Introducing the Mandiant Cyber Threat Intelligence (CTI) Analyst Core Competencies Framework
Mandiant Intelligence consultants are regularly asked by customers what the optimal team composition is when starting and maturing a cyber threat intelligence (CTI) program. While the question may seem straightforward, the answer is complex and often requires several layers of unpacking. For instance, the proper team composition across knowledge, skills, and abilities (KSAs) should align with the CTI program’s current mission, vision, and goals and where it sees itself evolving in the near-to-mid-term. Once determined, key performance indicators (KPIs) and CTI-centric metrics can support resource prioritization decisions surrounding recruitment and talent retention, data and tool procurement, stakeholder outreach, and other dimensions, which we covered in our previous blog post on the “balanced scorecard approach”.
Mandiant’s Intelligence Services (MIS) group has more than a decade of experience building industry-leading CTI capabilities. Our experts work with organizations across numerous industry verticals around the world to effectively adopt and integrate CTI into their operational environments. Throughout the years we have observed many changes in the threat landscape and in customers CTI maturity, however, despite the CTI discipline evolving considerably over the same time frame, we observed very little work done to identify requisite KSAs for CTI analysts. At its core, advancements in information and communication technology (ICT), the evolution of cyber security technology, and the subsequent shift in cyber adversaries’ use of cyber operations and tradecraft have expanded the breadth and depth KSAs requirements for CTI analysts.
To fill a much-needed gap, Mandiant decided to do the heavy lifting and developed The Mandiant Cyber Threat Intelligence (CTI) Analyst Core Competencies Framework to help grow the pool of highly capable practitioners.
The Mandiant Cyber Threat Intelligence (CTI) Analyst Core Competencies Framework has three primary goals:
- Empower organizations to identify areas for team or individual growth, determine appropriate development roadmaps, and align internal, external, or on-the-job training opportunities to ensure CTI skills progression.
- Provide a guidepost for aspirant CTI analysts to tailor their studies.
- Assist network defenders in understanding the roles and responsibilities of a CTI analyst to improve collaboration between disciplines.
The framework (as represented in Figure 1) groups competencies into four foundational pillars: Problem Solving, Professional Effectiveness, Technical Literacy, and Cyber Threat Proficiency. Each competency is then broken out into one or more series of skills with some competencies more prescriptive than others.
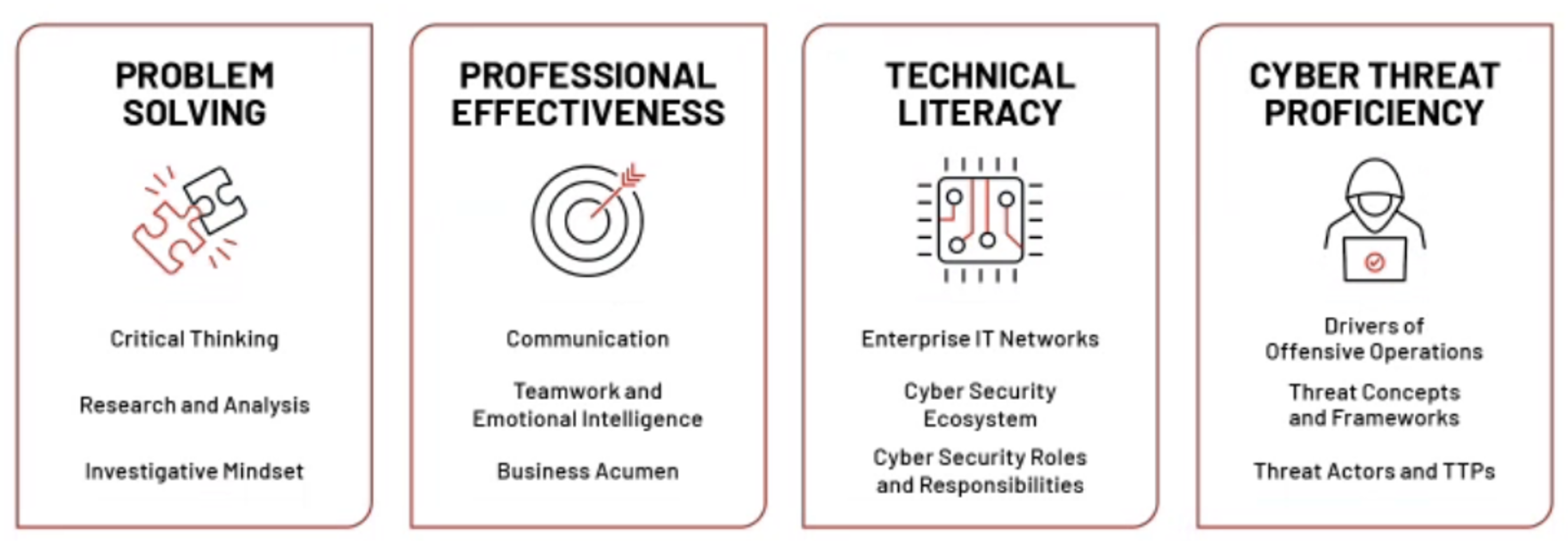
A CTI analyst’s role, responsibilities, experience, education, and training will largely dictate the analyst’s depth in each competency. Not all analysts need to be rockstars across every competency; their job roles will dictate areas where advanced proficiency is required. For example, a technical analyst whose role largely focuses on extracting intelligence from malware to produce high fidelity indicators of compromise (IOCs) to write detection signatures will require above average skills in Technical Literacy and Cyber Threat Proficiency competencies. It is worth nothing that some competencies take more time to develop than others due fundamental prerequisite knowledge and experience.
At Mandiant, we group our analysts into two camps–technical or strategic–and, in understanding the complimentary nature of both roles, we strive to pair an analyst of each type to work together when producing finished intelligence assessments on threat activity, actor intent, relative capability, or potential impact. Ideal candidates are strong in both the technical and strategic skills, although many analysts frequently have more depth and preference operating in one role over the other.
- For our technical analysts, we require a thorough understanding of adversary cyber operations and tradecraft, forensic artifacts, malware and network traffic analysis, operational infrastructure, and the ability to develop detection signatures, amongst other skills.
- Our strategic threat analysts, on the other hand, are required to have a thorough understanding about threat actors, motivations, how cyber operations are used to achieve national objectives consistent with geopolitical aspirations, and operational trends, amongst other skills. Strategic analysts have a heavier focus on traditional intelligence analysis tradecraft.
Download The Mandiant Cyber Threat Intelligence (CTI) Analyst Core Competencies Framework today.
Acknowledgements
We would like to thank Joe Slowik, Jake Williams, Andreas Sfakianakis, Tom Winston, Katie Nickels, and Jorge Orchilles for reviewing the framework, providing creative input, and helping ensure it reflects today’s realities in the CTI discipline. Additional thanks to the several Mandiant employees that kindly lent an ear to soundboard the framework’s development. Lastly, this framework would not have been possible without the excellent work done by the Intelligence and National Security Alliance (INSA) in 2015 and Carnegie Mellon University in 2012 to create seminal steppingstones from which this framework expounds upon.
