How the Rise of Cryptocurrencies Is Shaping the Cyber Crime Landscape: Blockchain Infrastructure Use
UPDATE (May 31, 2018): A section of the post on commonly used OpenNIC IPs has been removed to avoid any implication that the OpenNIC IPs are inherently malicious, which is not the case.
Introduction
Cyber criminals have always been attracted to cryptocurrencies because it provides a certain level of anonymity and can be easily monetized. This interest has increased in recent years, stemming far beyond the desire to simply use cryptocurrencies as a payment method for illicit tools and services. Many actors have also attempted to capitalize on the growing popularity and subsequent rising price of cryptocurrencies by conducting various operations aimed at them, such as malicious cryptocurrency mining, collection of cryptocurrency wallet credentials, extortion activity, and the targeting of cryptocurrency exchanges.
Coinciding with the rising interest in stealing cryptocurrencies, distributed ledger technology (DLT), the technology that underpins cryptocurrencies, has also provided cyber criminals with a unique means of hosting their malicious content. This blog covers the growing trend of cyber criminals using blockchain domains for malicious infrastructure.
Blockchain Infrastructure Use
Traditionally, cyber criminals have used various methods to obfuscate malicious infrastructure that they use to host additional payloads, store stolen data, and/or function as command and control (C2) servers. Traditional methods include using bulletproof hosting, fast-flux, Tor infrastructure, and/or domain generation algorithms (DGAs) to help obfuscate the malicious infrastructure. While we expect cyber criminals to continue to use these techniques for the foreseeable future, another trend is emerging: the use of blockchain infrastructure.
Underground Interest in Blockchain Infrastructure
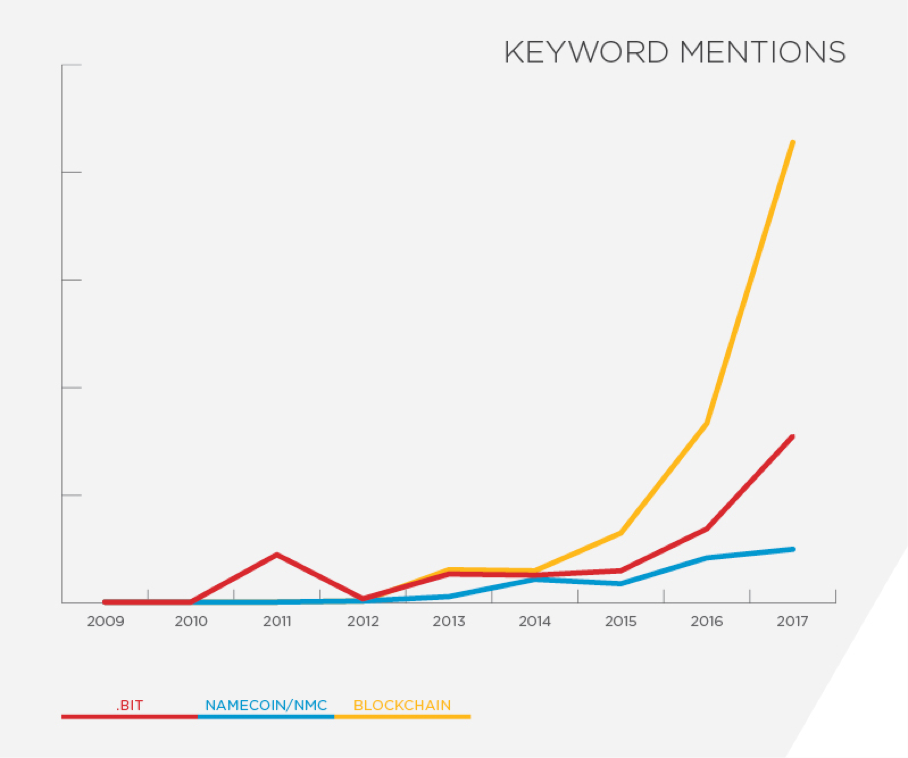
FireEye iSIGHT Intelligence has identified eCrime actor interest in cryptocurrency infrastructure-related topics dating back to at least 2009 within underground communities. While searches for certain keywords fail to provide context, the frequency of specific words, such as blockchain, Namecoin, and .bit, show a sharp increase in conversations surrounding these topics beginning in 2015 (Figure 1).
