The Value of Early Knowledge — Mandiant Breach Analytics for Chronicle
In 2021, the global median dwell time—the number of days an attacker is on a victim system before being detected—was 21 days. While security teams have come a long way in reducing dwell time, there are still opportunities for improvement.
One key aspect of any effective security operations program is actionable, current, and relevant threat intelligence. Threat intelligence can help organizations stay ahead of threats and ultimately decreases dwell time; however, it can be challenging to properly implement due to the sheer breadth of adversary tactics, an ever-expanding attack surface, and a growing cyber security talent shortage.
That’s where Mandiant Breach Analytics for Google Cloud’s Chronicle comes in. Breach Analytics enables Chronicle customers to reduce attacker dwell time with advanced automation.
The offer is designed to inform customers about the presence of indicators of compromise (IOC). These IOCs are identified by Mandiant consultants investigating the latest breaches around the globe. Automation and machine-learning based models curate and prioritize IOCs at a fraction of the effort and cost. At the end of the day, the offering helps organizations answer the critical question: Are We Compromised?
Breach Analytics is Powered by Mandiant
To help organizations—regardless of size, industry, geography, or security controls deployed in the cloud, on-premises or in a hybrid model—detect a potential breach faster, we developed a proactive pipeline to Mandiant’s frontline insight and expertise as a virtual extension of a security team, all without requiring extensive security engineering. Now, using advanced analytics, security teams can know what we know—when we know it.
Mandiant’s services global footprint and large team of in-house security analysts and researchers make all the difference. Powered by the Mandiant’s Intel Grid™, Breach Analytics takes the latest IOCs from Mandiant Incident Response engagements, insight from our industry-leading threat intelligence analysts, and what we are seeing on the frontlines with Managed Defense clients, and continuously compares it to your cyber security data.
