SEC Cybersecurity Disclosure Regulations: 7 Essential Steps to Prepare Your Whole Organization for a Cyber Incident
**Register today for our live webinar on October 31 at 12pm ET - SEC Cybersecurity Rule Compliance Through Effective Disclosure Controls
On July 26, 2023, the U.S. Securities & Exchange Commission (SEC) adopted a new rule (“rule” or “regulations”) enhancing disclosure requirements regarding cybersecurity readiness and incident reporting for publicly traded companies (“registrants”). The rule also requires foreign private issuers to make comparable disclosures.
The rule is intended to benefit investors by providing more timely and consistent disclosures about material cybersecurity incidents, and by providing consistent and easily accessible information around cybersecurity risk management, strategy, and governance practices.
These regulatory changes will impact how registrants communicate essential information through a cyber incident. Every organization impacted by the rule should evaluate both their technical and organizational incident response plans with the new reporting requirements in mind.
What are the SEC Rule Changes?
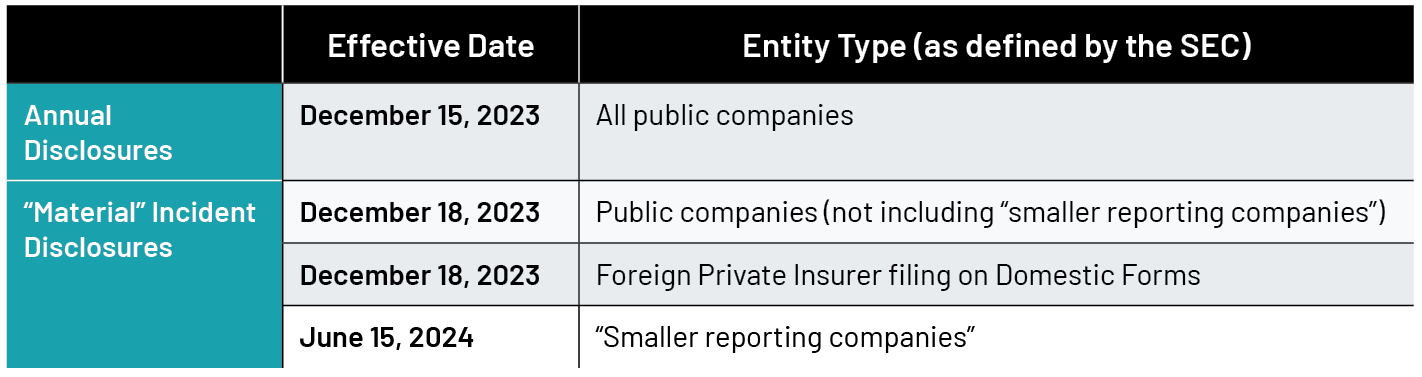
The rule requires registrants to disclose — within four business days — cybersecurity incidents that are deemed “material.” Although the SEC did not define “material,” it notes aspects of materiality include “nature, scope, and timing, as well as its material impact or reasonably likely material impact on the registrant. The SEC recognized it can take time for a company to determine whether an incident is “material”, which can affect the timing of the mandatory disclosure. There is a national security and public safety exemption to the four-day reporting requirement where registrants can delay immediate disclosure of material incidents by obtaining approval from the U.S. Attorney General who would then notify the SEC in writing.
The new rule also requires that registrants annually disclose their processes for assessing, identifying, and managing material risks or likely material risks from cybersecurity threats and previous incidents. Additionally, registrants must disclose relevant expertise of any members of management or committees that are responsible for assessing and managing registrants’ material cybersecurity risks and describe board oversight of such risks and threats.
Is Your Organization Ready to Respond to the Rule?
When a cyber incident occurs, organizations need to be ready and able to respond quickly. Foundational to an effective response is a comprehensive cyber incident response plan matched with a detailed governance, risk, and compliance program. Having such plans and processes in place help organizations manage cyber incidents in an efficient, agile, and cohesive way. The new rule puts a premium on having a comprehensive response plan because it can potentially change how forensics, legal, and communications teams work during an incident. Organizations should take steps now to ensure they are ready to comply with the SEC rule.
When Do the Rule Changes Go Into Effect?
How Can My Organization Prepare?
- Ensure you have a clear and cohesive cybersecurity response strategy
Organizations should ensure that a cybersecurity governance and response strategy is well-defined, aligned to best practices, and includes capabilities to empower effective security decision making to identify, assess, and mitigate cybersecurity risks. These capabilities should also include channels for effective and transparent reporting of measurements and metrics to relevant executives and business stakeholders around cyber risks that could have financial, operational, or reputational impacts.
