Unveiling Mandiant’s Cyber Threat Intelligence Program Maturity Assessment
As part of Google Cloud's continuing commitment to improving the overall state of cybersecurity for society, today Mandiant is publicly releasing a web-based Intelligence Capability Discovery (ICD) to help commercial and governmental organizations evaluate the maturity of their cyber threat intelligence (CTI) program. The ICD is designed to provide cyber security practitioners and threat intelligence leaders with an estimate of how effectively and efficiently the organization's CTI program is creating a positive organizational impact and reducing risk for the business. The ICD plays a critical role in helping organizations design, build, operate, and enhance their CTI program.
- The scoring measures used in the ICD are derived from the NIST Cybersecurity Framework, and represent what Mandiant has identified as foundational elements that contribute to effective CTI programs.
- Many thanks to all of our industry peers who provided feedback during the 2024 SANS CTI Summit workshop “How to Build an Effective Cyber Threat Intelligence Program” where we previewed the assessment. We are especially grateful to Grace Chi, Sierra Stanczyk, Rebecca Ford, Mike Debolt, Alena Funtikova-White, and Michael Thompson who kindly helped us test the ICD in advance of the workshop.
One Assessment to Rule Them All
By design, the ICD aims to validate a CTI program’s existing practices while identifying growth opportunities and providing organizations with insights critical for future planning. The ICD consists of 42 questions spread across six capability areas. The ICD measures people, processes, and technologies across a CTI program, as well as the program's strategic alignment, organizational reach, and engagement with broader information sharing communities. The six capability areas are:
- The Organizational Role of CTI
- Intelligence Services and CTI Use Cases
- Analyst Capability and Expertise
- Intelligence Process Lifecycle
- Analytic Practices and Products
- Technology Integration
Through a series of prompts, the assessment taker will self-rate their program one measure at a time. For each measure, the participant chooses the option that best reflects the current state of their CTI program. Upon completion, the ICD will provide a maturity score and practical recommendations for improvement including related intelligence courses to uplift analyst expertise. These recommendations also link to capability areas highlighted in previously published Mandiant whitepapers like the CTI Analyst Core Competencies Framework.
- The ICD uses an adaptation of the Capability Maturity Model Integration (CMMI) framework (CMMI) framework scoring categories. The CTI-centric assessment evaluates each capability area on a maturity range from Initial to Adaptive.
- The practical recommendations highlight overarching CTI program guidance, why the capability area is important, and some capability best practices. The recommendations also align with Mandiant service offerings which can help organizations of all sizes uplift and evolve their intelligence programs.
Diving Deep into the Capability Areas
Mandiant intelligence consultants have worked with private and public sector organizations for over a decade to assess, design, build, operate, and enhance CTI programs. Over this time period, we have observed common themes present during our engagements, which are consistent across industry, organizational size, or cybersecurity program constructs. The capability areas and their respective measures are a manifestation of our observations juxtaposed with the evolution of the CTI field and the expanding demands on CTI programs. The ICD measures are informed by Mandiant’s requirements-driven CTI program philosophy, which you can read about in our whitepaper.
Capability Area | Description |
Organizational Role of CTI | Establishes the CTI program as a defined function in the organization with authority to operate, a defined mission mandate, and funding that has been approved by leadership. |
Intelligence Services and CTI Use Cases | Outlines the type of service support the CTI program provides across strategic, operational, and tactical requirements and common stakeholders and their use cases. |
Analyst Capability and Expertise
| Ensures the CTI program is staffed with practitioners that have necessary breadth, depth, specialization, and commensurate business, security, and risk understanding to support current and future intelligence requirements. |
Intelligence Process Lifecycle | Focuses on process elements that drive CTI operations, improve efficiencies, organizational reach, and overall impact. |
Analytic Practices and Products | Captures how the CTI program operates in a consistent manner to ensure repeatable workflows, analytic rigor, standards, and quality across intelligence practices and products. |
Technology Integration | Integrates technical solutions to extract, collect, track, process, normalize, correlate, tag, store, analyze, and retrieve information. Communication platforms are also included for collaborating and sharing information. |
For each discovery measure, the assessment taker selects whether they believe their CTI program fully complies with all of the areas identified in the measure, partially complies, or does not comply. There is also a non-applicable option available if the measure truly is not relevant to their team’s specific services or mission. Some measures are more simplistic than others whereas the more complex measures will have multiple parts. If your program meets only some of the requirements outlined in a measure then score yourself "partial".
