Decentralized Robbery: Dissecting the Nomad Bridge Hack and Following the Money
In this blog post, Mandiant takes a deeper look into how the Nomad bridge smart-contract was exploited and analyzes the on-chain transactions post-compromise using cybercrime prevention company Cyber Team Six’s (CT6) blockchain investigative software, CryptoVoyant.
Background
In early August 2022, the public observed yet another bridge attack, this time against the Nomad token bridge—a “bridge” allows interoperability between two blockchains and is further described in this post. In this case an update to the bridge’s smart contract led to a state where specially crafted transactions would be processed without proper validation.
Attacks against cryptocurrency bridges resulted in the theft of over $1.3 billion in 2022. Notable examples include the Ronin bridge attack in March 2022 (~600 million stolen), the Harmony bridge attack in June 2022 (~$100 million stolen), and the more recent Binance Smart Chain attack in October 2022 (~$568 million stolen).
Not only was this hack one of the largest with over $190 million siphoned out of the Nomad liquidity pool, making it one of the more sizeable decentralized-finance (DeFi) hacks in history, but also one of the most chaotic as the technique used to steal funds required little technical knowledge, resulting in a fury of cash-grabbing copycats once news of the exploit spread on social media (Figure 1).
Nomad put forth a bounty following this hack—the bounty allowed attackers to keep 10 percent of their funds and face no legal action if the other 90 percent was returned. Oh, plus a Whitehat non-fungible token (NFT) as a thank you (Figure 2). Ultimately $36 million of the $190 million stolen was returned.
Terminology Primer
Bridge
To best understand how the Nomad bridge was exploited, it is important to understand what a “bridge” is in the first place and why so many have been exploited.
Each blockchain is an independent network of nodes with their own native token, consensus mechanisms, programming languages, smart-contracts, and network rules. A “bridge” is a protocol (or set of rules) that allows multiple blockchain networks to interact with each other and for users to swap one token to another without having to trade in and out of tokens on an exchange and incur multiple trading fees.
Categorically, there are two types of bridges: custodial and non-custodial. Custodial bridges are controlled by a central entity while non-custodial bridges are considered more decentralized in that the handling of tokens is managed via a smart-contract and not a central organization. Essentially, a custodial bridge is as secure as the controlling organization, and a non-custodial bridge is as secure as its smart-contract's code.
Because bridges offer a means of interoperability between multiple separate blockchain networks, they must hold large amounts of all tokens associated with each blockchain it bridges—thus creating a massive liquidity pool and an enticing target for hackers, whether that pool is managed by a centralized custodian or a smart-contract.
Smart-Contract
You can think of a smart-contract as an account (like a bank account) controlled by code, and the code can have any number of logic decisions built-in that automate processes. Within a smart-contract there are various units called “functions” that can read or modify values within the smart-contract and/or perform a type of action.
Account Types, Transactions, and Messages
Within Ethereum there are two types of accounts: externally owned accounts (EOAs) that are controlled by an individual’s private key, and contract accounts (CAs) that are controlled by smart-contract code.
For a smart-contract code to execute it must receive either a message or a transaction. The difference between a message and a transaction is detailed within the official Ethereum white paper, and is such that a transaction is a digitally signed data package (generally financial in nature), and a message is like a transaction; however, it only exists within the Ethereum execution environment and is only generated by a CAs. This is relevant as the Nomad CA executed the sending of funds based on a flaw in how the smart-contract validated and processed those messages.
The Medium is the “Message”
According to their documents page, Nomad describes how the protocol leverages cross-chain transactions/messages to push data from one blockchain to another and how it relies on an “off-chain” agent called Updater for validating those messages (Figure 3).