Breach Analytics not only matches known public tactics and techniques from threat actors against specific profiles, but also tactics that may be unpublished yet identified and qualified in Mandiant’s active Incident Response engagements, where Mandiant is ranked a leader in the recent Forrester Wave™. This ensures customers will always have the most current information from real, active breach investigations performed worldwide.
But it does not stop there. As threat actors and adversaries evolve with their attacks and techniques, systems that were once considered “safe” can be presented with new threats. Breach Analytics continuously analyzes historical data, enabling security teams to uncover past compromises, or past data that has become compromised, using newer IOCs. With Google Cloud Chronicle’s 12-month retention for all ingest, including high-volume data sources, users are now able to run retroactive hunts to identify the first point of breach in a cost-effective way.
The Inner Workings
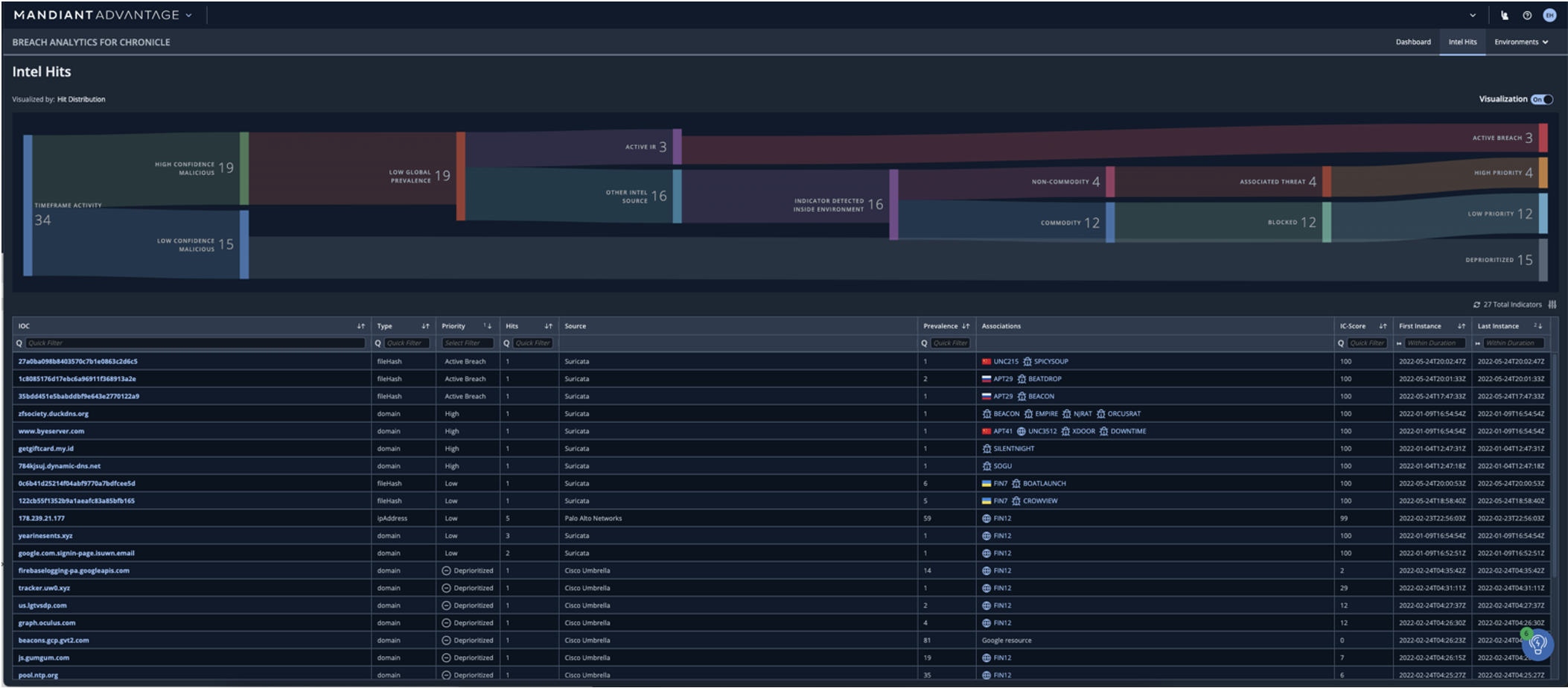
In Figure 1 we see how Breach Analytics found 34 matches or “hits” and quickly distilled it to only three of them being an “active breach”. In the absence of Breach Analytics, it would have taken the analyst more than 11 hours to triage and analyze (assuming roughly 20 minutes per “hit”).
With Breach Analytics, a security analyst can pick a “high priority” event to focus on and check its “IC-Score,” Mandiant’s expert-based confidence score for millions of officially known indicators, plus the latest unpublished insights for vulnerabilities. The “prevalence” indicator helps with understanding the immediate impact on similar geography or industry customers that Mandiant has already identified. Lastly, visibility into vulnerabilities identified in current Mandiant investigations within Active Breaches is essential for quickly understanding the risk at hand.
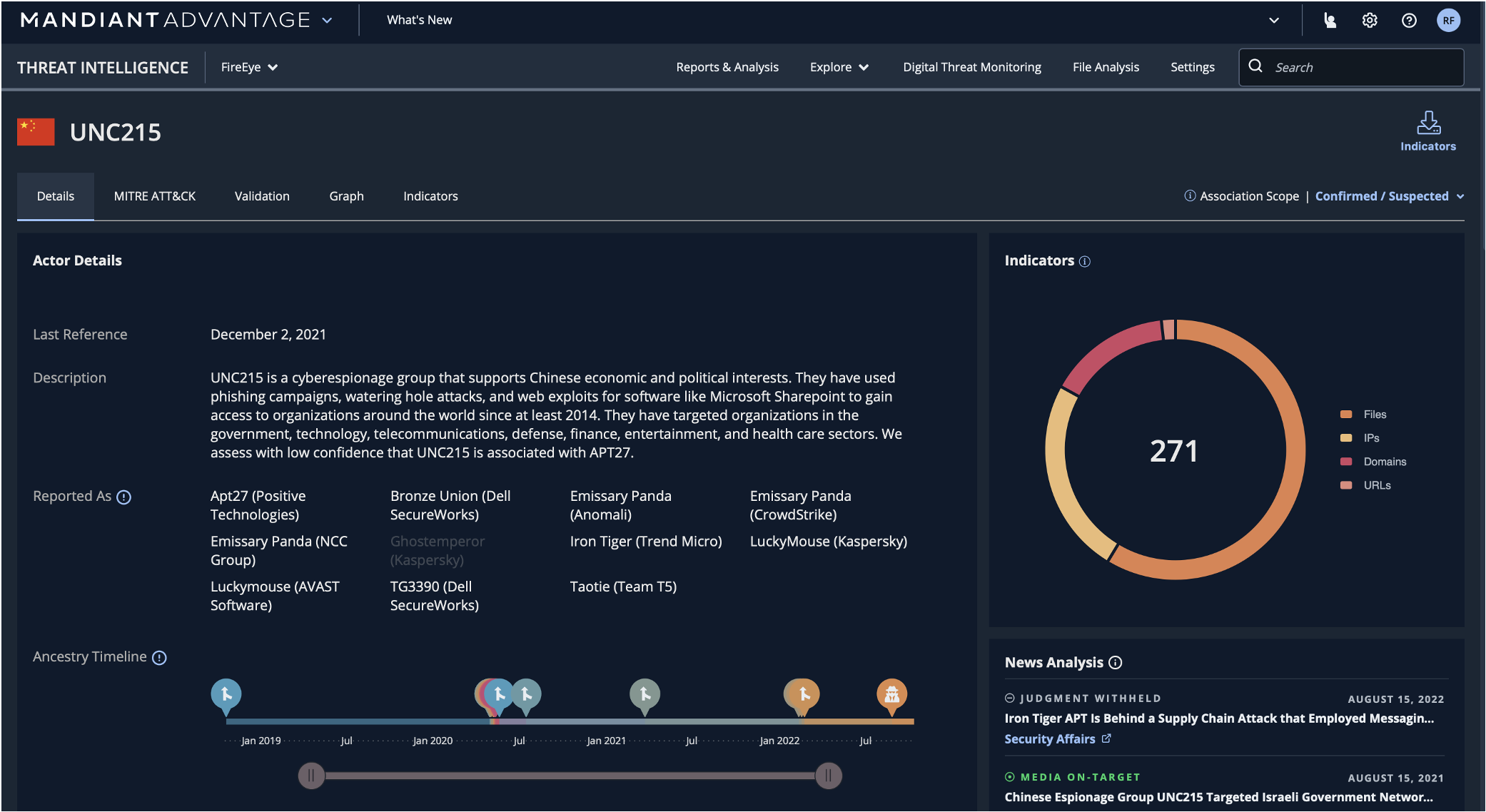