Namecoin Domains
Namecoin is a cryptocurrency based on the Bitcoin code that is used to register and manage domain names with the top-level domain (TLD) .bit. Everyone who registers a Namecoin domain is essentially their own domain registrar; however, domain registration is not associated with an individual's name or address. Rather, domain ownership is based on the unique encrypted hash of each user. This essentially creates the same anonymous system as Bitcoin for internet infrastructure, in which users are only known through their cryptographic identity. Figure 2 illustrates the Namecoin domain name generation process.
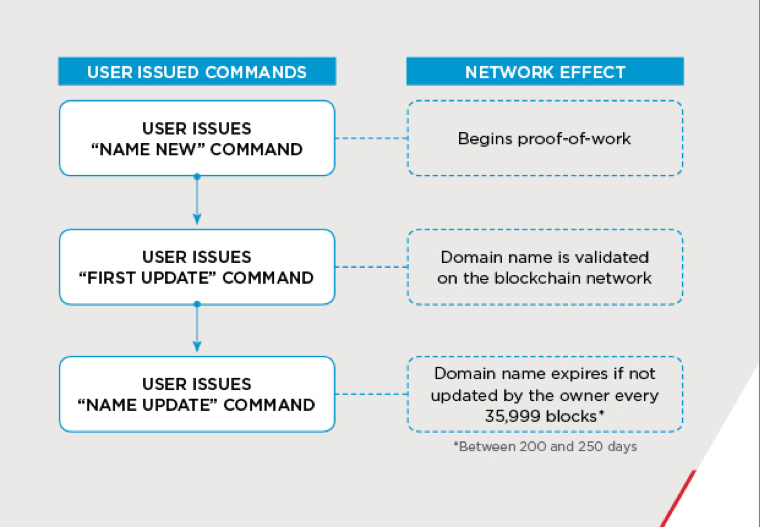
As Namecoin is decentralized, with no central authority managing the network, domains registered with Namecoin are resistant to being hijacked or shut down. These factors, coupled with the comparative anonymity, make Namecoin an increasingly attractive option for cyber criminals in need of supporting infrastructure for their malicious operations.
Navigating to Namecoin Domains
Domains registered with Namecoin use the TLD .bit, and are not managed by standard DNS providers. Consequently, a client will be unable to establish a connection to these blockchain domains unless additional configurations are made. According to the Namecoin wiki, individuals can take one of the steps shown in Figure 3 to browse .bit domains.
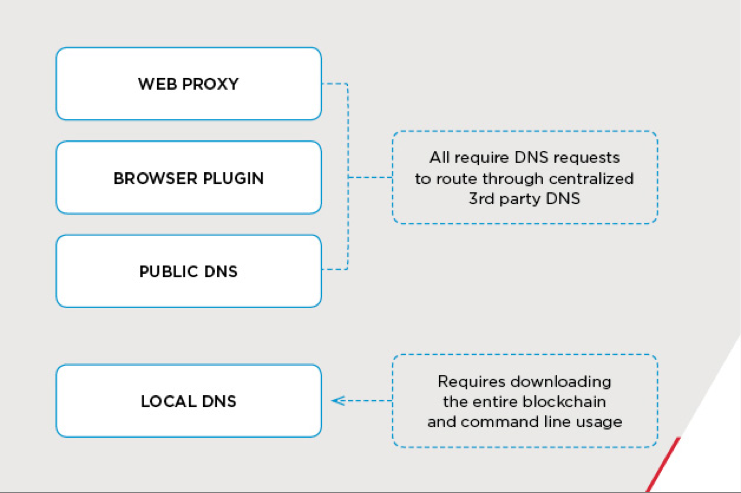
These options are not ideal for cyber criminals, as downloading the entire blockchain onto an infected host would require significant space and bandwidth, and routing their malicious traffic through an unknown third party could result in their traffic being blocked by the resolver. As a result, many have configured their malware to query their own privately managed Namecoin-compatible OpenNIC DNS (Figure 4), or to query other compatible servers they've purchased through underground infrastructure offerings. Bulletproof hosting providers, such as Group 4, have capitalized on the increased demand for .bit domains by adding support to allow malicious actors to query compatible servers.