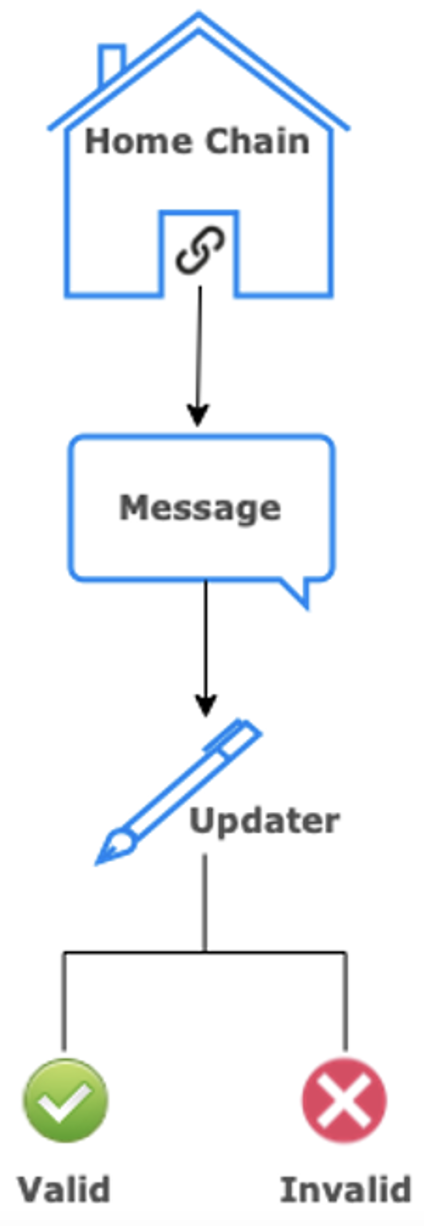
It is this off-chain Updater that is responsible for attesting the message data by checking for a valid root. According to the blockchain security firm Halborn: “In an upgrade to the protocol, Nomad decided to initialize the value of trusted roots to 0x00. While this is common practice, it also matches the value for an untrusted root, so all messages are automatically viewed as proven.”
Due to the aforementioned upgrade, since all transactions/messages with a root value of 0x00 were automatically viewed as proven, anyone could construct a transaction/message with that root value, call the process() function directly and have their transaction processed without being properly validated.
An Exploitive Transaction/Message
An Ethereum transaction contains a field called “data,” (Figure 4) and typically when a transaction interacts with a smart contract, the data inside this field is able to call specific functions within the smart contract it is interacting with.
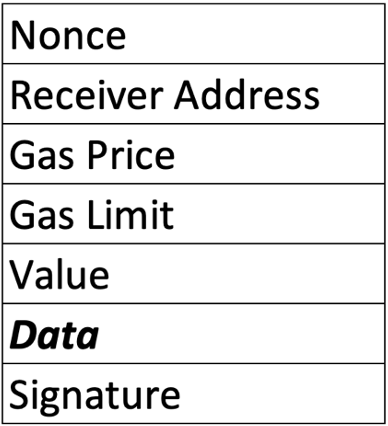
It is in this field where attackers call the process() function directly, replace the recipient address with their own, and broadcast the new transaction. An example of one such malicious transaction can be seen on Etherscan, and the input data is shown in Figure 5.
