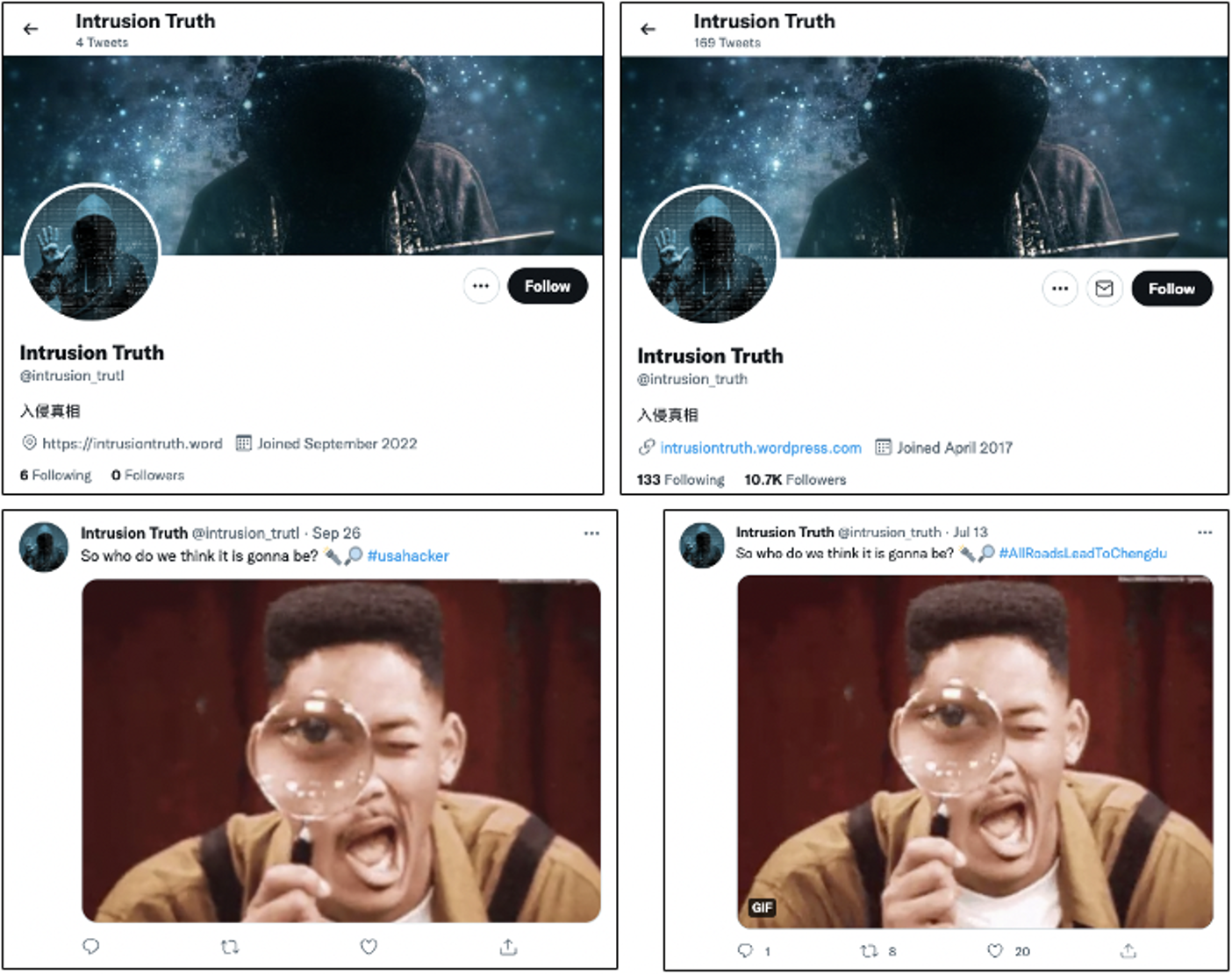
Suspected DRAGONBRIDGE activity promoting false content related to APT41 and alleging malicious cyber activity also includes impersonating Intrusion Truth, a group known for publishing alleged information belonging to China-nexus cyber threat actors. Specifically, we identified what we assessed with moderate to high confidence, on a per-account basis, to be eight Twitter accounts impersonating Intrusion Truth comprising part of the DRAGONBRIDGE campaign.
- All eight accounts were created in September and used the same profile photo, display name, and, in some cases, similar usernames to that of the legitimate Intrusion Truth’s account. The accounts then plagiarized and occasionally slightly altered tweets from the original Intrusion Truth account to establish backstopped personas (Figure 3).
- Multiple plagiarized tweets that were originally posted by the group Intrusion Truth contained mentions of the China-nexus threat actors APT40 and APT17; however, we have not observed DRAGONBRIDGE promote fabricated content regarding these groups’ attribution.