Underground Advertisements for Namecoin Support
The following underground advertisements relating to the use of .bit domains have been observed by researchers over the past several years. These posts range from actors offering .bit compatible modules or configuration updates for popular banking Trojans to .bit infrastructure offerings.
Sample Advertisement #1
Figure 5 shows an advertisement, observed in late 2015, posted by the actor "wachdog" in a popular Russian-speaking marketplace. The actor advertised a small utility (10 KB in size) that is compatible with both Windows and Android operating systems, and would allow for the communication to and from .bit domains.
Advertisement Translated Text: The code is written in C+ for WinAPI or Java for Android. It can be used for small stealth applications to access .bit domains. The registration of new domain costs 0.02 NMC, update of a record - 0.005 NMC. So, the price for domain registration and update will be approximately 0.0072$ and 0.0018$. The code works in all Windows starting from XP, it doesn't require additional libraries, admin privileges, it doesn't download a lot of data. The size of compiled code is 10 KB. It's easy to write it in asm, paskal, c#, java etc. It also works for Android (all versions). You should download the Namecoin wallet, credit it with the minimum amount of NMC and register your own domain using the wallet. IP of C&C can be linked to the domain also using the wallet (one of many, everything works as for normal DNS). Create a build of your software locked to .bit domain. In case the IP of your server is listed, just change the DNS record and assign your domain a new IP for just for 0.005 NMC. No need in new rebuild or registration of new domains. .bit domain cannot be taken, botnet cannot be stolen. Price: Technology + code in C: $300 USD Technology + code in C + code in Java for Android: $400 USD |
Figure 5: Actor "wachdog" advertises utility to connect to .bit domains in late 2015
Sample Advertisement #2
In late 2017, actor "Discomrade" advertised a new HTTP distributed denial of service (DDoS) malware named "Coala" on a prominent Russian-language underground forum (Figure 6). According to the advertisement, Coala focuses on L7 (HTTP) attacks and can overcome Cloudflare, OVH, and BlazingFast DDoS protections. The original posting stated that the actor was working on adding support for .bit domains, and later updated the forum post to specify that Coala was able to support .bit domain communications.
