Keeping up with CONTI
Evaluate your ability to prevent CONTI and other ransomware threats with Mandiant Advantage Ransomware Defense Validation
CONTI ransomware recently made headlines after pledging support for the Russian government and threatening retaliatory attacks against the critical infrastructure of any nation responsible for cyber-attacks impacting Russia. This resulted in the subsequent leak of source code and private communications between actors involved in CONTI and adjacent operations. Victims are still appearing on the CONTI data leak site indicating that at least some actors have continued their operations. Mandiant Threat Intelligence rereleased a report on these operations, describing the tactics, techniques, and procedures (TTPs) seen across intrusions attributed to actors that have deployed CONTI ransomware.
Keeping up with CONTI: Tactics, Techniques and Procedures Associated with CONTI Ransomware Deployment
Mandiant Advantage Threat Intelligence Report, March 16, 2022, 06:45.00 PM, Version 3
While we have not observed CONTI ransomware advertised in underground forums, we have high confidence that threat actors deploying CONTI commonly partner with other actors who provide initial access resulting in a variety of initial access vectors. These have included malicious emails delivering EMOTET, TRICKBOT, and ICEDID, as well as the exploitation of Microsoft Exchange vulnerabilities. Actors associated with CONTI operations have also commonly sought to purchase VPN credentials on underground forums. After obtaining access, threat actors have relied on various publicly available and legitimate tools to facilitate earlier stages of the attack lifecycle before deploying CONTI ransomware, most commonly using batch scripts and PsExec.
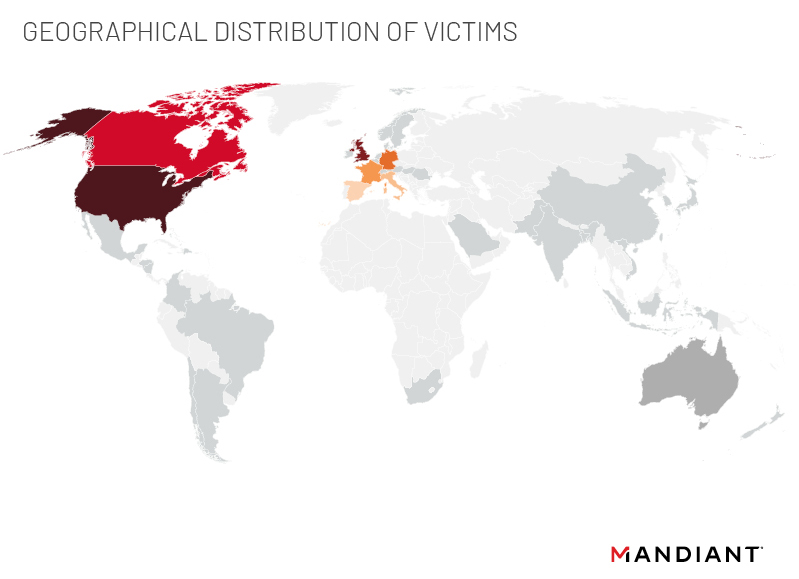
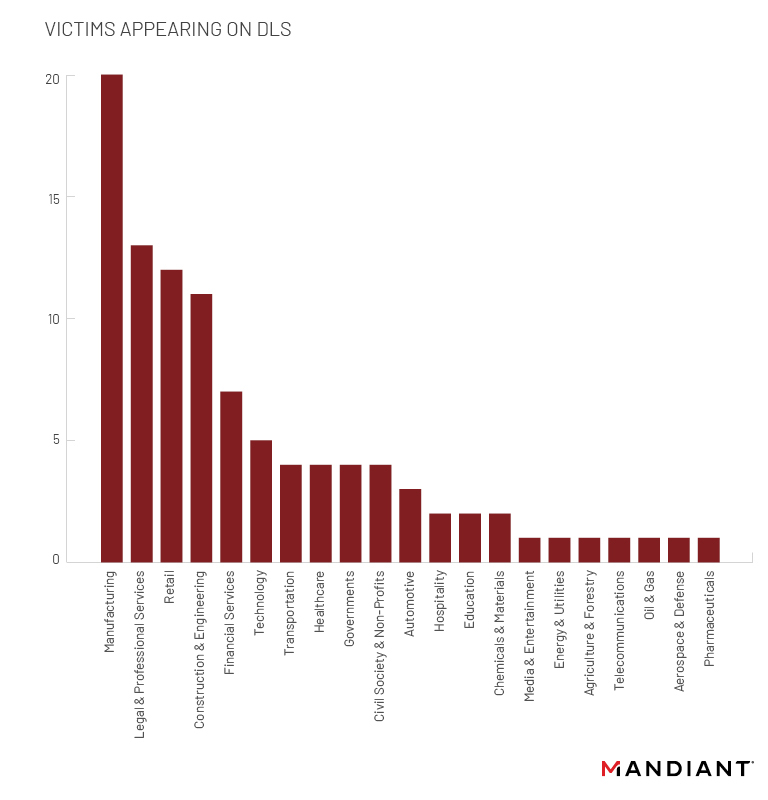
Of the nearly 800 organizations appearing on its data leak site, CONTI victims have been based mostly in the manufacturing, legal and professional services, construction and engineering, and retail sectors. The actors deploying CONTI may have a targeting preference for North America. More than 60 percent of victims are located in North America, but a total of 40 countries in total have been impacted (Figure 4 and 5).
Safely test your ability to prevent against CONTI. Get a demo of Mandiant Advantage Ransomware Defense Validation.
