Six Functions to Activate to Improve Your Cyber Defenses
Conversations on cyber security are increasingly focused on Security Operations Center (SOC) tools and activities. While it is impossible to deny the importance of the SOC to an organization’s security strategy, the SOC is part of the much broader scope of Cyber Defense. When Cyber Defense—which encompasses the SOC—isn't properly prioritized, the effectiveness of people, processes and capabilities used to defend environments from the latest attacks is impacted.
Robust Cyber Defenses are needed to prevent compromise, reduce attack impact, and enable organizations to continue to operate in the face of threats. In a new book published by Mandiant, The Defender’s Advantage, our intelligence and consulting experts lay out six critical functions of Cyber Defense and how to activate them against threat actors launching attacks in our own environments.
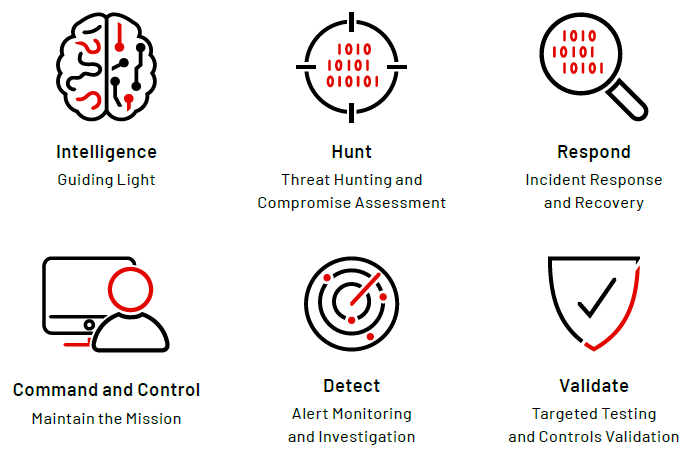
Each of these Cyber Defense functions focuses on a unique piece of the overall cyber security program, feeding into each other and benefiting from their joint capabilities.
1. Intelligence Function
Cyber threat intelligence guides all action within Cyber Defense. It is the lifeblood of Cyber Defense, delivering insight into attackers, their targets and motivations, helping to uncover vulnerabilities and the potential impact of an attack. When threat intelligence is fully activated within an organization’s security team, they have greater understanding of the threats facing them, are able to make more informed decisions, and can get a better sense of their organization’s risk exposure.
2. Hunt Function
Hunting is the practice of searching an environment for evidence of current or past compromise. In today’s changing landscape, hunting for active threats is a necessary and important part of Cyber Defense. When a hunting function is properly implemented, detecting ongoing attacks isn’t the only benefit. Hunting can also help organizations shore up defenses by uncovering previously unknown vulnerabilities or security gaps.
3. Detect Function
Detecting and investigating malicious activity are understood as the more traditional activities performed by SOC teams. Unfortunately, optimizing SOC activity is an ongoing struggle for many organizations faced with overwhelming alert volumes. An optimized SOC team leverages threat intelligence to manage, evaluate and prioritize detection use cases. This allows them to prioritize and investigate anomalous behavior identified by the technical security controls in their environment. The pressures faced by SOC teams today can be eased by deploying technology to automate tasks, modernizing SOC procedures and augmenting the team with highly skilled analysts.
4. Respond Function
The Respond function is responsible for confirming whether suspicious activity constitutes a breach, and if it does, for containing the incident, restoring business operations and eradicating all trace of an attacker from the environment. When intelligence is activated in the incident response process it can shorten incident response times and prevent repeat compromise. Outcomes from the Respond function also extend to identifying any lessons learned from an incident to improve intelligence and operations for the future, as well as other processes.
5. Validate Function
Targeted testing and continuous controls validation are another important function of Cyber Defense. These activities objectively evaluate the systems and tools in place to reduce an organization’s risk exposure. Through the safe deployment of real attacks across the kill chain, organizations can discover undetected gaps, overlaps in security infrastructure and opportunities for optimization. Validation of people, process and tools throughout Cyber Defense is also an important part of building confidence that the organization can effectively respond to a breach.
6. Command and Control Function
Central to Cyber Defense is the Command and Control function that ensures the Intelligence, Hunt, Detect, Respond and Validate functions are aligned to the organization’s overall security mission. The focus is primarily on people and processes within the Cyber Defense domain, providing direction and resource prioritization across all functions to protect critical assets from a breach. The Command and Control is generally made up of team members from the other functions and is activated during a breach to orchestrate Cyber Defenses, including crisis communications and alignment with other business imperatives.
Gaining The Defender’s Advantage
To see the bigger picture that Cyber Defense plays in preventing and reducing the impact of an attack and improving the identification and containment of a compromise, organizations must look beyond the SOC. Without a fully operationalized Cyber Defense, organizations can suffer from siloed or uncoordinated security activities, leading to duplicated efforts, a lack of information sharing, inefficient/ineffective operations, and a failure to identify critical security gaps before a breach occurs.
By breaking Cyber Defense into six integrated functions, organizations can determine gaps in capabilities and invoke accelerators to achieve greater business protection. With this view, organizations can distinguish capabilities that are best served by internal resources, identify where external assistance is required, and invest in automation to alleviate time consuming manual tasks.
The Defender’s Advantage by Mandiant lays out how organizations across all industries can achieve a fundamental advantage over their adversaries by activating and maturing their Cyber Defenses. Access your free copy today for our step-by-step guide to building robust Cyber Defenses in your organization.
Free Self-Assessment
Mandiant has developed a free self-assessment to help organizations of all sizes assess their cyber defense capabilities, and identify areas where they can improve their security. The self-assessment is based on the six critical functions of cyber defense laid out in The Defender’s Advantage.