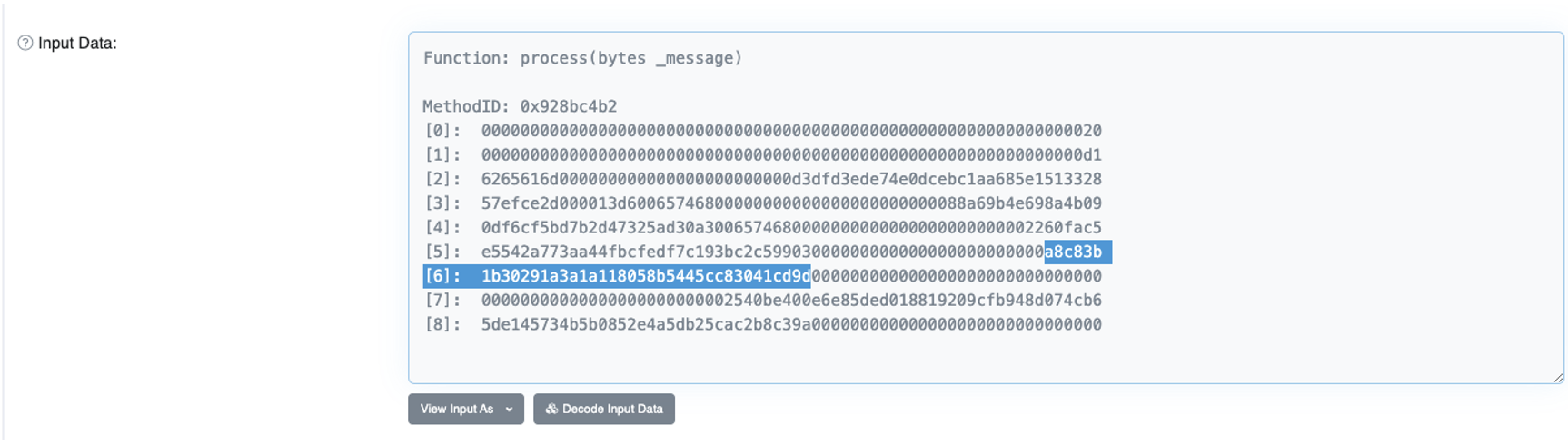
In a detailed analysis of the attack, published by Coinbase, their report stated: “While writing a PoC we found it curious that attackers chose to extract funds in smaller increments when they could have drained the whole amount in a single transaction. This is likely due to the attackers not crafting bridge messages from scratch, but instead replaying existing transactions with patched receiving addresses.”
On-Chain Analysis
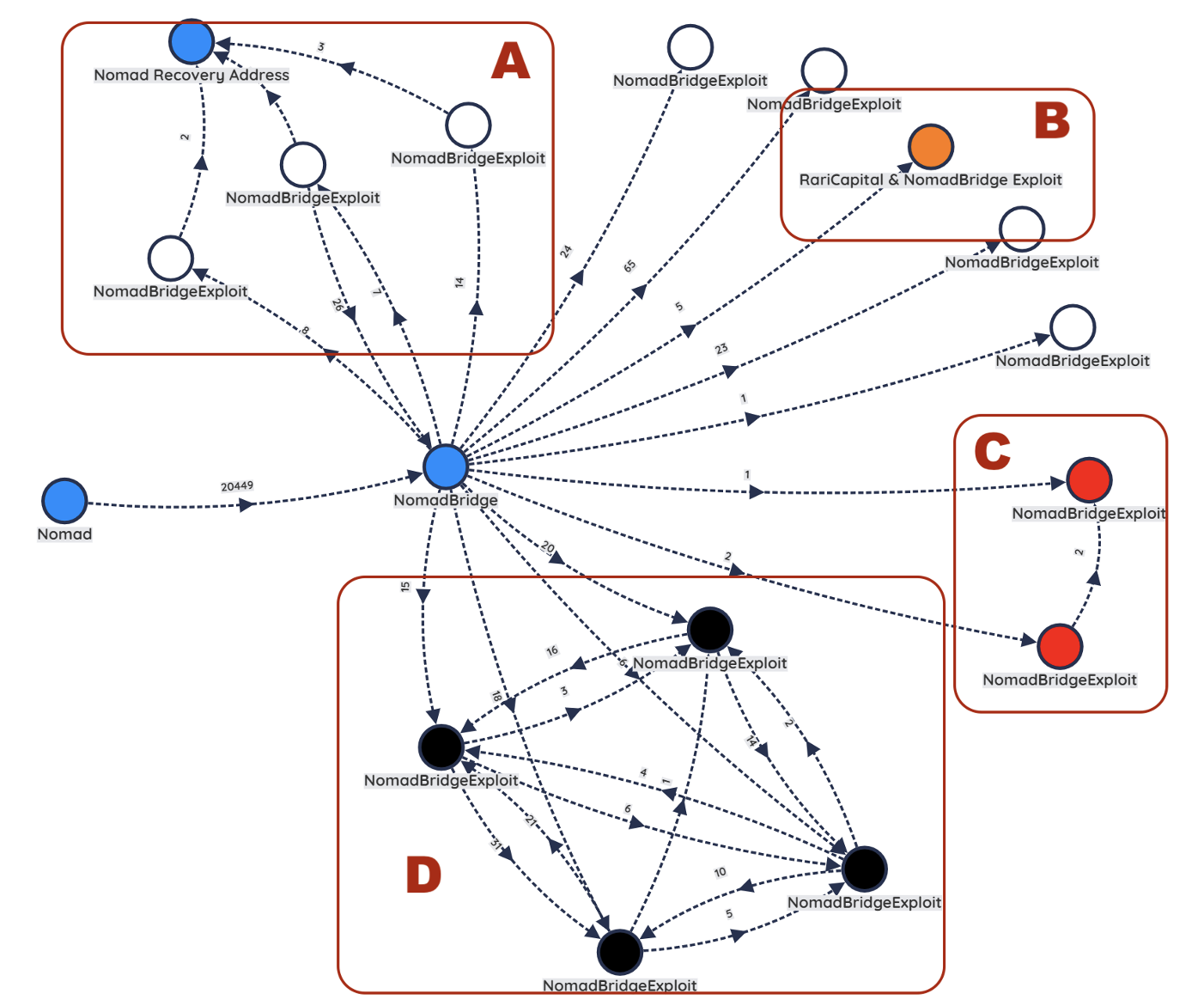
During this analysis, Mandiant partnered with the cybercrime prevention company CT6 to analyze the on-chain transaction patterns post-compromise. With the use of their blockchain investigative software, CryptoVoyant, we were able to identify four distinct clusters within the list of addresses that stole over $2 million USD worth of tokens from the Nomad bridge. Our findings are as follows:
