New Mandiant Threat Intelligence Integrations for MISP, Splunk SIEM and SOAR, and Cortex XSOAR by Palo Alto Networks
Security professionals are often overwhelmed by the number of management consoles or platforms they need to jump between on any given day. Automating and sharing information into existing workflows can unburden these teams by eliminating mundane tasks and reducing human error.
Mandiant SaaS integrations save time and help make security teams more proactive. The Mandiant Threat Intelligence API allows security teams to integrate Mandiant Threat Intelligence data directly into their existing security tools and workflows.
As part of our ongoing commitment to helping security teams work more efficiently with their tools of choice, we are launching new integrations for MISP, Splunk SIEM and SOAR, and Cortex XSOAR. These integrations provide customers with improved situational awareness and threat detection, helping them be more proactive in protecting against cyber attacks.
Customers benefit from:
- Improved situational awareness: Use Mandiant Threat Intelligence in the context of their own environment, providing them with a more complete picture of the threat landscape.
- Reduced risk: Automate response actions, reducing the risk of human error.
- Improved efficiency: Save time and resources by automating tasks leveraging the latest intelligence.
- Improved Operationalization: Leverage threat intelligence across existing workflows to simplify protection and be more proactive.
MISP
The new integration with MISP, a leading open-source threat intelligence platform, provides a more efficient way to surface Mandiant Threat Intelligence, making it easier for security teams to consume and take action.
The integration creates MISP events from Mandiant finished threat intelligence reports, and builds galaxy clusters for each threat actor and malware family. This allows security teams to quickly see how different threats are related to each other, and to identify potential attack vectors. The integration also adds indicators of compromise (IOCs) associated with reports to each event as MISP attributes / objects, providing security teams with more context about each threat.
Splunk SIEM
Mandiant expanded the existing integration with Splunk SIEM to include:
- New Mandiant Indicator | Event matching feature: The new Mandiant Indicator | Event matching feature allows you to match Mandiant indicators to events in your Splunk SIEM environment. This can help you to identify potential threats that may not be otherwise detected. You can also tune the settings for this feature to create Notable Alerts for specific types of matches.
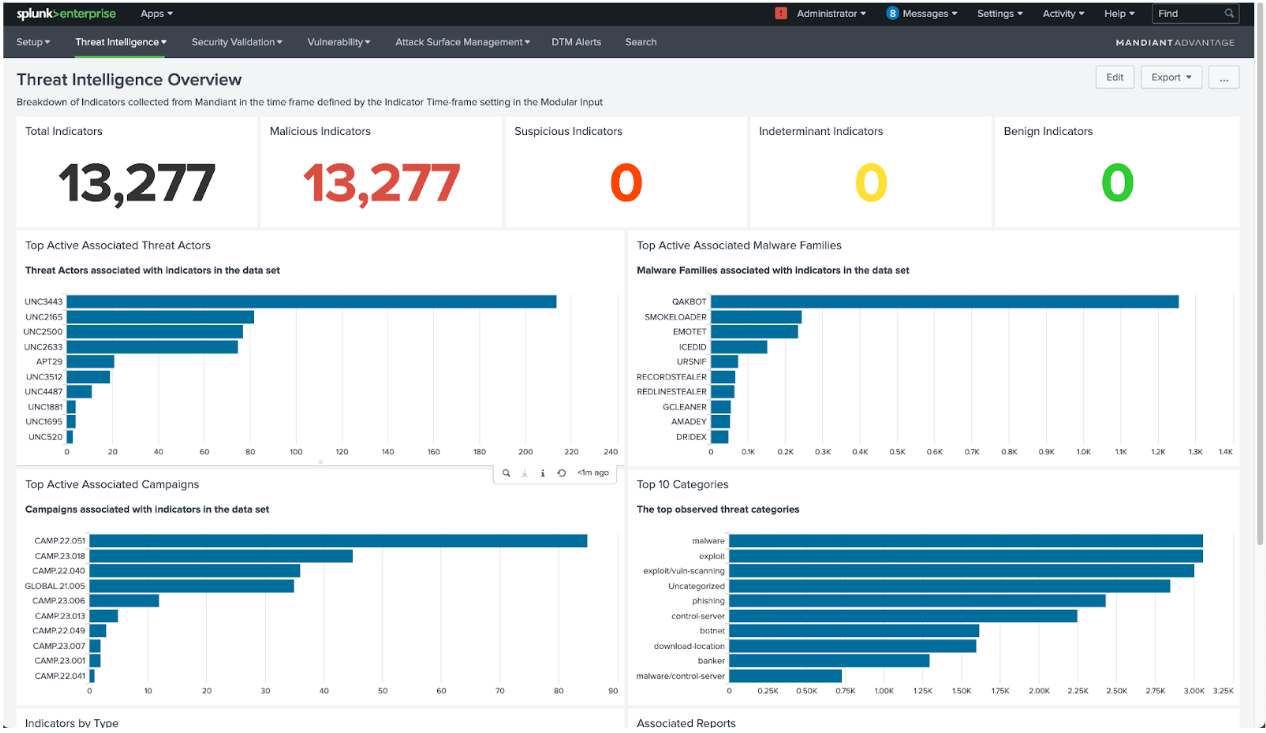
- Improved Threat Intelligence Overview dashboard: The updated Threat Intelligence Overview dashboard provides more context about the Mandiant indicators that are being ingested into your Splunk SIEM environment. This includes information about the active malware families, threat actors, campaigns, and reports that are linked to these indicators.
