
What is managed detection and response (MDR)?
MDR is a managed security service that monitors your security technology 24/7 and applies human intelligence and interpretation to quickly find and investigate impactful events, proactively hunt for ongoing or past breaches, and respond before attacks impact your business.
Managed XDR is widely considered an evolution of MDR services. Both offer a turnkey experience to help organizations perform the functions of detect, respond and recover in the NIST Cybersecurity Framework.
Managed detection and response services fill a gap between detect and respond created by the sophistication of today’s attackers that require security practitioners to investigate and form an effective response.
For example, the security operations center (SOC) sees alerts for a process deleting shadow copy volumes on an endpoint machine. This is often executed by ransomware before encrypting files to impede recovery. However, what was detected was the action of deleting backup copies. It is ineffective to move immediately to respond and create new backups without understanding the full scope of the problem. Security teams must first investigate to understand if this was an automatic process or a bad actor. If it was bad actor, additional information needs to be analyzed, including what sort of access the attacker has on the network.
Investigation is not easy. It requires skilled people, processes and technology all working together.
Extended detection and response (XDR) is a capability that integrates, correlates and contextualizes data and alerts from an organization’s security products to deliver a more unified and efficient approach to prevent, detect and respond to threats.
Security teams are overloaded with a multitude of security controls that generate too much data, inhibiting their ability to secure their environments in a timely manner. The result: attackers go undetected for too long, free to inflict significant, lasting organizational impact.
- Analysts need automation to work smarter and faster
- Investigation of advanced attacks requires specialty skills that are hard to find and maintain
- Most organizations don’t have enough highly skilled people
Managed Defense: The Analytical Mindset
When it comes to detection and response, you are ultimately reliant on analyst expertise to find and stop attackers in your environment. Learn what kind of tools and investigative mindset are needed from this recent Mandiant Managed Defense investigation and response.
Security teams that use MDR services can expect a significant reduction in attacker dwell time that reduces the impact of a security breach.
- Augment your team with experienced analysts and incident responders without adding full-time staff
- Extend threat detection across your enterprise
- Improve your understanding of important and timely threats to your business
- Uncover attackers your technology missed with proactive threat hunting
Modern ransomware attacks are multifaceted with multiple outcomes. The combination of practiced SOC analysts and proactive threat hunting accelerates an organization’s ability to find and halt sophisticated threat actors before they deploy debilitating ransomware or extort the victim.
How to Stop a Ransomware Attack
If you want to stop a ransomware attack, speed matters. Defenders need to be well-informed, practiced and swift. See what can happen in the short time a bad actor dwells in your network before it deploys ransomware and achieves its goal.
Actions taken via managed detection and response
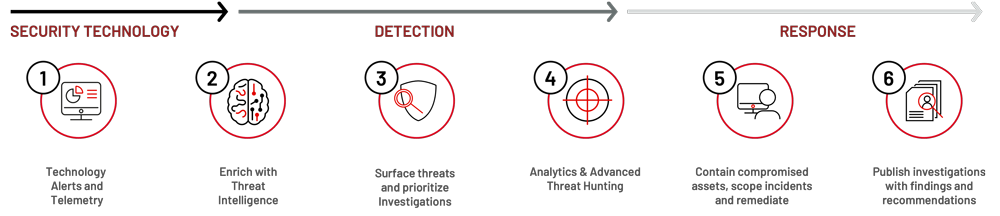
MDR providers rely on analyst knowledge combined with a systematic inquiry process, curated threat intelligence and experience responding to advanced attackers.
- MDR providers ingest logs and detection alerts from your security technologies (endpoint, network, cloud and operational technology).
- MDR providers overlay threat intelligence to provide context to technology alerts.
- MDR analysts assess alerts and threat hunting detections within the customer environment investigate and provide a narrow set of priorities enriched with context.
- Proactive threat hunting is a critical component of most MDR services, directed by threat intelligence and streamlined by data science and automation.
- MDR providers contain compromised assets, scope incidents and develop actionable response for the customer. Providers use endpoint technology to contain affected hosts and prevent further attack impacts.
- MDR providers deliver investigation findings and response and recovery recommendations to the customer in a full report.
Today’s increasingly sophisticated attackers continuously alter their techniques to evade detection from security technologies. Organizations need to proactively hunt for undetected attackers in their environments.
Expert hunters think differently—they systematically combine knowledge, intuition and automation to proactively search for covert signs of an active or attempted compromise. They use the experience they gain from continuous exposure to attacker behavior, tactics, techniques and targets. Proactive threat hunting is both:
Artifact-driven: When anomalous activity is discovered, threat hunters quickly form and test hypotheses around the attacker’s next moves to formulate a definitive response.
Mission-based: Agile, ongoing approach based on experience in the frontlines of incident response and threat intelligence. Missions test against known attacker behavior, tactics and targets as mapped to the MITRE ATT&CK framework.
In addition to expert threat hunters, proactive threat hunting requires:
- Operationalized threat intelligence from varied sources (adversary, victim, machine and campaign) Expert threat hunters use intelligence to streamline their activities and focus on the most relevant threats impacting the organization.
- Large amounts of security data from logs and forensic artifacts from endpoint, network, cloud and email.
- Data science and automation to elevate efficiencies and reduce costly system resources are needed to create complex rule sets within security information and event management (SIEM) tools to comb through large datasets.
Traditionally, MSSPs primarily help with detection, providing alert prioritization and reduction. They do not investigate or respond to incidents. Those functions are left to in-house customer security teams. MSSPs may provide other services such as device management, log retention or reporting functions.
MDR providers are specialists in detecting advanced threats and offer a variety of response services. Their deep expertise is not readily available in house or from an MSSP, and includes threat hunting, advanced malware analysis, forensics and security research.
Managed Security Service Provider Functions
| Functions | MSSP | MDR or MXDR |
|---|---|---|
| Device management | X | |
| Configuration management | X | |
| Vulnerability management | X | |
| Log retention and reporting | X | |
| 24/7 monitoring and alert triage | X | X |
| Detect known threats | X | X |
| Detect unknown threats | X | |
| Expert analysts investigate incidents | X | |
| Automated sweeps against known threats | X | X |
| Proactive threat hunting powered by automation | X | |
| Remote remediation, when available | X | |
| Expert incident responders perform rapid response | X | |
| Deep expertise for advanced malware analysis, forensics, and security research | X |
The Definitive Guide to MDR
Discover what you need to accelerate detection and response with the Mandiant Definitive Guide to MDR. Complete with descriptions of critical functions, this guide includes questions to ask vendors when you are looking for an MDR partner.
How is the Mandiant approach different from other MDR offerings?
The combined power of intelligence, expertise and automation in Mandiant Managed Defense delivers unique, differentiated and high-demand cyber security capabilities, knowledge and skills to SOC managers and their security teams. It minimizes many critical SOC challenges with:
- A dedicated onboarding team to ensure smooth implementation from day one
- A dedicated Managed Defense consultant who becomes part of the client’s security team and acts as their conduit and incident handler
- An early knowledge advantage through world-leading threat intelligence that delivers advanced detections and notifications of ongoing adversary activity from the latest frontline experiences
- The ability to integrate disparate data types with Mandiant technology and gain a cohesive, single vantage point to secure their environment
- A combination of skilled threat hunting and proprietary Mandiant intelligence to help discover and identify headline-worthy threats, adversaries and vulnerabilities.
The full benefits of Mandiant Managed Defense extend to the C-Suite. Executive leadership gains peace of mind, knowing that their SOC managers and security teams understand the threats that matter to their organization.
Have Questions? Contact Us.
Mandiant experts are ready to answer your questions.
