Transcending Silos: Improving Collaboration Between Threat Intelligence and Cyber Risk
Cyber Threat Intelligence (CTI) and risk management have emerged as distinct disciplines, yet they share many similarities in their mission. Both approaches inform decision-making by providing high-quality insight on the most relevant threats and risks impacting organizations. Although risk and CTI teams approach this challenge from different vantage points, their underlying shared mission creates exciting opportunities for collaboration. Collaboration also provides a no-cost opportunity to cross-train staff on complementary skills, augmenting existing capacity to address the biggest inhibitor organizations face when implementing CTI effectively, according to the SANS 2023 CTI Survey.
In our latest whitepaper, Better Together: The Benefits of Integrating Cyber Threat Intelligence and Risk Management, we outline practical steps on how CTI and risk professionals can work together. Improving collaboration begins with building mutual understanding. Once CTI professionals understand the core principles of cyber risk management (and vice versa), they are in a much stronger position to work together. Several factors can undermine CTI-risk cooperation, including the unique lexicons used in each discipline, misperceptions about the role each team serves, and cultural differences. To rectify this, our whitepaper provides a high-level overview of both approaches to identify common ground.
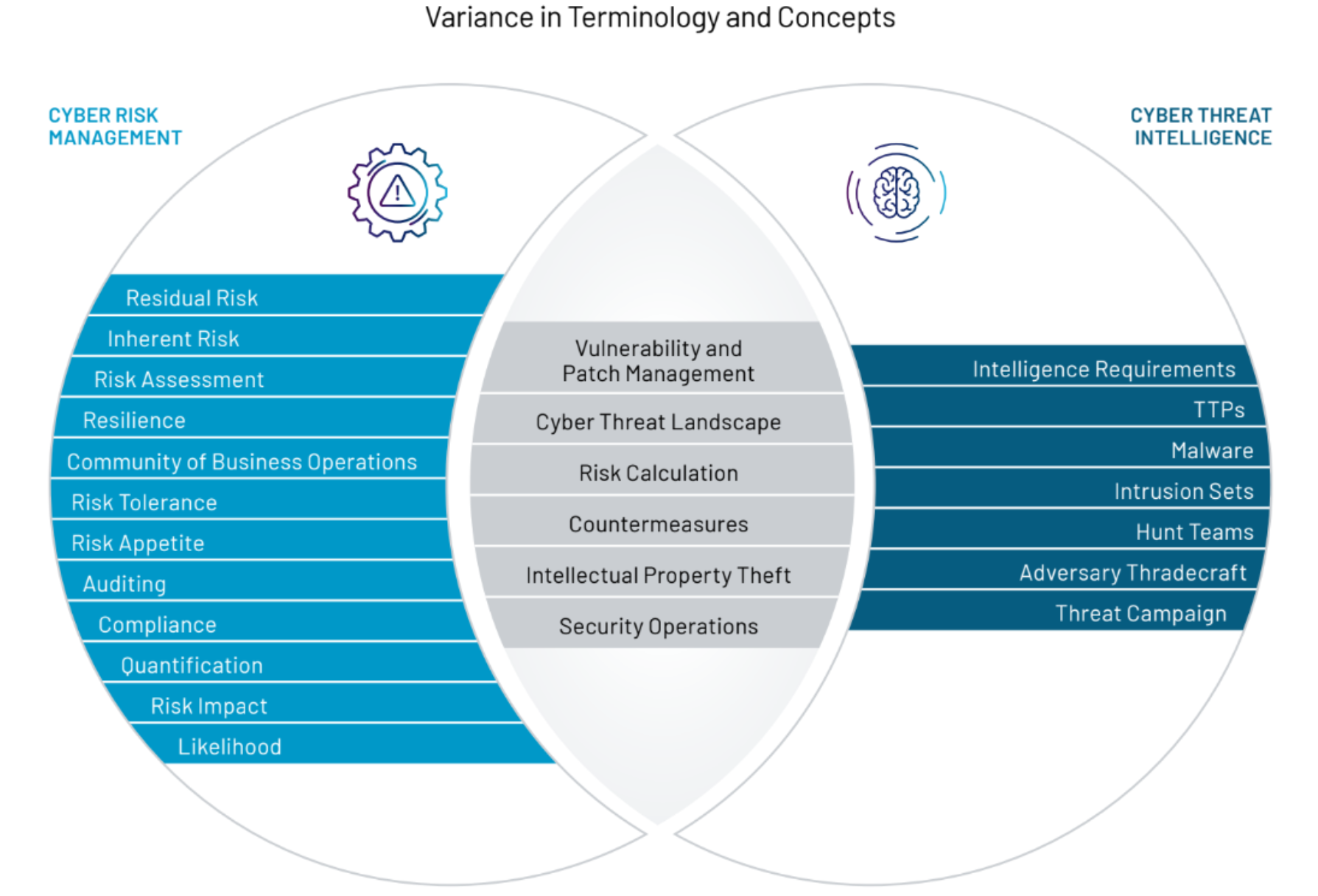
The paper then explores how foundational CTI concepts can be applied to risk management, including stakeholder analysis, intelligence requirements, and a cyber threat profile. A threat profile can be used to develop a threat model, which can be used by risk management teams to determine whether adequate security controls are in place to address potential risk exposure.
Partnership between risk and CTI teams can play out in various ways, and is highly dependent on an organization's unique context and favored risk framework. Rather than a set of rigid rules, our paper outlines a range of collaboration opportunities. These are best viewed as a menu of potential options that can be adapted accordingly. Typical examples of collaboration include: crown jewel asset mapping, threat modeling, and feeding threat data into risk matrices.
We also provide three case studies that provide examples of how both teams can collaborate to develop jointly-produced assessments for their leadership. These case studies are focused on patch prioritization informed by newly identified software vulnerabilities, software supply chain risk and threats targeting software developers, and transferring ransomware risk through cyber insurance purchases.
Additionally, we highlight the opportunity to codify partnership opportunities through the development of a combined intelligence-risk (RACI) matrix. An intelligence-risk RACI matrix clarifies the involvement and ownership of different risk-related issues within an organization. Given the vast potential overlap between the two functions, building a RACI matrix represents a positive opportunity to streamline and enhance the effectiveness around process integration by clarifying roles.
| Activity | Responsible | Accountable | Consulted | Informed |
| Identify and document cyber threat use cases | CTI | CTI | IT Leadership | Risk |
| Lead cyber risk assessments | Risk | Risk | CTI | IT Leadership |
| Develop threat models | IT Security | IT Security | Risk and CTI | IT Leadership |
| Validate cyber threats to crown jewel assets | CTI or red team | Risk | Risk | IT Leadership |
Cyber risk and CTI both confer clear benefits to organizations independently. Yet, their value multiplies exponentially when brought together. When cyber risk is deeply connected to developments in the threat landscape, decision makers are equipped with the best insight available to confront their most pressing and complex challenges.
Download Better Together: The Benefits of Integrating Cyber Threat Intelligence and Risk Management today. For, more check out our other CTI whitepaper, A Requirements-Driven Approach to Cyber Threat Intelligence.