- 14 addresses each stole over $2,000,000 USD
- 22 addresses each stole between $1,000,000 and $2,000,000 USD
- 281 addresses each stole between $100,000 and $1,000,000 USD
- 215 addresses each stole between $1,000 and $100,000 USD
The Over 2 Million Club
During a deep dive into the 14 addresses that stole over $2 million, four distinct groups of addresses were identified (Figure 6).
Group A
Group A consists of three addresses (represented in white) that each returned some amount of the stolen funds to the Nomad recovery address (Figure 7).
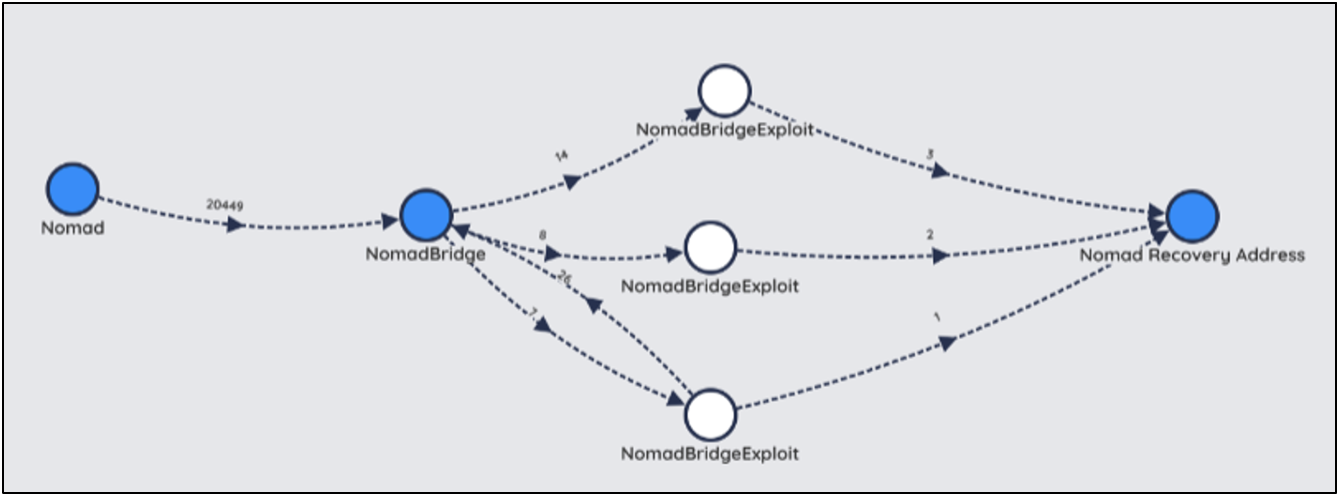
However, of the three addresses, only one address returned a significant portion of the stolen funds (77.6%) while the other two only returned 1.7% and 3.4% respectively (Table 1).