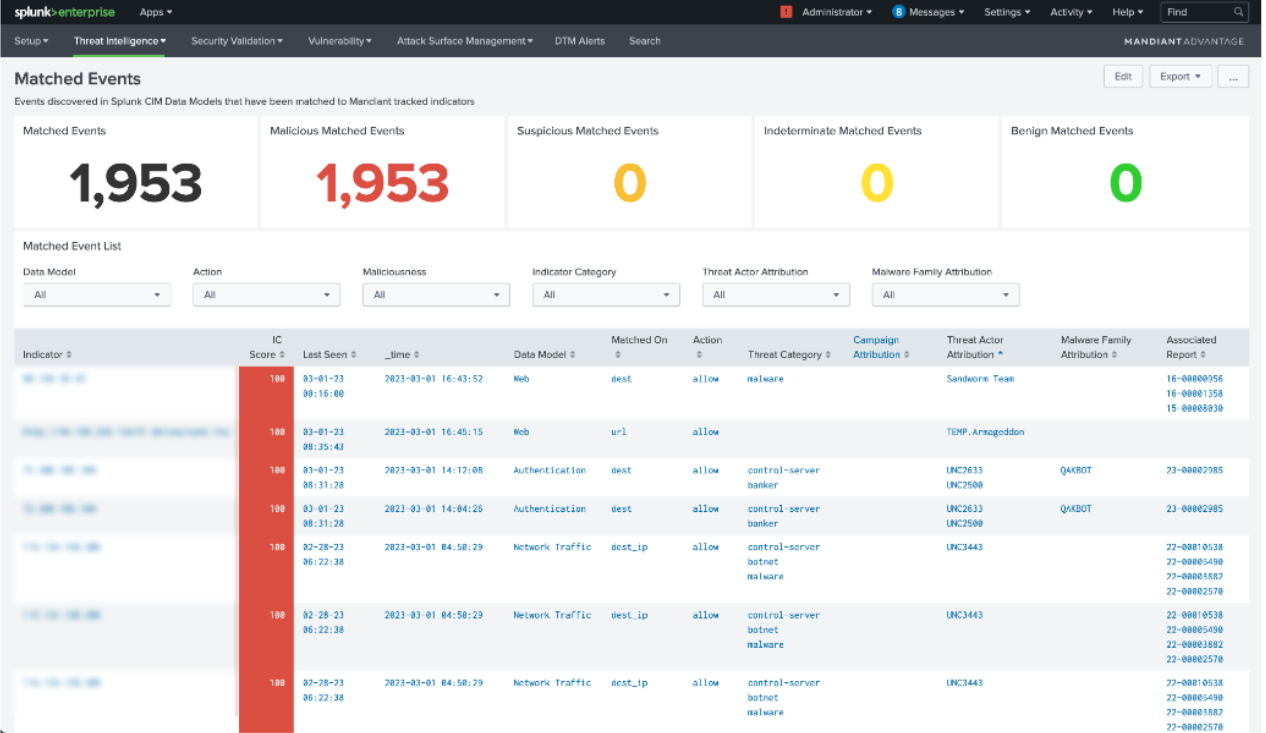
- New Mandiant Matched Events dashboard: The new Mandiant Matched Events dashboard provides more context about the events that have been matched to Mandiant indicators. This includes information about the maliciousness, source data model, indicator category, event action, attributed malware family / threat actor, and more.
- Added support for associated campaigns and threat intelligence reports: We have added support for associated campaigns and threat intelligence reports for ingested indicators. This can help you to better understand the context of each indicator and to identify potential threats.
Mandiant Integration with Splunk SOAR, and Cortex XSOAR by Palo Alto Networks
We are excited to announce the integration of Mandiant with Splunk SOAR and Cortex XSOAR. These integration will provide organizations with a powerful way to automate and orchestrate security workflows, accelerate incident response, and improve their security posture.
By combining, automating and orchestrating security workflows with the latest Mandiant Threat Intelligence, Splunk SOAR and Cortex XSOAR can help organizations to reduce the time it takes to respond to threats, improve the accuracy of responses, and free up security analysts to focus on more strategic tasks.
The Mandiant Threat Intelligence SOAR integration provides a number of benefits, including:
- On-demand enrichment for indicators: Discover details about an indicator of compromise, based on the value of the indicator. An indicator can be specified by URL, FQDN, IP Address, or File Hash (MD5/SHA1/SHA256). This information can be used to improve the accuracy of threat assessments and to identify potential threats.
- Correlate details of associated actors, campaigns and malware: This information can be used to improve the understanding of the threat landscape and to identify potential threats.
- Retrieve Mandiant vulnerability details and their associations: Lookup detailed information about vulnerabilities being actively exploited in the wild, also get unique insights on what vulnerabilities are being used by attackers in impactful breaches around the world.
- Review associated finished intel reports within the SOAR console: This enables analysts to access detailed Threat Intelligence, optimize their workflow and perform further contextual analysis without leaving their application.
Using Intelligence
Mandiant believes these integrations will provide organizations with a powerful way to automate and orchestrate security workflows, accelerate incident response, and improve security posture. Learn more about these and other Mandiant Threat Intelligence integrations.