- Review and enhance your cybersecurity risk management program and processes
Having a well-defined cyber security risk management program is a foundational pillar to an overarching enterprise-wide risk program and will enable an organization to quickly validate when incidents may lead to a material impact requiring disclosure.
An established cyber risk program enables an organization to make decisions by balancing business impact with risk considerations such as asset loss, business disruption, and the ability to restore operations if critical systems are adversely impacted. Key activities that organizations should consider in their cyber risk planning include understanding their threat profile, high value assets, dependencies on third party partners, and the ability to detect and respond to threats that could lead to an incident that could materially affect their operations.
- Identify the “Crown Jewels”
Critical to assessing material impact are identifying and evaluating the assets most valuable to an organization, which are attractive targets for malicious actors. A clear understanding of the assets and information that matter most to the business and its customers — the “Crown Jewels” — will help both inform materiality determinations and bring precision and prioritization to areas of highest criticality. When identifying your Crown Jewels, we often recommend enriching asset information with an understanding of not only business significance, but also the value of the asset to an attacker, incident history, and both upstream and downstream system dependencies.
- Review and update your plans, playbooks, and documentation
To support an organization’s cyber defense and risk management program, operational capabilities are a natural place to start. By understanding and aligning the systems and data most critical to your organization (i.e., Crown Jewels) to incident response plans, playbooks, and governance documentation, organizations are best positioning themselves for a better outcome to an incident and their ability to comply with the new SEC reporting requirements. Successful compliance will require preparedness on multiple fronts.
As with any SEC regulatory updates, there are also significant legal considerations. To support operational resilience during and after an incident, organizations should consider establishing both incident response and legal retainers. This will provide external legal support to supplement an organization’s own capabilities and offer additional resources that increase the probability of success through an incident and alignment with the SEC’s reporting and disclosure requirements.
- Test your organization’s operational readiness for cybersecurity incidents
Companies should also test their response plans through tabletop exercises before an incident occurs to identify and address any gaps that may impede their ability to comply with the new regulations (e.g., the ability to determine materiality, report within four business days, or file for a reporting exemption). There are different types of tabletop exercises to help measure the breadth and depth of an organization’s processes and capabilities including executive, technical, operational, and board-level exercises. Organizations should include representation from across business units in their exercises to ensure appropriate representation and surface and minimize the risk of process, communication, and ownership collisions across teams during an incident.
Additionally, a Red Team Assessment is one of the best ways to test your security program, people, and technology. “Red teaming” is a realistic, “no-holds-barred” (though non-destructive) attack scenario in your environment that is guided by engagement objectives designed similar to a targeted attacker’s mission objectives. By using advanced attack techniques learned by observing real attackers and targeting your most critical assets, the security specialists will test the organization’s ability to prevent, recognize, and respond while also identifying gaps in your network and security architecture configurations.
- Map your stakeholders and communication channels
A critical aspect of a successful enterprise-wide cybersecurity incident response plan is a comprehensive communications plan that will govern the process of creating content and distributing updates to key stakeholders. Companies need to ensure they are ready to communicate about an incident internally and externally. Failure to have such a plan runs the risk of inconsistent messaging and potential compliance issues with the SEC. For example, without a coordinated plan, messaging could become splintered, or some audiences could receive different information than what was disclosed to the SEC.
- Identify your ecosystem of responding partners
When a cyber incident occurs, there is an ecosystem of external partners that assist with various aspects of the organizational response. The responding partners vary by organization and the nature of the incident, but commonly include:
- Legal
- Insurance
- Forensics
- Communications
- Extortion/Ransomware Negotiators
While not directly involved with the incident working group, it is a best practice to have data discovery and credit monitoring vendors identified and ready to help with various phases of the investigation and response.
It is important to identify these partner relationships prior to an incident and establish how to work together during an event. If possible, partners that will be directly involved with the response should be included in preparation activities like tabletop exercises. Organizations should also ensure that they have up to date contact information and processes captured in incident response plans and playbooks.
One additional consideration, it is advisable for partner retainers to include a Service Level Agreement (SLA) to ensure you have access to your partners’ services during an incident. While many partners offer “no up-front cost” retainers, during times of high attacker activity — such as we’ve seen multiple times this year with high-volume attacks against multiple file transfer services — incident response partners can quickly reach capacity and clients with SLAs are given priority.
For public companies this is a critical time and an opportunity to build out their cyber response strategies before they are faced with an actual incident. Companies cannot effectively enhance cyber crisis processes as an incident is ongoing. By following these steps and proactively investing in cybersecurity preparedness, an organization can mitigate risk, comply with the SEC, and promote trust and resilience.
Resources