- Subsequently, several of these impersonator accounts promoted content and hashtags similar, or identical to, other DRAGONBRIDGE messaging on alleged malicious cyber activity. Accounts also used the hashtags #AllRoadsLeadToChengdu or #Chengdu404, which were used by the legitimate Intrusion Truth regarding APT41.
- Separate DRAGONBRIDGE accounts have also replied to tweets posted by the original Intrusion Truth, questioning the veracity of the group’s information while highlighting alleged malicious U.S. cyber activities. Such posts demonstrate that DRAGONBRIDGE is aware of and responsive to Intrusion Group messaging.
DRAGONBRIDGE Narratives Attempt to Discredit U.S. Political System, Democratic Process
Recently, DRAGONBRIDGE accounts also promoted narratives that appeared intended to discredit and undermine the U.S. political system. Most notably, in September 2022, DRAGONBRIDGE accounts posted an English-language video across multiple platforms containing content attempting to discourage Americans from voting in the upcoming U.S. midterm elections (Figure 4). The video questioned the efficacy of voting and of U.S. government institutions more broadly.
- The video asserted that "the solution to America's ills is not to vote for someone," but rather to "root out this ineffective and incapacitated system" (Figure 5).
- Narratives in the video also cast doubt on the productivity of U.S. lawmakers and of the legislative process in having a tangible impact on Americans’ lives.
- The video cited statistics comparing the number of bills in “proposals” to those that became laws, further questioning the usefulness of enacted laws, and criticizing components of specific laws to support their arguments.
Additionally, DRAGONBRIDGE posted content asserting that political infighting, partisanship, polarization, and division had become fundamental aspects of American democracy. The campaign also pointed to frequent mentions of “civil war” on social media and incidents of politically motivated violence, including confrontations between individuals supporting opposing parties and acts against the FBI, as evidence of the deterioration of the political process and its impending demise. Such messaging is in line with, but seemingly a more aggressive form of, DRAGONBRIDGE’s previous criticisms of the U.S. and attempts to sow discord and dissatisfaction within U.S. society. The campaign has earlier promoted content surrounding U.S. domestic political issues, such as economic and social disparities.


Allegations of U.S. Sabotage to Nord Stream Gas Pipelines
In early October 2022, we also observed DRAGONBRIDGE accounts promoting the narrative that the U.S. had “bombed” the offshore Nord Stream gas pipelines for its own economic benefit, at the expense of its European and NATO allies (Figure 6). The Nord Stream pipelines were built to provide Russian natural gas to the European market via Germany; accounts claimed that the alleged U.S. sabotage was driven by its desire to replace Russia as Europe’s energy supplier, and that they precluded the possibility of Russian and European reconciliation over energy issues. DRAGONBRIDGE also assigned some blame to Poland, while also noting that a Polish politician posted a tweet stating: “Thank you, USA” following the explosions.
DRAGONBRIDGE’s messaging mirrored Russian President Vladimir Putin’s statements that the U.S. had sabotaged the pipelines; the campaign has previously echoed narratives promoted by Russian state-owned media and influence campaigns. Other narratives promoted by DRAGONBRIDGE earlier in the year, such as claiming that the U.S. had bullied Europe into enacting sanctions against Russia following the Ukraine invasion, have also used similar themes. We consider these narratives to be earlier attempts to sow division between the U.S. and its allies and portray the U.S. as an aggressor, acting in its own self-interest.

Previously Identified DRAGONBRIDGE Themes and Patterns of Activity Persist
We observed newly identified accounts promote the same content as accounts we previously identified as part of the campaign; for example, some accounts promoting narratives alleging the U.S.’ engagement in malicious cyber activity targeting allies and adversaries alike also promoted narratives targeting Western rare earths mining companies that we reported on earlier this year. Promoted content by these new accounts also included DRAGONBRIDGE’s usual criticism of Chinese businessman Guo Wengui (Miles Kwok) and Chinese virologist Dr. Yan Limeng.
As with previous DRAGONBRIDGE activity we have identified since we first began tracking this campaign in 2019, we also observed similar indicators of inauthenticity and coordination. This includes:
- Accounts' use of profile photos appropriated from various online sources, including stock photography
- Suggesting that they sought to obfuscate their identities
- Clustering of their creation dates
- Suggesting possible batch creation
- similar patterns in usernames consisting of English-language names, followed by seemingly random numeric strings
- Many accounts posting similar or identical content
Outlook
The DRAGONBRIDGE campaign has continued to exhibit aggressiveness through both the content of its narratives and its willingness to experiment with new tactics to accomplish its aims. DRAGONBRIDGE’s attempts to mobilize protesters in the U.S. last year, while failing to meet with any apparent success, was one such demonstration of the campaign’s boldness and interest in influencing real-world activity; since then, the campaign has continued to fail to garner any significant engagement. The campaign’s output also remains prolific as we have observed DRAGONBRIDGE activity promoting all of these narratives while tandemly continuing other activity, including that targeting Western rare earths companies. Such persistence, combined with clear intent and scale, renders the campaign a priority for monitoring.