Advertisement Translated Text: Coala - Http DDoS Bot, .net 2.0, bypass cloudflare/ovh/blazi... I changed my decision to rewrite the bot from the scratch on native language. I added the following features/options/abilities: - to customize the HTTP-headers (user-agent, cookie, referrer) I removed the feature related to DDoS attacks against TOR sites because of its improper functioning and AV detects. Currently I am working on .bit domains support. The price: $400 |
Figure 6: Discomrade advertising Coala DDoS malware support for .bit domains
Sample Advertisement #3
The AZORult malware, which was discovered in mid-2016, is offered in underground marketplaces by the actor "CrydBrox." In early 2017, CrydBrox offered an updated variant of the AZORult malware that included .bit support (Figure 7).
Advertisement Translated Text: AZORult V2 [+] added .bit domains support There are 4 variants of the stealer: The prices: |
Figure 7: CrydBrox advertising AZORult support for .bit domains
Namecoin Usage Analysis
Coinciding with malicious actors' increasing interest in using .bit domains is a growing number of malware families that are being configured to use them. Malware families that we have observed using Namecoin domains as part of their C2 infrastructure include:
- Necurs
- AZORult
- Neutrino (aka Kasidet, MWZLesson)
- Corebot
- SNATCH
- Coala DDoS
- CHESSYLITE
- Emotet
- Terdot
- Gandcrab Ransomware
- SmokeLoader (aka Dofoil)
Based on our analysis of samples configured to used .bit, the following methods are commonly used by malware families to connect to these domains:
- Query hard-coded OpenNIC IP address(es)
- Query hard-coded DNS server(s)
AZORult
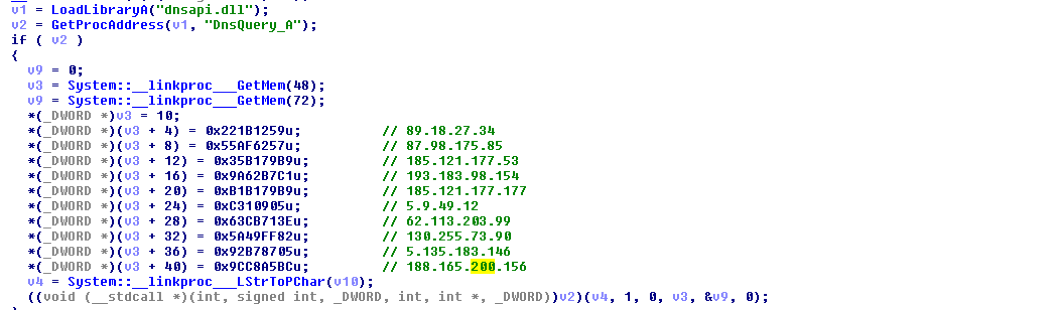
The AZORult sample (MD5: 3a3f739fceeedc38544f2c4b699674c5) was configured to support the use of .bit communications, although it did not connect to a Namecoin domain during analysis. The sample first checks if the command and control (C2) domain contains the string ".bit" and, if so, the malware will query the following hard-coded OpenNIC IP addresses to try to resolve the domain (Figure 8 and Figure 9):
- 89.18.27.34
- 87.98.175.85
- 185.121.177.53
- 193.183.98.154
- 185.121.177.177
- 5.9.49.12
- 62.113.203.99
- 130.255.73.90
- 5.135.183.146
- 188.165.200.156
CHESSYLITE
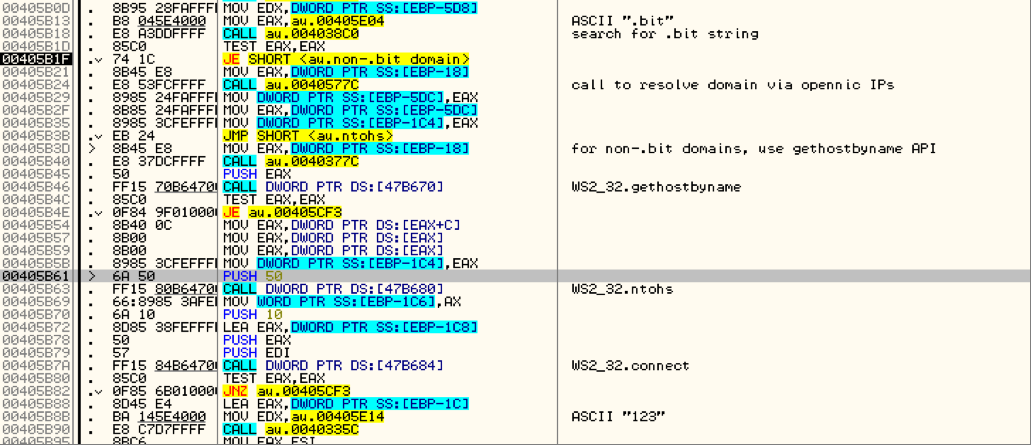
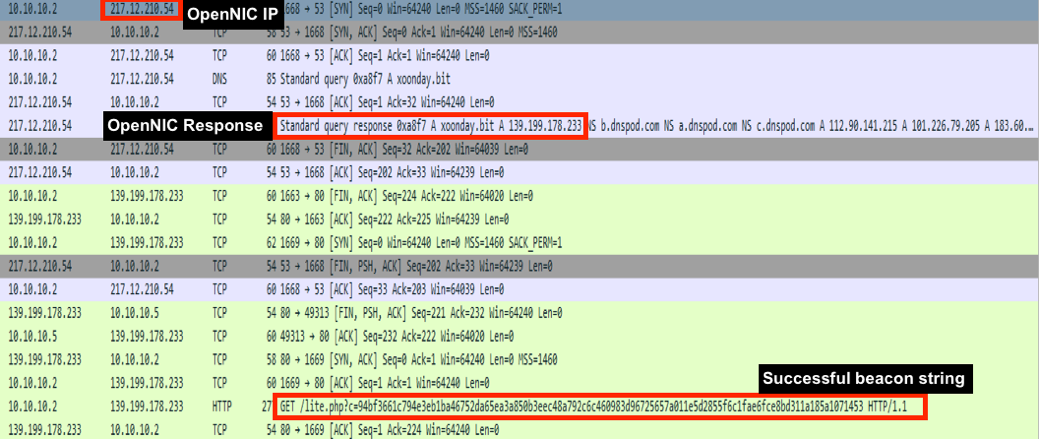
The analyzed CHESSYLITE sample (MD5: ECEA3030CCE05B23301B3F2DE2680ABD) contains the following hard-coded .bit domains:
- Leomoon[.]bit
- lookstat[.]bit
- sysmonitor[.]bit
- volstat[.]bit
- xoonday[.]bit
The malware attempts to resolve those domains by querying the following list of hard-coded OpenNIC IP addresses:
- 69.164.196.21
- 107.150.40.234
- 89.18.27.34
- 193.183.98.154
- 185.97.7.7
- 162.211.64.20
- 217.12.210.54
- 51.255.167.0
- 91.121.155.13
- 87.98.175.85
Once the .bit domain has been resolved, the malware will issue an encoded beacon to the server (Figure 10).