| Approximate Amount Stolen | Approximate Amount Returned | Percentage Returned |
| $9,918,000 | $164,000 | 1.7% |
| $4,782,000 | $164,000 | 3.4% |
| $4,122,000 | $3,710,000 | 77.6% |
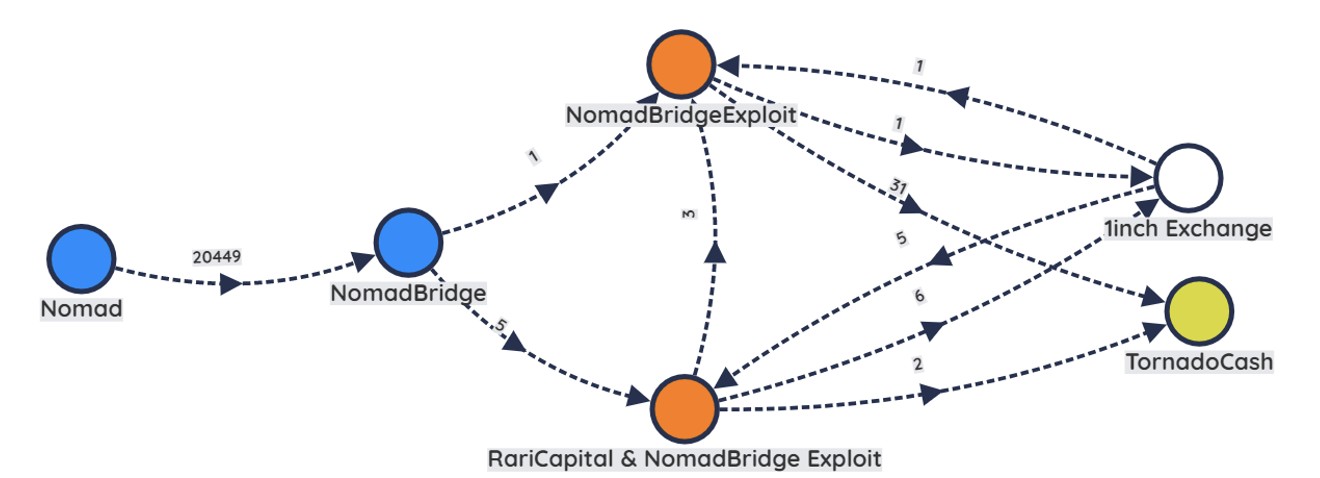
Group B
Of the two address belonging to Group B (represented in orange), one is also associated with the Rari Capital Exploit that occurred back in April 2022, indicating this actor/group has experience in exploiting smart-contracts for financial gain. This actor/group stole approximately $4,015,000 USD worth of tokens, leveraged the DeFi exchange 1inch to swap into other tokens, and then proceeded to send the funds through TornadoCash to further obfuscate the funds (Figure 8).