For illustrative purposes, consider the following six measures that an assessment taker would evaluate:
The Organizational Role of CTI
Complex measure: Is the CTI function a recognized, formalized part of the organization with an explicit call out on the organizational chart that operates in accordance with authorities granted in its program charter?
Simplistic measure: Is the CTI function able to surge capacity when needed to support imminent threats that could have significant negative impact to the organization?
Intelligence Services and CTI Use Cases
Complex measure: Does the CTI function provide tactical intelligence support that focuses on intrusion clustering, IOC documentation, or signature development to support security operations in a proactive manner and are used to align detection and response activities to the most relevant and impactful threats? Detections developed are tagged properly with a reference to related intelligence.
Simplistic measure: Does the CTI function provide strategic support to drive risk and threat exposure reduction? This includes stakeholders across risk management, cyber defense leadership, security awareness, and other organizational facets.
Analyst Capability and Expertise
Complex measure: Does the CTI workforce understand the organization's various business functions, critical services, technology dependencies, and have the proper organizational and environmental knowledge about processes, risk management criteria, and security controls to provide actionable recommendations for stakeholders?
Simplistic measure: Does the CTI function have defined roles and responsibilities for team members? Irrespective of role, are all members of the CTI function maintaining regular situational awareness of new developments in the cyber threat landscape and can they articulate how various shifts in threats and trends can impact the organization?