Neutrino (aka Kasidet, MWZLesson)
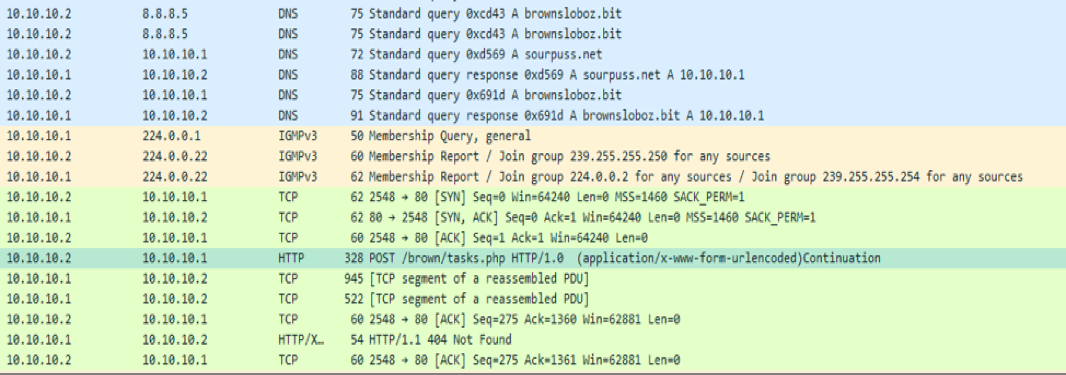
The analyzed Neutrino sample (MD5: C102389F7A4121B09C9ACDB0155B8F70) contains the following hard-coded Namecoin C2 domain:
- brownsloboz[.]bit
Instead of using hard-coded OpenNIC IP addresses to resolve its C2 domain, the sample issues DnsQuery_A API calls to the following DNS servers:
- 8.8.8.8
- sourpuss.[]net
- ns1.opennameserver[.]org
- freya.stelas[.]de
- ns.dotbit[.]me
- ns1.moderntld[.]com
- ns1.rodgerbruce[.]com
- ns14.ns.ph2network[.]org
- newton.bambusoft[.]mx
- secondary.server.edv-froehlich[.]de
- philipostendorf[.]de
- a.dnspod[.]com
- b.dnspod[.]com
- c.dnspod[.]com
The malware is configured to run through the list in the aforementioned order. Hence, if a DnsQuery_A call to 8.8.8.8 fails, the malware will try sourpuss[.]net, and so on (Figure 11). Through network emulation techniques, we simulated a resolved connection in order to observe the sample's behavior with the .bit domain.
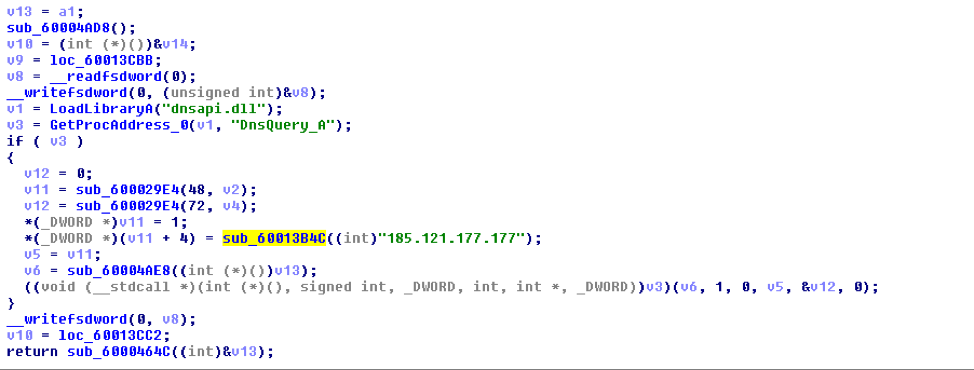
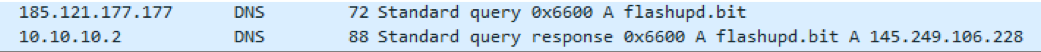
Monero Miner
The analyzed Monero cryptocurrency miner (MD5: FA1937B188CBB7fD371984010564DB6E) revealed the use of .bit for initial beacon communications. This miner uses the DnsQuery_A API call and connects to the OpenNIC IP address 185.121.177.177 to resolve the domain flashupd[.]bit (Figure 12 and Figure 13).
