
Red Team Assessment
Test your security against real-world attacks without the risks of negative headlines

Put your cyber security program to the test
Test your security program against real-world attacks
Experience attack objectives that expose your organization to worst-case business scenarios – both in the cloud and on-premise.
Gain experience combatting real-world cyber attacks
Emulate tactics, techniques, and procedures (TTPs) seen in actual incident response engagements.
Identify and mitigate complex security vulnerabilities
Receive a comprehensive report detailing all security vulnerabilities identified during the assessment, with remediation recommendations.
Mandiant Red Team Assessment Features

Real-world attack scenario
Methodology uses realistic attack scenarios using tactics, techniques, and procedures seen in real-world attacks.

Customizable objectives
Tailored engagements to meet organizational needs, with objectives based on the most relevant risks to your organization.
Sample objectives:
- Obtain access to PCI data
- Obtain access to personally identifiable information (PII)
- Obtain access to trade secrets

Industry expertise
Consultants experienced with critical infrastructure sectors – including energy, healthcare, and telecommunication providers.

Reports
Detailed, concise reports with actionable recommendations to aid in remediating identified issues post-engagement.
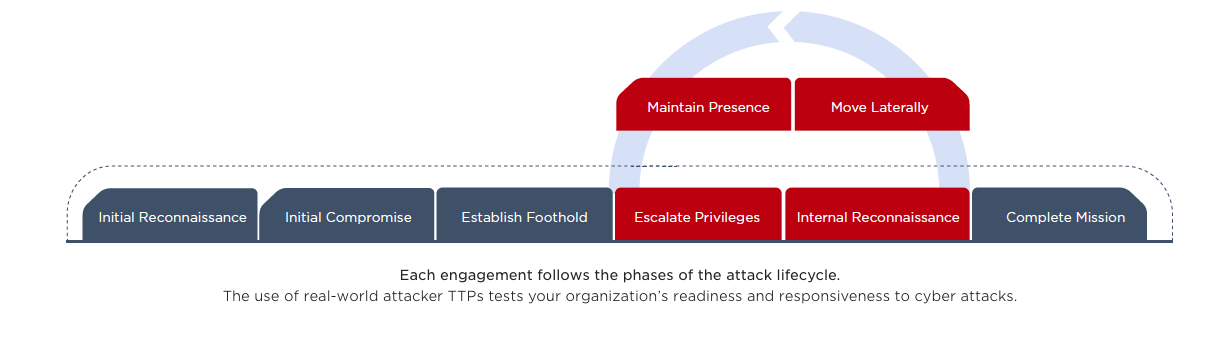
Our Methodology
The Mandiant Red Team relies on a systematic, repeatable and reproducible methodology. In collaboration with the organization’s leadership team, we begin by establishing the following core information and rules of engagement:
- Does the red team begin its effort with information about your environment (white box) or with no information at all (black box)?
- What intelligence does Mandiant already have about high-risk assets and vulnerabilities in your industry?
- What objectives do you want the red team to accomplish in simulating a real-world attack?
Once the objectives are set, the red team starts by conducting initial reconnaissance. Mandiant uses a combination of proprietary intelligence repositories, open-source intelligence (OSINT) tools and techniques to perform reconnaissance of the target environment.
Mandiant works to gain initial access to the target environment by exploiting vulnerabilities or conducting a social engineering attack, and leverages techniques used by real-world attackers to gain privileged access to these systems.
Once access is gained, the red team attempts to escalate privileges to establish and maintain persistence within the environment by deploying a command and control infrastructure, just like an attacker would.
After persistence and command and control systems are established within the environment, the red team attempts to accomplish its objectives through any non-disruptive means necessary.
Red Team Cyber Security Assessments at a Glance
We help you:
- Test your security team’s effectiveness in dealing with a cyber attack
- Train your team to better respond to future cyber attacks
- Determine the level of effort required to compromise your sensitive data or IT infrastructure
- Identify and mitigate complex security vulnerabilities before an attacker exploits them
- Receive fact-based risk analysis and recommendations for improvement
What you get:
- A high-level executive summary of the Red Team Assessment, catering towards executives and senior-level management
- A detailed report describing actions taken during the assessment and a report of all found vulnerabilities
- Fact-based risk analysis detailing the relevance of each vulnerability with respect to your environment, and techniques to validate said vulnerabilities
- Strategic recommendations for long-term improvement
Cyber Attack Simulation FAQ
Reliable and expert red teams deploy attack objectives that expose an organization to worst-case cloud and on-premise business scenarios. This is accomplished by simulating modern tactics, techniques and procedures (TTPs) of real-world attackers that target high-risk cyber assets. This attacker knowledge is based on actual incident response engagements and up-to-date cyber threat intelligence.
The best way to improve a security team’s skills is to combine various exercises, such as continuous purple teaming, experiential learning in a consequence-free cyber range, and specialized cyber security training .
Ready to Get Started?
Our security experts are standing by to help you with an incident or answer questions about our consulting and managed detection and response services.