For deeper insights about the specifics of a compromise and the attack source, Mandiant Advantage Threat Intelligence is a click away. Figure 2 shows an example of an analyst zooming in on known threats such as “UNC215”, which is sourced in China with an “espionage” motivation and targets specific industries in specific regions—all indicated in this view.
How to Get Started
Mandiant Breach Analytics for Google Cloud’s Chronicle helps security professionals to find, understand, unify, and simplify threat actor activity within their systems. It identifies and matches IOCs, and then applies sophisticated data science and contextual data to determine relevancy and priority. It collects security events from multiple IT systems and translates it into useful and actionable information, all while saving time, effort and costs. Breach Analytics helps organizations decide about conducting deeper investigations with the goal of making a defend/no-defend decision to mitigate the risk of an impact on a business operations or reputation caused by an active breach.
To know what we know when we know it, request a Breach Analytics free demo today. Once implemented, Mandiant Breach Analytics for Google Cloud’s Chronicle is available for organizations using Chronicle Security Operations. Breach Analytics requires no server installation and is simple to implement. It collects log events from systems you are currently using and does not lead to changes in working environments or configurations.
In need of additional help investigating and scoping alerts at scale? Alert Investigation and Prioritization, data science models enable deeper investigations, decrease false positives, and reduce analyst triage fatigue, so analysts can focus on the events that matter most and then make informative defend/no-defend decisions.
Most companies—regardless of size—will suffer a cyber-attack. Mandiant Breach Analytics for Google Cloud’s Chronicle empowers organizations to find signs of attacks as they occur and reduce dwell time, so they can minimize the impact of a breach with the advantage of early knowledge.
Learn more about Mandiant Breach Analytics for Google Cloud’s Chronicle, or even better, sign up for a Breach Analytics demo. To learn more about Chronicle Security Operations, visit chronicle.security.