Conclusion and Additional Freely Available Google Web-based Discoveries
Security assessments of any type involve challenges for both the customer and the third party if seeking an outside perspective. Understanding your current-state and end-state goals are equally important and if compliance requirements dictate a third-party review, you will have established an effective baseline for your organization. Consider taking an open and candid self-assessment using our free-of-charge ICD tool prior to signing up for a third-party intelligence assessment.
- Our hope is that organizations will leverage this freely available resource to baseline their CTI program maturity, better understand its current operational ability, and envision a path toward a more robust, intelligence-led security function.
Google Cloud’s Solution Center also hosts approximately a dozen other assessments designed to help organizations understand and improve their security posture, evaluate technology readiness, and aid in adoption of Google's technology solutions ranging from cloud computing to artificial intelligence.
One such assessment is the Security & Resilience Framework (SRF) that provides recommendations aligned with each functional area of the National Institutes of Standards and Technology (NIST) Cybersecurity Framework (CSF).
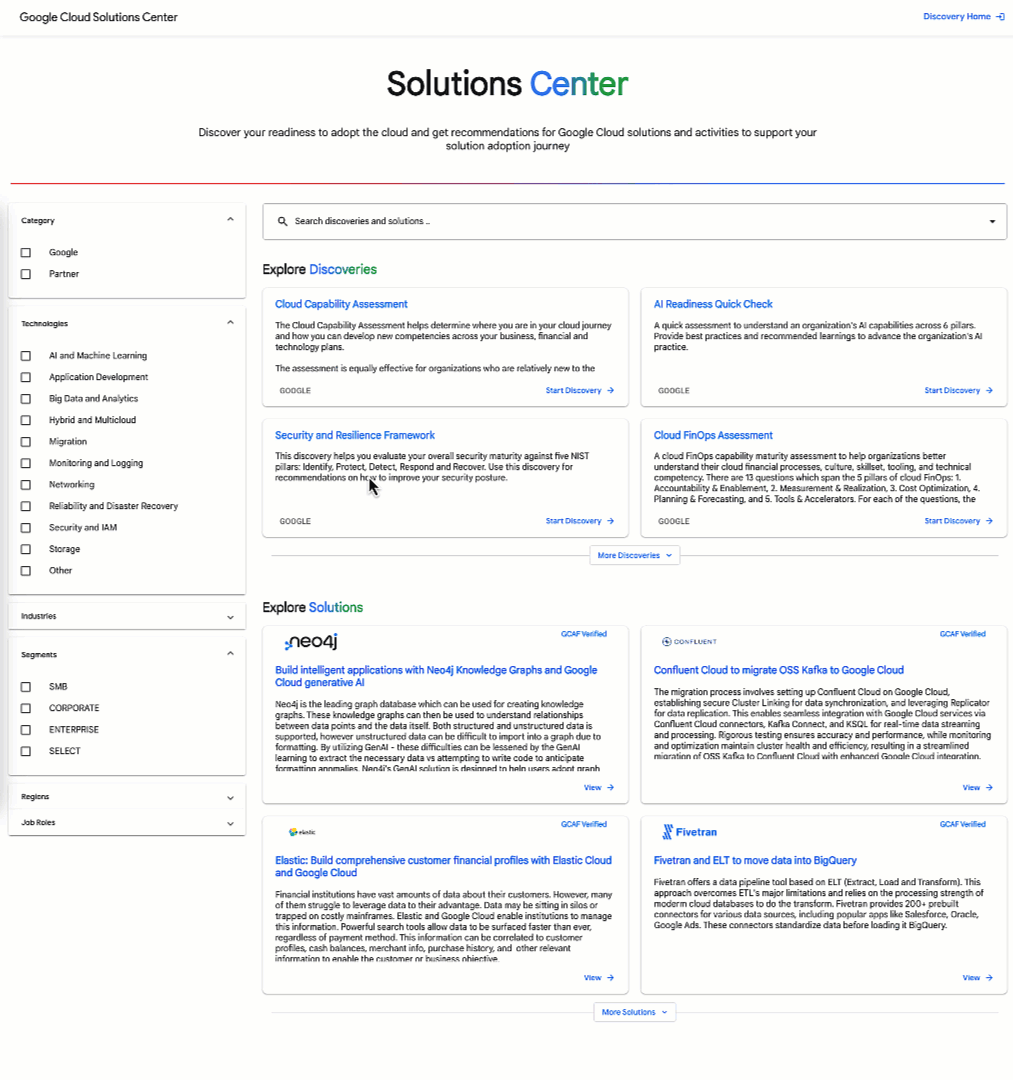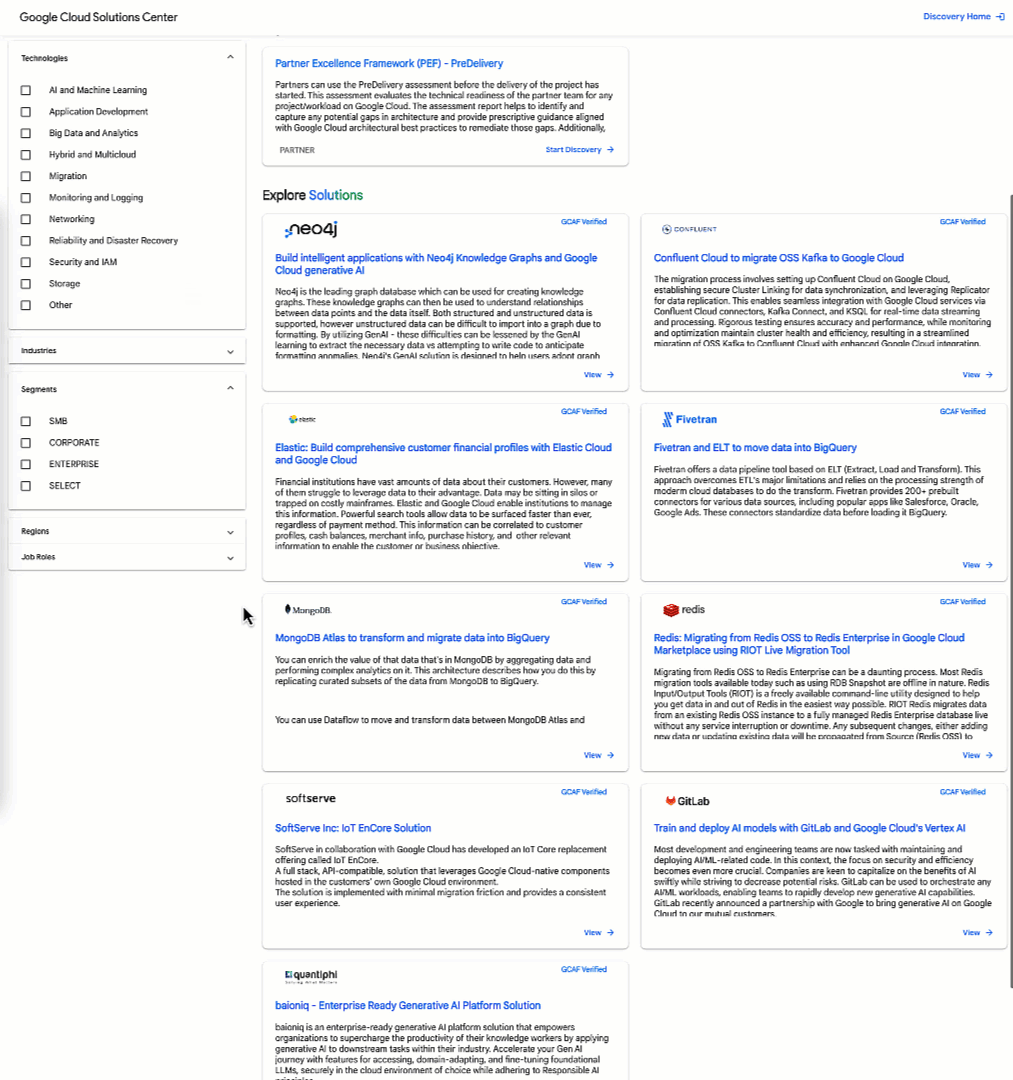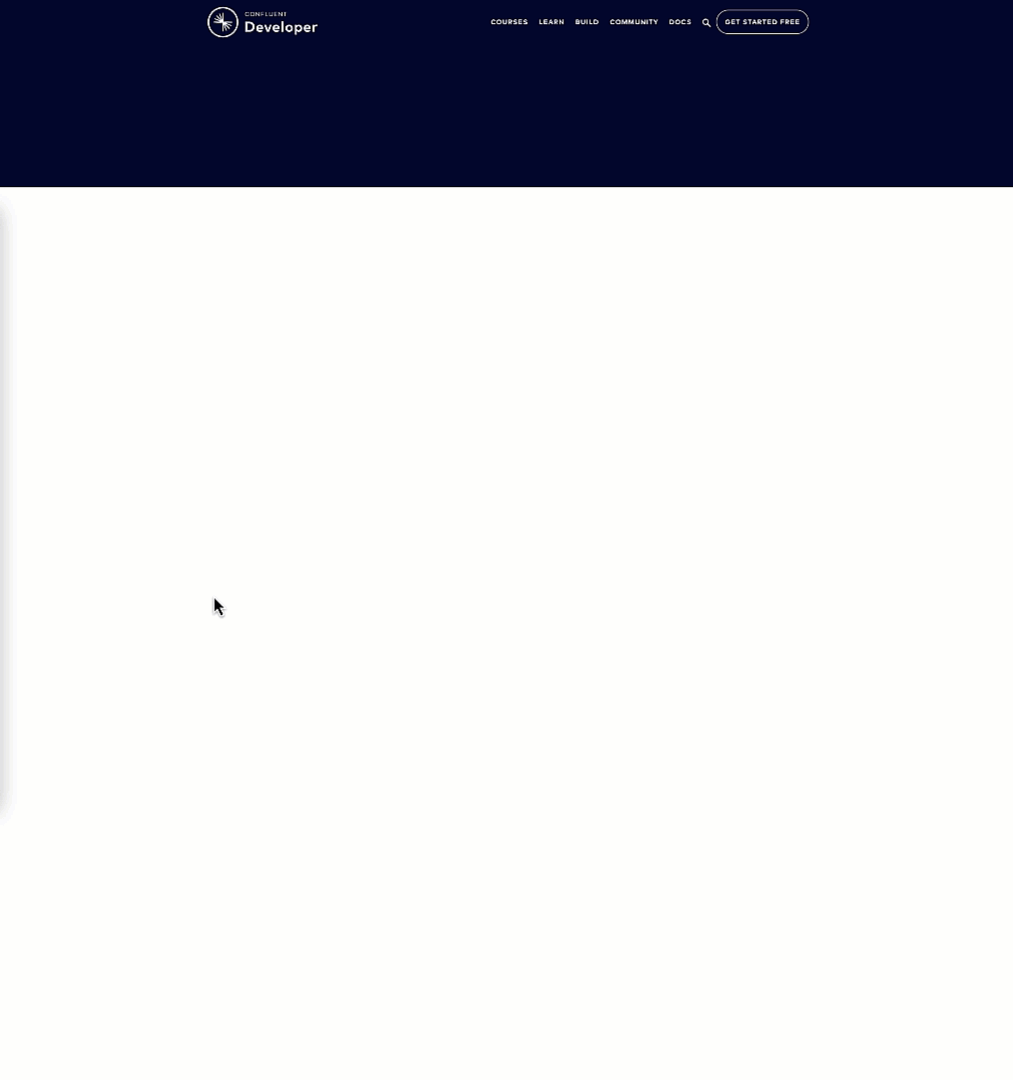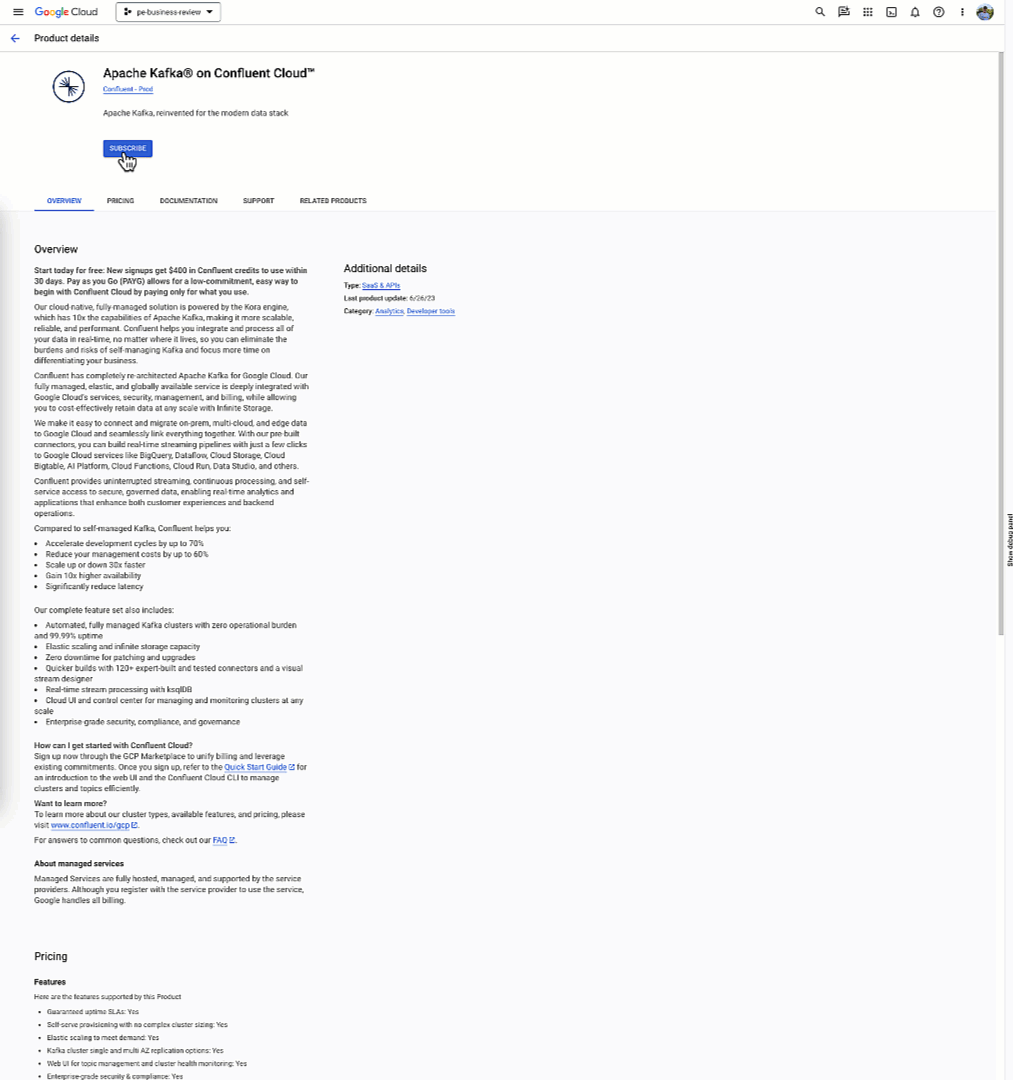
- This framework helps and enables our customers to assess risk, protect their businesses from threats, maintain continuous operations, and enable rapid recovery in the event of a crisis (ex) a ransomware incident).
We are proud to highlight one of the many areas Mandiant Intelligence and Google Cloud are collaborating on to improve user-centric products to security organizations around the world to further our mission of improving the overall state of cybersecurity for society.