Terdot (aka ZLoader, DELoader)
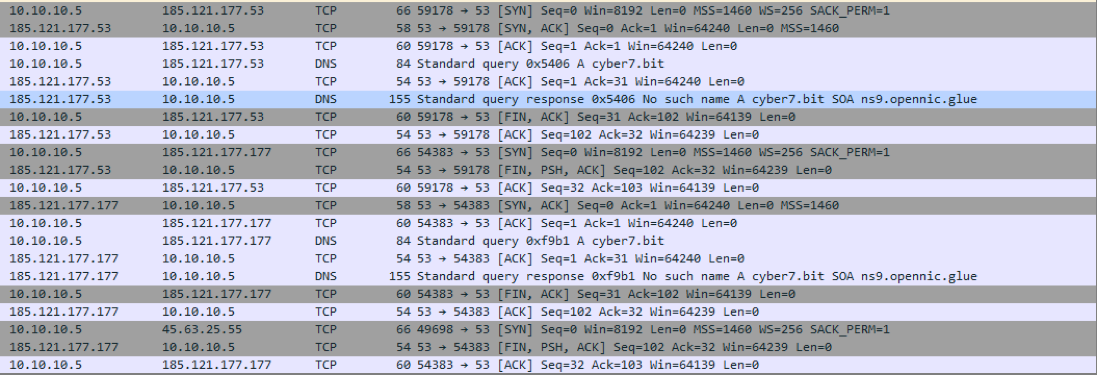
The analyzed Terdot sample (MD5: 347c574f7d07998e321f3d35a533bd99) includes the ability to communicate with .bit domains, seemingly to download additional payloads. It attempts resolution by querying the following list of OpenNIC and public DNS IP addresses:
- 185.121.177.53
- 185.121.177.177
- 45.63.25.55
- 111.67.16.202
- 142.4.204.111
- 142.4.205.47
- 31.3.135.232
- 62.113.203.55
- 37.228.151.133
- 144.76.133.38
This sample iterates through the hard-coded IPs in attempts to access the domain cyber7[.]bit (Figure 14). If the domain resolves, it will connect to https://cyber7[.]bit/blog/ajax.php to download data that is RC4 encrypted and expected to contain a PE file.
Gandcrab Ransomware
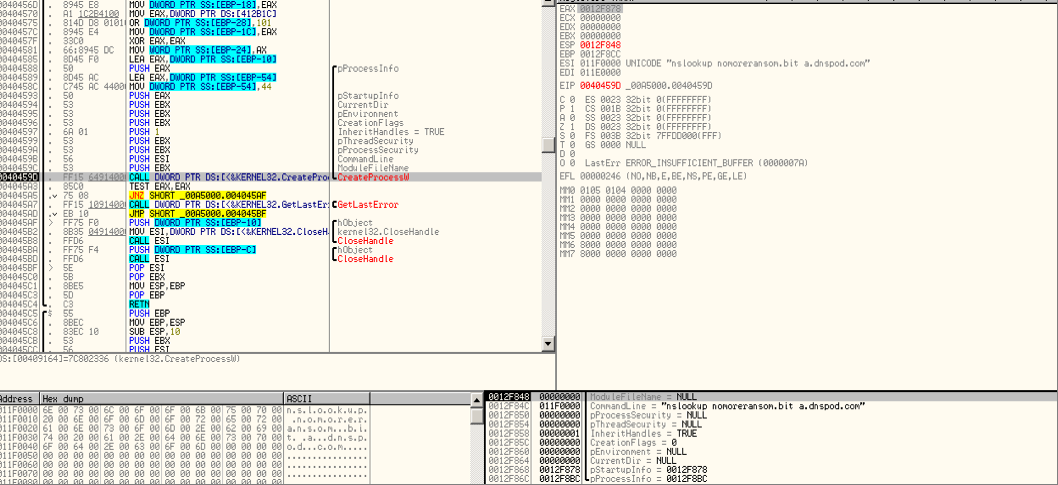
The analyzed Gandcrab ransomware sample (MD5: 9abe40bc867d1094c7c0551ab0a28210) also revealed the use of .bit domains. Unlike previously mentioned families, it spawns a new nslookup process via an anonymous pipe to resolve the following blockchain domains:
- Bleepingcomputer[.]bit
- Nomoreransom[.]bit
- esetnod32[.]bit
- emsisoft[.]bit
- gandcrab[.]bit
The spawned nslookup process contains the following command (as seen in Figure 15):
- nslookup <domain> a.dnspod.com
Emercoin Domains
FireEye iSIGHT Intelligence researchers have identified other blockchain domains being used by cyber criminals, including Emercoin domains .bazar and .coin. Similar to the Namecoin TLD, all records are completely decentralized, un-censorable, and cannot be altered, revoked, or suspended.