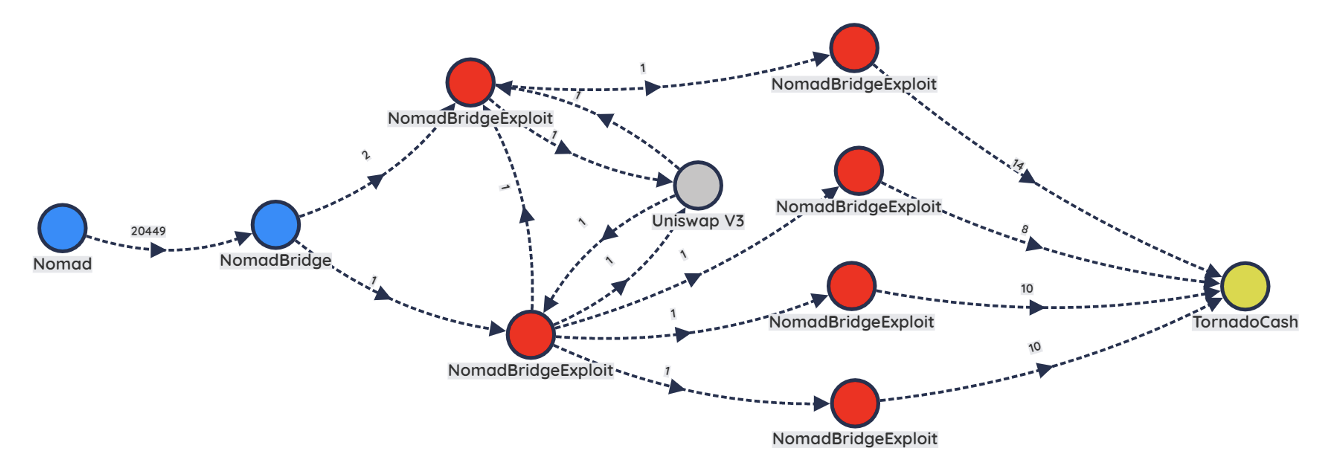
Group C
We assess with moderate confidence that the addresses in Group C (represented in red) belong to the same actor(s). This actor/group stole roughly $5,203,000 USD worth of tokens, and the on-chain analysis proves those funds were sent to Uniswap, most likely to exchange for different tokens, and then funneled through the TornadoCash mixer to help obfuscate their origins (Figure 9).
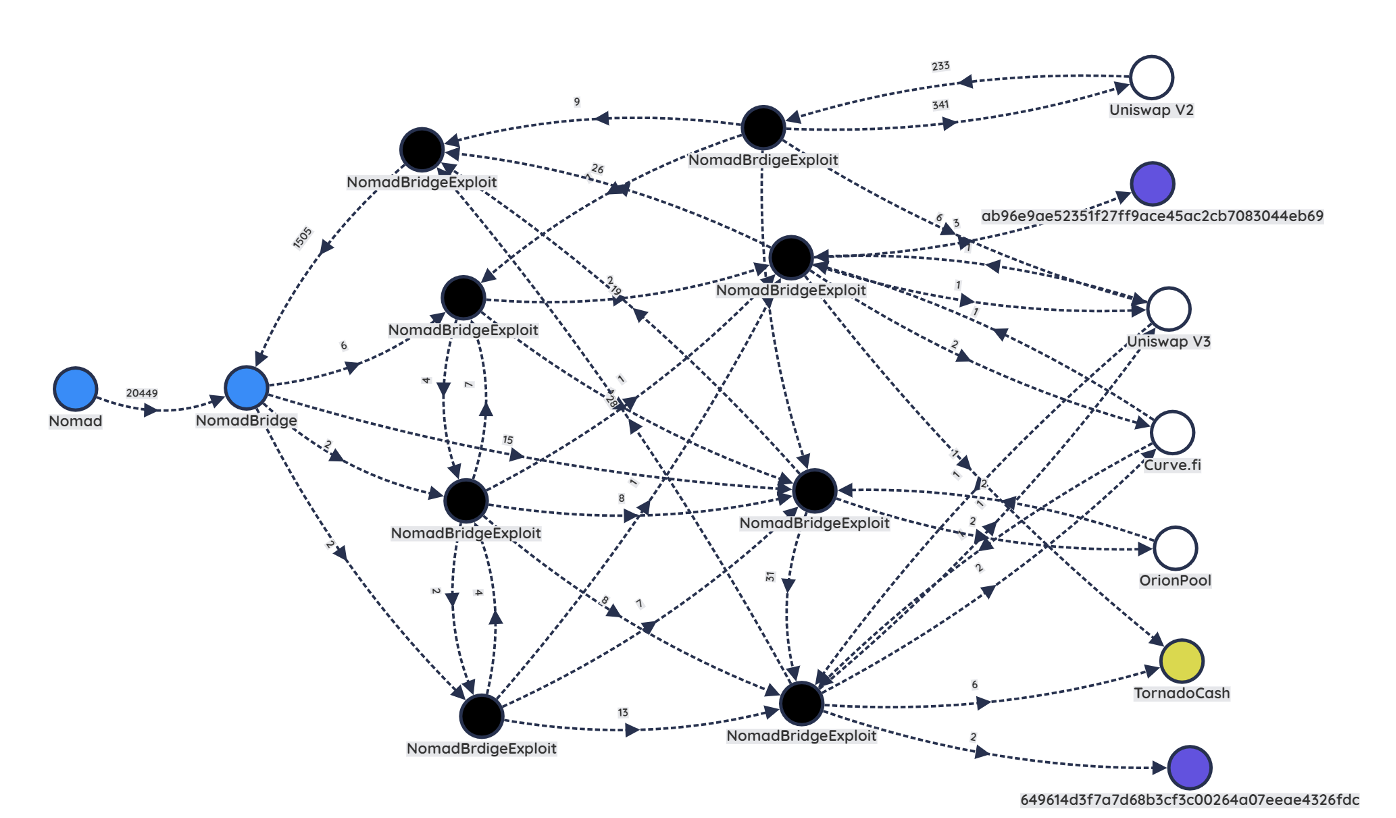
Group D
We assess with high confidence that the addresses belonging to Group D (represented in black) belong to the same actor/group (Figure 10), and the amount stolen from the Nomad bridge totals around $54,506,000 in USD value at the time of analysis. The on-chain analysis shows the actor/group leveraging several decentralized swapping pools (liquidity pools found on decentralized exchanges used for token swapping), specifically, OrionPool, Uniswap, and Curve, to exchange the stolen funds for other tokens. The actor/group then sends some funds through TornadoCash and some into two separate deposit addresses (represented in purple). Out of the roughly $54 million stolen in the heist, approximately $50 million reside across the two purple deposit addresses.
Conclusion
In a world with over 20,000 cryptocurrency tokens, bridge protocols play a crucial role in facilitating interoperability between these networks and in doing so, create a lucrative target for threat actors. This is evident by the fact that nearly $2 billion has been stolen from these cross-chain protocols in 2022 alone.
The speed at which money flows in cryptocurrency networks is part of its appeal, as the traditional finance system moves much slower and has higher Know Your Customer (KYC) standards. However, this speed of transaction and lower compliance standard is what aids threat actors to steal, move the money quickly, and in many cases, allows for the obfuscation of stolen funds, therefore easing the conversion to fiat currency (e.g. Rubbles, Yuan, Dollars, etc.), other tokens, or tangible assets within minutes or hours. While on-chain analysis is helpful at proving the path illicit funds take post-compromise, services such as mixers, DeFi swap pools, and non-KYC exchanges present a challenge to security researchers, law enforcement, and governments.
As this innovative sector continues to grow, Mandiant assesses with high confidence that bridge protocols will continue to be an attractive target for threat actors for the foreseeable future, and we recommend any organization or developer(s) working to design such a protocol to perform extensive security auditing prior to and during operation, while continuously assessing the on-chain transactional risk.
