The Cyber Risk Journey, Part Two: What Matters Most?
Between a steady stream of breaches and ongoing global events, the last few years has seen the threat landscape move into uncharted territory. As organizations continue to adjust to a shifting landscape, threat actors are also adjusting.
Cyber security teams have the unprecedented task of both supporting the business with day-to-day operations and being constantly prepared for attackers in their environment. Balancing the criticality of operational responsibilities with response preparedness is a difficult trade off, and even with the best teams, things sometimes go wrong.
As teams work to maintain a balance between enabling their business while maintaining enterprise safeguards, they often find themselves struggling to keep pace, and the desire to treat all things equal quickly becomes a losing battle. In our security predictions report, 14 Cyber Security Predictions for 2022 and Beyond, we discussed ransomware actors increasing both tempo and focus by applying additional pressure via extortion—with pressure increasing if critical systems are at risk.
Learning from impacted peers and high-profile incidents in the media, executive leadership teams and boards of directors are taking better steps to understand where their largest exposures reside, and how best to close the security gaps that attackers continually look to exploit. Some organizations have come to realize that a “Crown Jewels” approach to security helps strengthen overall posture by focusing on protecting assets most critical to the business—and likely most attractive to attackers.
This means better risk management, resourcing and investment decision making around high-value assets, and better prevention against those incidents that could hurt the most. However, selecting these assets can be a challenge—after all, isn’t every workstation, server, and bit of data within an organization critical?
Designing a Crown Jewels Program
When designing a Crown Jewels approach, we suggest starting with four key areas. These should then be used to pivot deeper into understanding the details around the potential strengths and weaknesses surrounding critical assets:
| Identify |
|
| Threats |
|
| Vectors |
|
| Countermeasures |
|
Taking a Crown Jewels approach provides organizations with a unique perspective outside of technology that increases visibility into the business, improves leadership commitment to protecting information assets, and aligns priorities across the organization.
When organizations make the conscious decision to develop or advance their security program towards more precision and risk aligned practices, we recommend the following process:
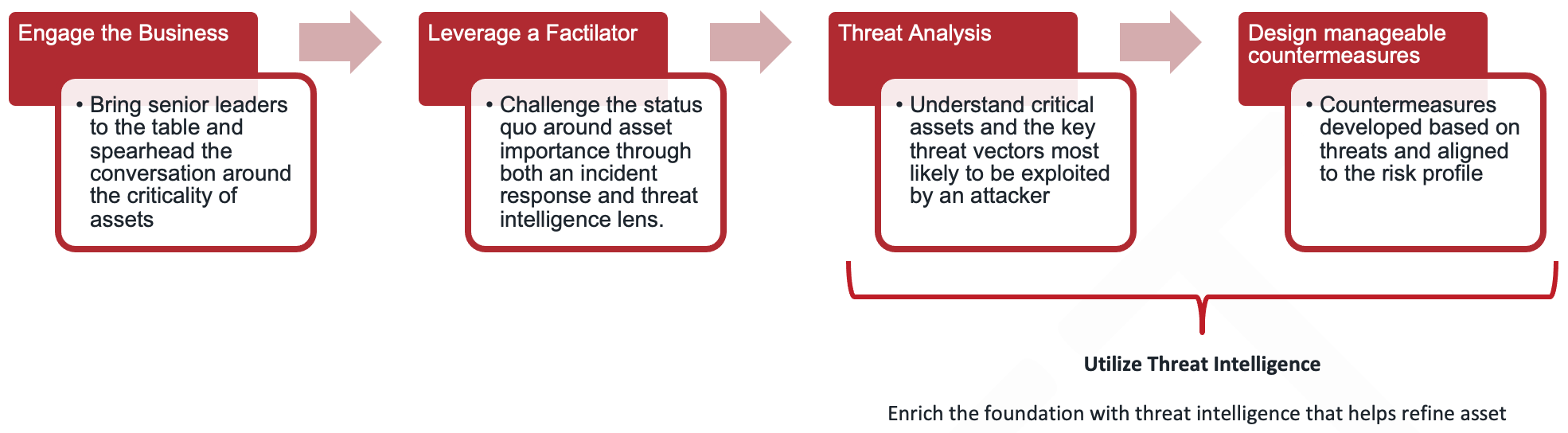
Here are some things to think about when developing a Crown Jewels approach:
- Make sure the Crown Jewels model isn’t just a repurposed business continuity plan.
- Combine standard risk management drivers such as importance, likelihood, and impact with intelligence-led concepts such as threat actors and motivations.
- High application usage doesn’t necessarily mean high value to an attacker
- Ensure generalized threats (such as phishing and commodity malware) don’t dominate models
- Avoid processes or teams being considered Crown Jewels (such as account payable and VIPs)
- Check if the proposed Crown Jewels portfolio assets are only focused on high monetary cost
- Don’t be afraid to override your model! If something “feels” more important, don’t be scared to make it more important.
Apply Threat Intelligence
While threat feeds will help with known attackers and their infrastructure, applying threat intelligence means having a full understanding of the threat actors that target your particular industry and assets. Understanding attacker motivations and behaviors—and building a threat profile based on their tactics, techniques and procedures (TTPs)—is necessary to begin effectively profiling an organization’s critical assets.
Infusing threat intelligence into a Crown Jewels approach means looking a little deeper, requiring organizations to consider the value of assets to them versus the value to an attacker. Risk management, business continuity, and/or disaster recovery plans don’t account for why an attacker targets an organization. Taking a Crown Jewels approach enriched with threat intelligence enables leaders to include critical assets in risk planning, as well as develop response protocols that are more aligned and better focused on what matters most.
Conclusion
Not all organizations are cut from the same cloth and security programs need to be right-sized for their respective business operational model and risk profile. Mandiant has worked with numerous organizations utilizing our measured approach to define acceptable loss, residual risk, and surface how teams can effectively mitigate impacts to their organization’s brand through the appropriate countermeasures and controls. The outcomes from this type of diligence can be a powerful differentiator within a security program and can be the difference between a minor incident at one organization and an impactful breach at another.
The ability to distinguish where control investments need to be made versus relying solely on a compliance or framework-based approaches helps to overcome the challenge of generic controls being applied indiscriminately across an organization, which can lead to overengineered programs that are difficult to maintain and sustain. This balanced approach is what makes a Crown Jewels approach to security so valuable for businesses of all shapes and sizes.