Navigating to Emercoin Domains
Emercoin also maintains a peering agreement with OpenNIC, meaning domains registered with the Emercoin's EMCDNS service are accessible to all users of OpenNIC DNS servers. Current root zones supported by EMCDNS are shown in Table 3.
| Zone | Intended Purpose |
| .coin | digital currency and commerce websites |
| .emc | websites associated with the Emercoin project |
| .lib | from the words Library and Liberty - that is, knowledge and freedom |
| .bazar | marketplace |
Table 3: Emercoin-supported DNS zones (Emercoin Wiki)
Users also have the option of installing compatible browser plugins that will navigate to Emercoin domains, or routing their traffic through emergate[.]net, which is a gateway maintained by the Emercoin developers.
Emercoin Domain Usage
FireEye iSIGHT Intelligence has observed eCrime actors using Emercoin domains for malicious infrastructure, albeit to a lesser extent. Examples of these operations include:
- Operators of Joker's Stash, a prolific and well-known card data shop, frequently change the site's URL. Recently, they opted for using a blockchain domain (jstash[.]bazar) instead of Tor, ostensibly for greater operational security.
- Similarly, the following card shops have also moved to .bazar domains:
- buybest[.]bazar
- FRESHSTUFF[.]bazar
- swipe[.]bazar
- goodshop[.]bazar
- easydeals[.]bazar
- In addition to the hard-coded Namecoin domain, the aforementioned Neutrino sample also contained several hard-coded Emercoin domains:
- http://brownsloboz[.]bazar
- http://brownsloboz[.]lib
- http://brownsloboz[.]emc
- FireEye iSIGHT Intelligence identified a Gandcrab ransomware sample (MD5: a0259e95e9b3fd7f787134ab2f31ad3c) that leveraged the Emercoin TLD .coin for its C2 communications (Figure 16 and Figure 17).
![DNS query for nomoreransom[.]coin](/sites/default/files/inline-images/dnsqueryfornomoreransom1.png)
![Gandcrab POST request to nomoreransom[.]coin](/sites/default/files/inline-images/gandcrabpost1.png)
Outlook
While traditional methods of infrastructure obfuscation such as Tor, bulletproof, and fast-flux hosting will most likely continue for the foreseeable future, we assess that the usage of blockchain domains for malicious infrastructure will continue to gain popularity and usage among cyber criminals worldwide. Coinciding with the expected increase in demand, there will likely be an increasing number of malicious infrastructure offerings within the underground communities that support blockchain domains.
Due to the decentralized and replicated nature of a blockchain, law enforcement takedowns of a malicious domain would likely require that the entire blockchain be shut down – something that is unfeasible to do as many legitimate services run on these blockchains. If law enforcement agencies can identify the individual(s) managing specific malicious blockchain domains, the potential for these takedowns could occur; however, the likelihood for this to happen is heavily reliant on the operational security level maintained by the eCrime actors. Further, as cyber criminals continue to develop methods of infrastructure obfuscation and protection, blockchain domain takedowns will continue to prove difficult.
